
A Cascade of Errors
When I wrote Delphi code, I had to compile code into binaries to run on Windows. The compiler wouldn’t produce a binary unless my code was semantically correct. If the code was semantically correct, but had potential logic errors, the compiler would issue warnings. My team always had an ironclad rule that we should never commit code with warnings. (There were also hints that resulted from semantically correct, but syntactically meaningless, code. We also never wanted to check-in code with hints…)
Sometimes a compilation would result in many, many warnings. A quick examination would usually reveal the reason and making one fix in one spot would often resolve all the warnings.
A similar thing can happen with security vulnerabilities in your code. Sometimes, when doing a Static Analysis Security Testing (SAST) scan, you can get a ton of (seemingly) unrelated errors. You might look at that and think “Sweet Baby Elvis, this is going to take a long time to fix!” But fear not – our Static Application Security Testing (SAST) tool can make it easier for you to clear those errors as quickly as possible.
The Best Place
Very often, a single change to your code can cause many of the vulnerabilities in your code to go away. But it’s finding that spot in your code can often be the challenge.
Checkmarx SAST has a feature called “Best Fix Location,” or BFL for short. The BFL is designed to find that “one fix, many vulnerabilities disappear” spot in your code. As part of the scanning process, our SAST will process our code analysis, and then try to find the very best place to fix any given alert. Very often, that remediates the root problem for many other issues.
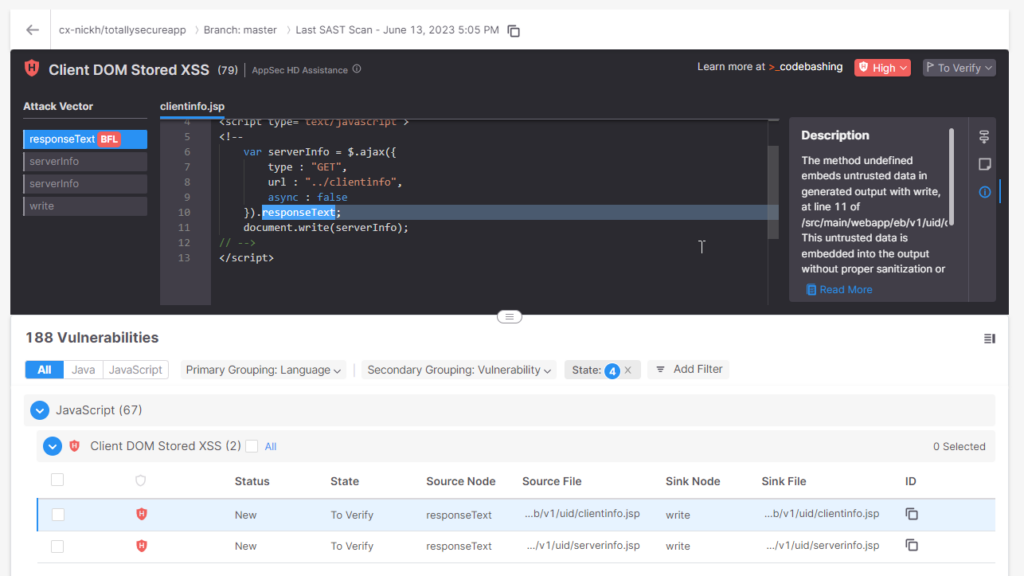
Above, you can see the Checkmarx One interface showing an alert in some JavaScript code that could lead to a DOM Stored Cross-site Scripting attack. This is a common problem that has an easy solution. Sometimes, it can be difficult to figure out the best place to start.
In the upper right, you can see links to a chain of attack vectors – places that a malicious actor might try to place script code into your application. The bottom link is the line of code “closest to the surface”, and each line above it digs in a little deeper.
The top one, the fourth in the call stack, is the Best Fix Location. It is the spot in the code that is the “root of the problem.” Make a correction there, and it is likely that other vulnerabilities that use that code at a “higher” point in the code will go away as well.
In this case, we can see that the responseText property will allow malicious users to be able to place unsanitized code into our page, leaving our application open to attack.
How This All Works
Our SAST tools do something that is called “Data Flow Analysis.” Data Flow Analysis focuses on how data flows through the application, showing how data is passed between different statements or blocks of code. It tracks the relationship between different variables, expressions, and operators in a particular program, and how they are used to compute values or change data. Our solution uses this information to find vulnerabilities in your code.
Data Flow Analysis is much more resource intensive than some other solutions that use Regular Expressions or other ways of analyzing code. This trade-off is worth it though, because Data Flow Analysis is a deep and thorough examination of not merely the code, but the way the code works.
Getting It Fixed
Now you know where the problem lies. But we don’t abandon you there. We will point you to resources that will help you understand what the risk is, why it is a risk, and how to make the risk go away.
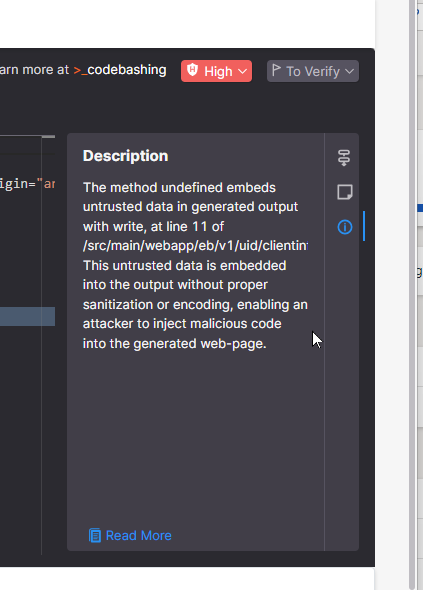
On the right is a quick description of what the vulnerability is. You will be able to continue to learn more about the vulnerability by following the “Read More” link. There you will be given a complete description of the issue, including code examples of the problem occurring and recommended solutions. In addition, we point you to resources within our CodeBashing training solution that can give you even more information.
Once you understand the issue, we make it simple for you to remediate it. You know your codebase, and so you know the best way to move forward with this alert. Maybe it looks like a problem, but it isn’t. Maybe it is a problem and needs to be fixed in due course. Or maybe it needs to be fixed immediately. You can use the dashboard to give the issue a label to make sure that it will be dealt with properly, and so that it will receive the correct level of attention.
So far, we’ve been looking at all of this in the Checkmarx One Dashboard. But if you are a developer, you can do all of what we talked about here right inside your IDE. We have plugin support for VS Code, Visual Studio, JetBrains Ultimate, and Eclipse. Our plugins let you run SAST scans to see, process, and fix alerts without leaving your tool of choice.
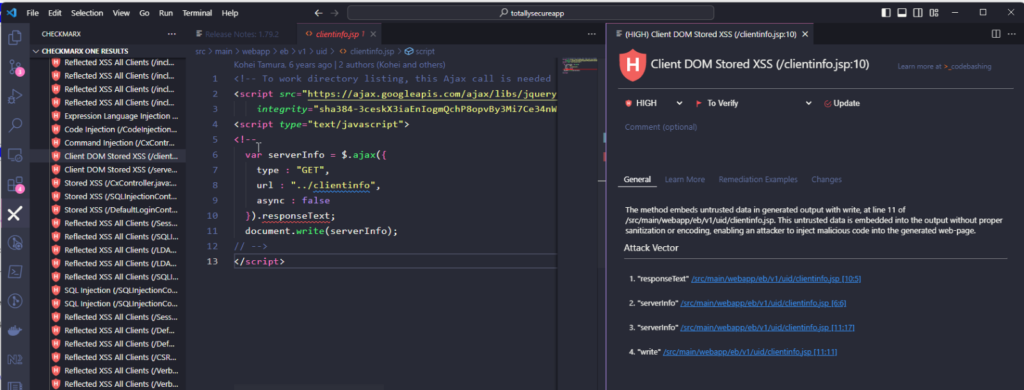
Hunting down the location of the problem is often the biggest time-sink in dealing with a code security alert. Not having to even do the search is a huge productivity boost. Getting all the information about the problem and advice on how to fix it is the icing on the cake.
In the end, the Best Fix Location feature will give you everything you need to make quick work of problems in your code.