Through an integration with Sysdig, Checkmarx One users can now leverage runtime container insights to prioritize vulnerabilities associated with running container packages that pose the most risk.
Prefer not to read? You can watch a replay of our joint webinar where we go into more depth about the capabilities and demonstrate live within the Checkmarx One and Sysdig Secure products. Watch now ->
In the past several years containers have emerged as a favorable choice for deploying applications, due to their architecture they allow developers to overlook concerns about dependencies and environments. Everything essential for running an application is neatly encapsulated within the container, encompassing code, runtime, system tools, libraries, and dependencies.
In cloud-native environments, containers, when coupled with best practices and the appropriate tools, offer seamless scalability, ensuring optimal application performance and availability. This flexibility not only caters to peak demands but also frees processing power for various application components.
However, the challenge arises when cloud and application security functions operate in silos, creating fragmentation. This scenario leaves AppSec teams without the correlation or context to understand which container packages are running, which are not and prioritize associated risks effectively.
Imagine a scenario where developers, prompted by security alerts and new work items, invest their valuable time in remediation efforts, only to discover that the identified low-priority vulnerability pertains to an unused container package. Without the correlation between vulnerability and runtime data, frustration sets in for developers, and may cause alert fatigue, while AppSec teams find themselves handicapped without a comprehensive view of the critical vulnerabilities that truly matter.
The challenge for AppSec teams is not merely identifying vulnerabilities but prioritizing, and remediating the ones that pose the most risk. Establishing a connection between vulnerabilities and the running containers becomes crucial, enabling teams to prioritize critical vulnerabilities and remediating them effectively. This correlation goes beyond technical nuances; it forms the backbone for fostering trust and collaboration between developers and AppSec teams.
Checkmarx & Sysdig; connecting the dots between pre-production and runtime
Sysdig enhances Checkmarx Container Security by providing vital runtime insights into container Open-Source Software (OSS) running within cloud-native environments. While Checkmarx excels in securing container images by detecting vulnerabilities during development, Sysdig’s real-time profiling enriches this process by analyzing containerized applications during runtime. Checkmarx crossmatches the list of OSS packages used at runtime with known vulnerable packages, enhancing the identification of security risks. By integrating with Sysdig, Checkmarx extends its container security capabilities beyond static image analysis, ensuring a comprehensive approach throughout the container lifecycle.
The collaboration between Sysdig and Checkmarx streamlines overall security management by offering continuous runtime monitoring and analysis. Sysdig’s integration enhances Checkmarx’ ability to prioritize and address vulnerabilities effectively, delivering a unified solution covering static analysis and real-time package insights. This partnership strengthens the capability to identify and remediate security threats, fostering a resilient cloud-native environment while empowering security teams and developers with a more proactive security posture.
See the integration in action
Beginning in Checkmarx Container security, we look at the completed scans under the “Container” tab.
Runtime insights for container packages are available at the container level and at the vulnerability level.
Within the container level under the “Container Packages” tab, container scan results are sorted by default by the packages used at runtime, and by the packages with the most vulnerabilities.
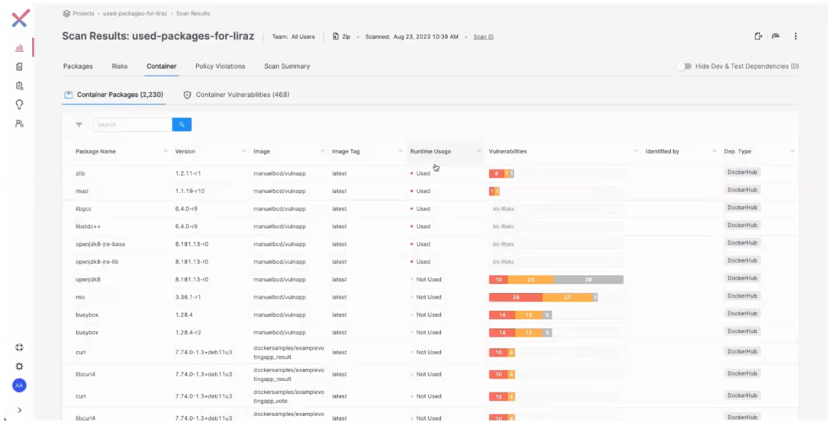
In this view, you can easily see how easy it is to quickly jump in and tackle the container packages with the most vulnerabilities. But when users quickly cross reference the “Runtime Usage” column alongside the number of vulnerabilities found, it becomes clear which vulnerabilities should be prioritized.
Users can also filter this view to only see the packages used at runtime.
Runtime insights are also available at the vulnerability level. The ‘Container Vulnerabilities’ view displays vulnerabilities associated with containers and their criticality, bubbling up those vulnerabilities associated with containers found in runtime at the top of the list.
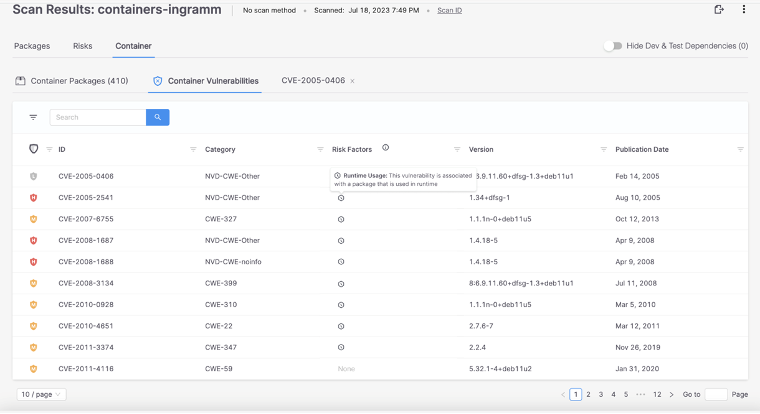
In this view, you’ll see that the “Risk Factor” column highlights whether the vulnerability is associated with a package that is used at runtime. The results show 9 CVEs that are associated with a package used in runtime, and the last CVE was not within a package used in runtime. The risk factor of whether the vulnerability was associated with a package found in runtime is just the start; additional risk factors are coming soon.
When users want to better understand a given vulnerability found, they can click into the CVE for more information, including the severity, CVSS Score, and attack vector.
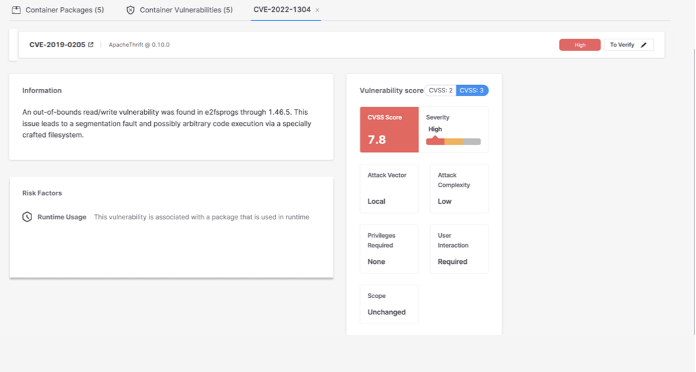
When users click into a given CVE, they’ll now see a new “Risk Factors” box, where they can quickly see that the vulnerability is associated with a package used in runtime.
Prioritize what’s running and reduce noise by up to 90%
Using runtime insights from Sysdig Secure, Checkmarx One or SCA standalone customers gain several benefits.
- They can effectively prioritize remediation. Correlating pre-production and runtime surfaces the most impactful risk, dramatically reducing the time to detect and prioritize vulnerabilities associated with in-use packages first.
- Build #DevSecTrust. Team alignment and trust are crucial for the success of an enterprise-scale AppSec program. Focusing their development team on the most critical vulnerabilities and filtering out the rest while reducing alert fatigue, builds trust with developers.
- Improve your security posture. Runtime insights aid organizations in increasing their overall security posture, by providing the context your team needs to prioritize the most impactful vulnerabilities.
- Reduce noise. AppSec teams can prioritize vulnerabilities based on in-use context, and eliminate 90%
Whether you’re a CISO (Chief Information Security Officer) focused on your total application security posture, or part of an AppSec team focused on identifying and prioritizing vulnerabilities, or a developer focused on remediation and supporting the business where it matters most, Checkmarx and Sysdig help you better identify, prioritize, and remediate vulnerability risk.
The integration is available for users of both Checkmarx One or Checkmarx SCA standalone and Sysdig Secure. For current customers of both Checkmarx and Sysdig, or you wish to start gathering runtime insights Request a Demo, to get started.
You can also watch a replay of our joint demonstration https://info.checkmarx.com/tech-partner/sysdig/bridging-code-and-cloud-security