According to its official documentation, "twitter-server" is a Twitter OSS project used to provide a template from which servers at Twitter are built. It provides common application components such as an administrative HTTP server, tracing, stats, and more, and is used, amongst other things, by both the Finagle and Finatra frameworks.
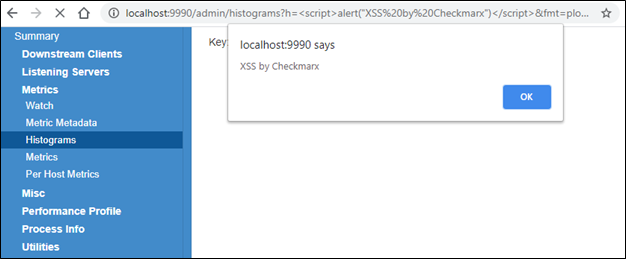
After researching twitter-server, the Checkmarx Security Research Team discovered a reflected cross-site scripting (XSS) vulnerability, assigned CVE-2020-35774, that exists in the administration panel of twitter-server in the “histograms” component.
CVSS Score
CVSS: 3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N Score: 6.1 (Medium)Impact Summary
Successful exploitation of the vulnerability could have allowed attackers to retrieve information presented in the twitter-server admin dashboard web-application, and potentially access additional functionality, such as shutting down the server or services. However, overall impact would be determined by functionality exposed by the specific twitter-server instance’s admin panel.Description
An XSS vulnerability exists in "twitter-server" in the "h" GET parameter in /admin/histograms, when the "fmt" parameter is set to either "plot_cdf" or "plot_pdf." Note that this webpage is only available, and vulnerable, if the “finagle-stats” dependency is included, either on its own or via other dependencies such as Finatra.Proof-of-Concept
1. Create basic twitter-server instance by following the guide here. 2. Add “finagle-stats” dependency to project to enable histograms tab.- Can be added explicitly - e.g. in build.sbt - libraryDependencies += "com.twitter" %% "finagle-stats" % "20.10.0"
- Implicitly as part of the finatra-http dependency - e.g. in build.sbt – libraryDependencies += "com.twitter" %% "finatra-http" % "20.10.0

Vulnerability Analysis
A quick manual analysis shows the tainted flow in code is quite clear:- Request matches /admin/histograms - https://github.com/twitter/twitter-server/blob/develop/server/src/main/scala/com/twitter/server/handler/HistogramQueryHandler.scala#L353
- “fmt” parameter is either “plot_pdf” or “plot_cdf” which renders HTML response - https://github.com/twitter/twitter-server/blob/develop/server/src/main/scala/com/twitter/server/handler/HistogramQueryHandler.scala#L357
- Response content type is set to HTML - https://github.com/twitter/twitter-server/blob/develop/server/src/main/scala/com/twitter/server/handler/HistogramQueryHandler.scala#L278
- “h” GET parameter, as value of the “query” variable, is rendered into the string "Key: $query is not a valid histogram.", which is returned as raw HTML https://github.com/twitter/twitter-server/blob/develop/server/src/main/scala/com/twitter/server/handler/HistogramQueryHandler.scala#L283
Timeline of Disclosure
- Oct 29, 2020 – Disclosure via HackerOne
- Oct 30, 2020 – Issue acknowledged by Twitter
- Nov 10, 2020 – Fix committed
- Dec 11, 2020 – Fixed version released
- Dec 29, 2020 – CVE-2020-35744 assigned
- Jan 6, 2021 – Public disclosure






