
Unveiling the Latest NPM Ecosystem Threat: Thousands of SPAM Packages Flood the Network, A New Discovery by Checkmarx
What Happened?
- A sudden surge of thousands of SPAM packages were uploaded to the NPM open-source ecosystem from multiple user accounts within hours.
- Further investigation uncovered a recurring attack method, in which cyber attackers utilize spamming techniques to flood the open-source ecosystem with packages that include links to phishing campaigns in their README.md files.
- The packages were created using automated processes, with project descriptions and auto-generated names that closely resembled one another.
- The Attackers referred to retail websites using referral IDs, thus profiting from the referral rewards they earned.
- The packages appeared to contain the very same automation code used to generate these packages, probably uploaded by mistake by the attacker.
- As first recognized in this tweet by Jesse Mitchell, the generating scripts also include valid credentials used by the attacker in the attack flow.
NPM Anomalies
Our technology collects and indexes evidence related to packages from all open-source ecosystems, allowing us to query historical data for new insights.
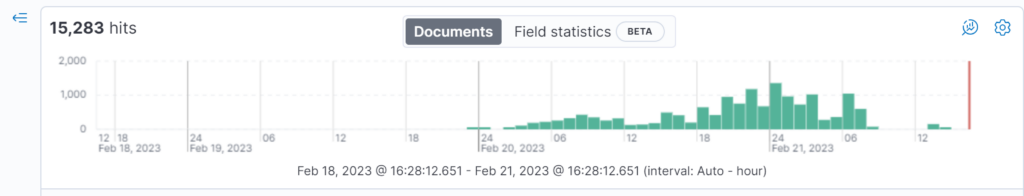
On Monday, 20th of February, Checkmarx Labs discovered an anomaly in the NPM ecosystem when we cross-referenced new information with our databases. Clusters of packages had been published in large quantities to the NPM package manager. Further investigation revealed that the packages were part of a trending new attack vector, with attackers spamming the open-source ecosystem with packages containing links to phishing campaigns. We reported on a similar attack last December.
In this situation, it seems that automated processes were used to create over 15,000 packages in NPM and related user accounts. The descriptions for these packages contained links to phishing campaigns. Our team alerted the NPM security team.
Phishing Sites in Package Description
The attackers used a large number of packages with names related to hacking, cheats, and free resources to promote their phishing campaign. Some of the package names included “free-tiktok-followers,” “free-xbox-codes,” and “instagram-followers-free”. These names were designed to lure users into downloading the packages and clicking on the links to the phishing sites.
The descriptions of all the packages we found contained links to phishing sites.
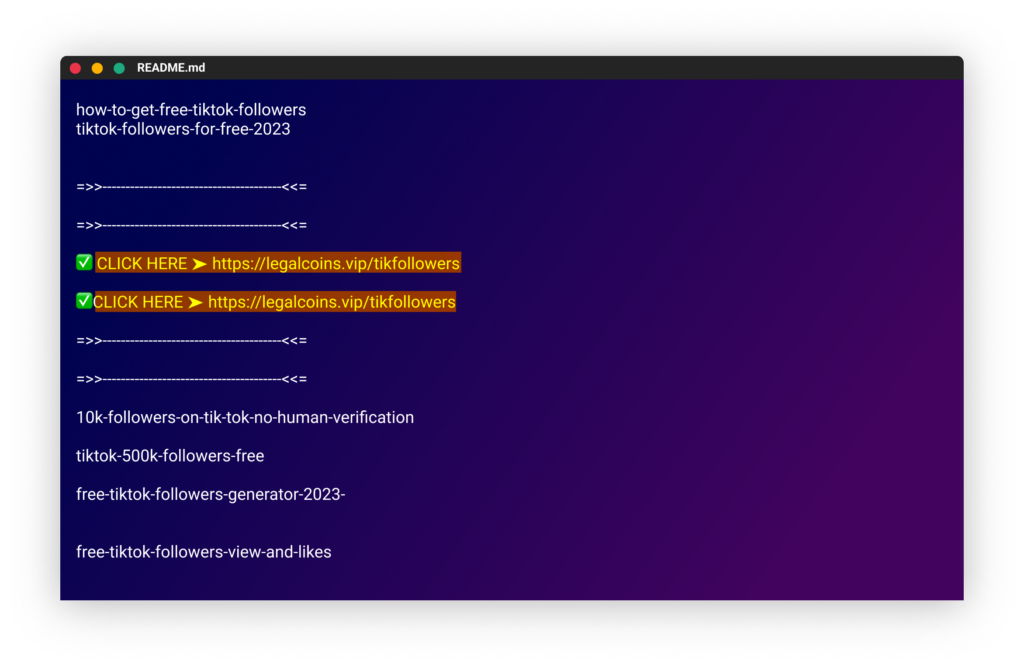
The messages in these packages attempt to entice readers into clicking links with promises of game cheats, free resources, and increased followers and likes on social media platforms like TikTok and Instagram.
The phishing campaign linked to many unique URLs across many domains, with each domain hosting multiple phishing webpages under different paths. The deceptive webpages are well-designed and, in some cases, even include fake interactive chats that appear to show users receiving the game cheats or followers they were promised.
These chats will even respond to messages if the reader chooses to participate, but these are all automated and fabricated. This highlights the need for caution when interacting with links in packages and the importance of only using trusted sources.
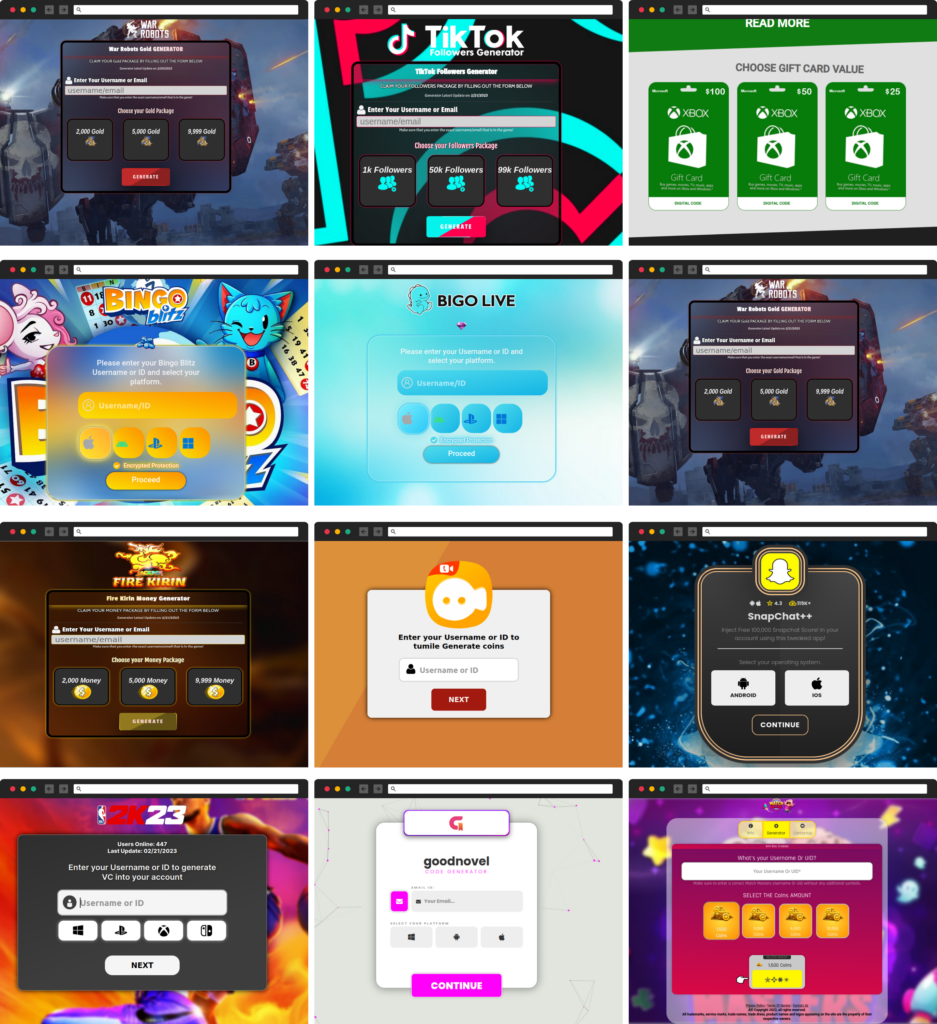
The websites included built-in fake flow that pretended to process data and generate the promised “gifts.” However, this process most of the time failed, and the victim was then asked to enter a “human verification” phase that involved multiple sites referring the user from one to another. These sites included surveys that asked the user to respond to various questions, leading to additional surveys or eventually to legitimate eCommerce websites. This shows the importance of being cautious when interacting with links in packages and only using trusted sources.

Referrals Rewards
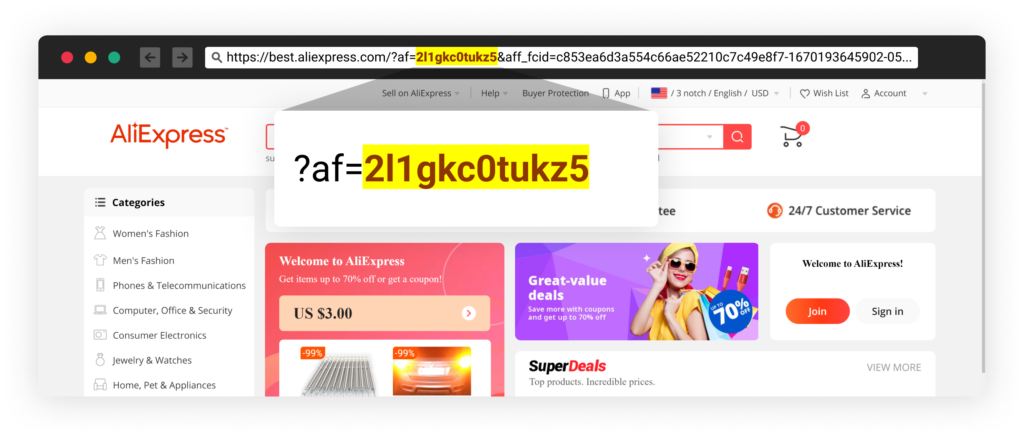
While investigating the phishing websites, we noticed that some of them redirected to eCommerce websites with referral IDs. For example, one of our experiments resulted in being redirected to AliExpress, one of the world’s largest online retail platforms. Like many other retail websites, AliExpress offers a referral program that rewards members for referring new customers to the platform. If the threat actors refer their victims to AliExpress and they make a purchase, the threat actors’ account will receive a referral reward in the form of a coupon or store credit. This highlights the potential financial gain for threat actors who engage in phishing campaigns like this one.
Did the Attacker make a mistake?
Throughout many of the packages we found similar python scripts with similar functions that seemed to be the ones automatically generating and publishing the spam packages. Other than that, we found other “helper.txt” files that seemed to also be a part of the automated mechanism. The most interesting file is a python script within the NPM packages that includes all steps of the package publication.
The flow of the Python script are as follows:
- Defines folder paths containing configuration files.
- In some cases defines a list of website URLs and their login credentials (which later uses to publish there the link of the uploaded package).
- Loops through the folder paths and read configuration files to get a domain name and keyword.
- Generates random titles and descriptions using the configuration files.
- Generates a random link for new content using the title along with a random number.
- Creates the following files: index.js, package.json, and README.md based on templates and modifies them to include the new link and titles.
- Uploads the new package to NPM using the npm publish command.
- Checks if the upload was successful and writes the URL to a file.
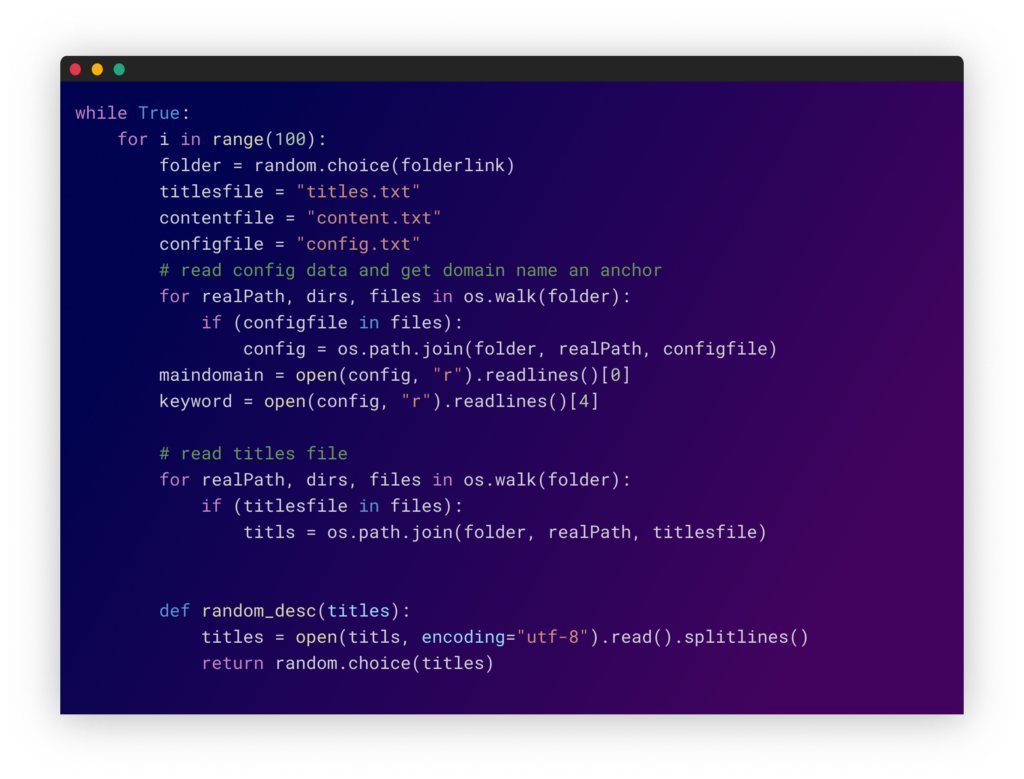
Generating random content for new NPM packages
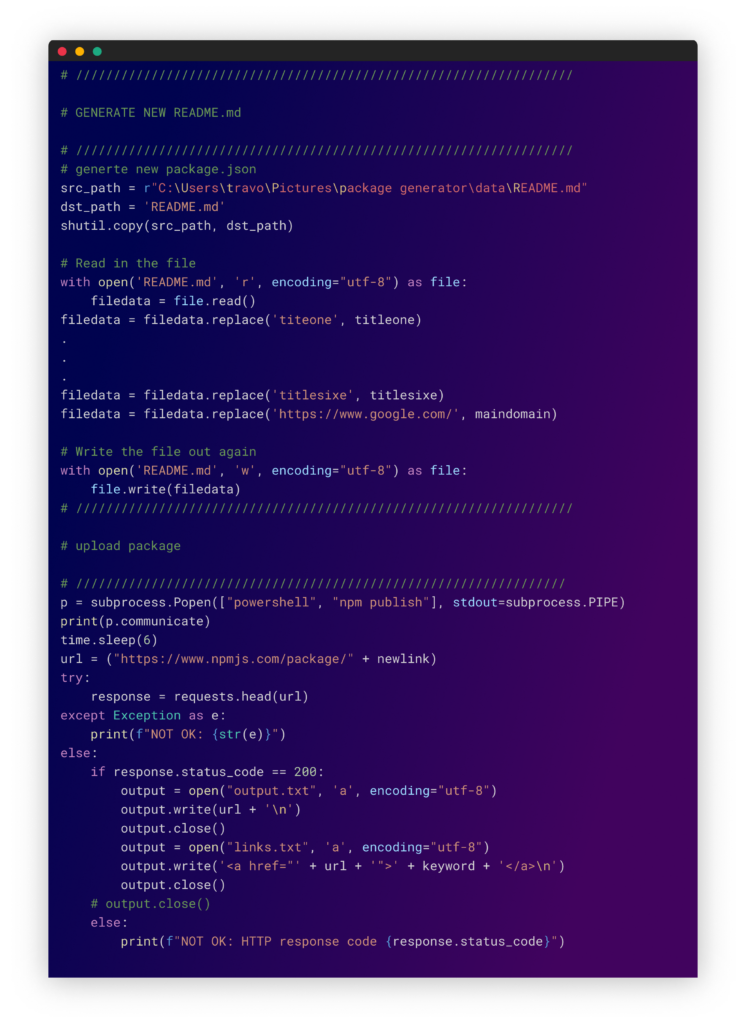
Generating package files and publishing to NPM
After completing the publication of all packages in the current batch, the attacker goes on to the last automated task.
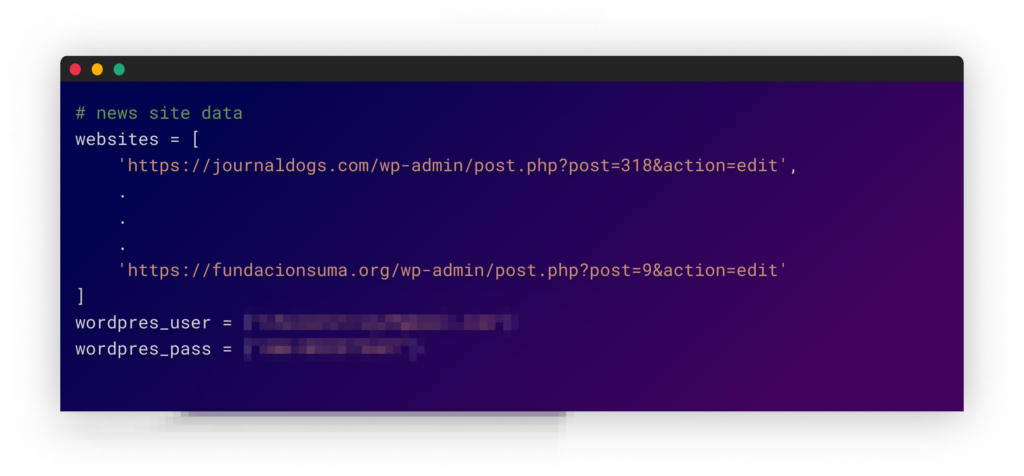
From what we see thus far, the attacker created or at least has access to several news-like websites in which they can publish content.
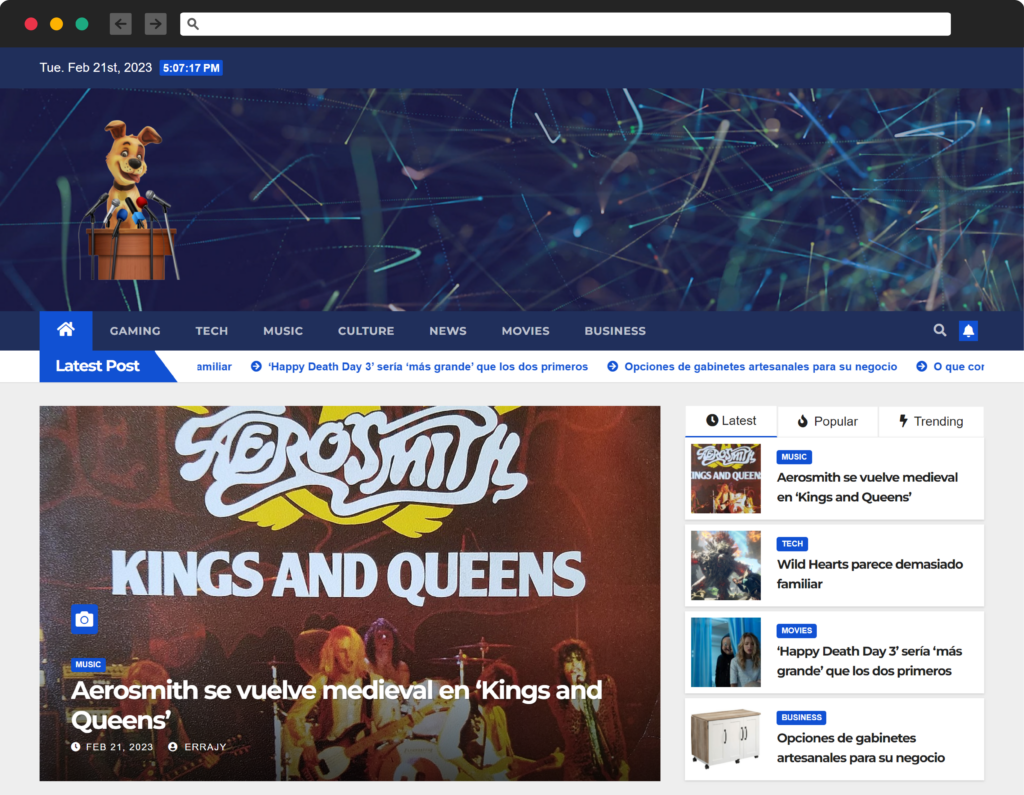
The last task in the python scripts is appending links to unrelated posts in these new-like websites. These links direct to the webpages of the packages they published on NPM’s website.
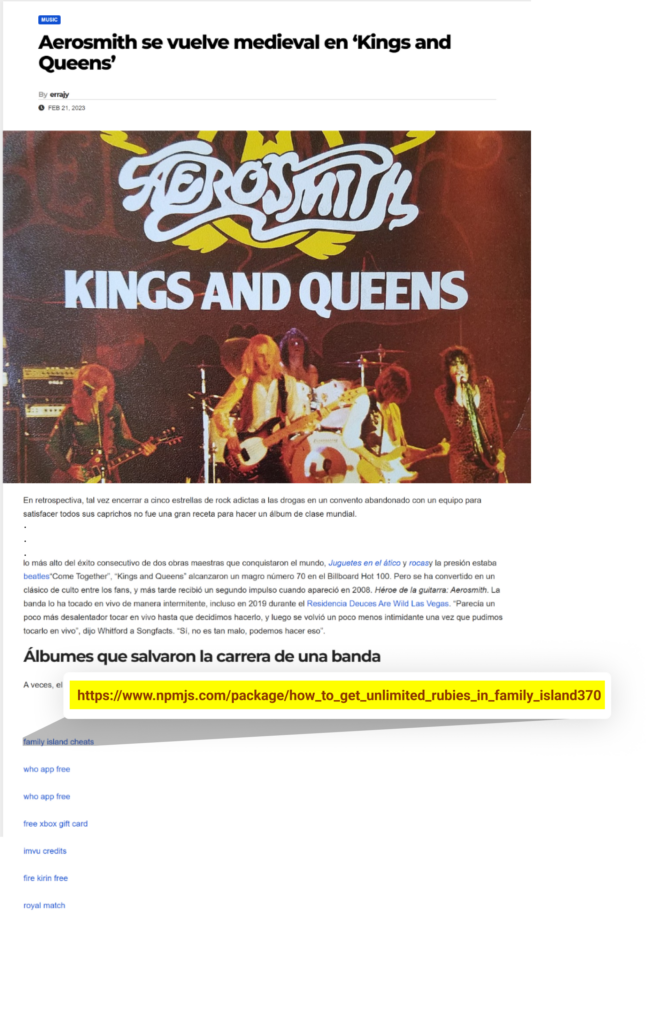
To do that, the attacker uses the “selenium” python package to interact with these wordpress websites. First, they need to authenticate as an editor, and only then continue to post the package’s links.
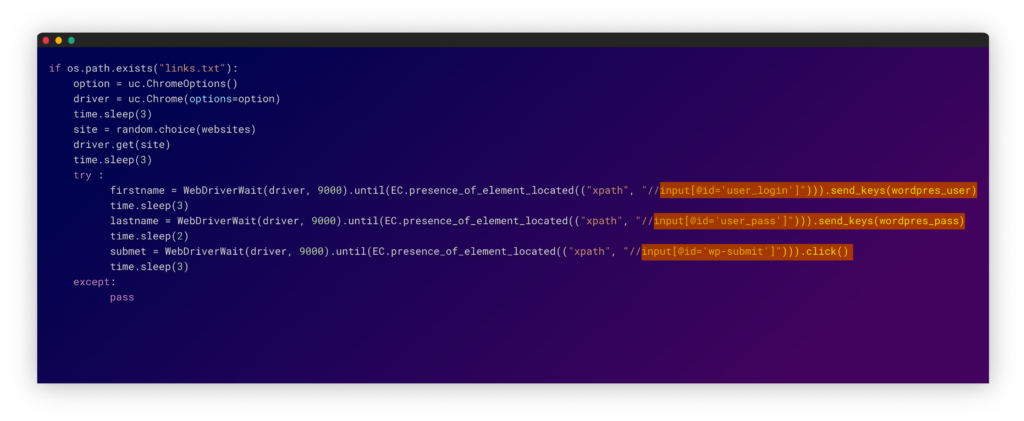
We believe uploading these PyPi scripts wen’t done intentionally by the attacker. A significant sign is that the scripts include the credentials used to authenticate with the WordPress websites, as was first recognized in this tweet by Jesse Mitchell.
Conclusion
These attackers invested in automation in order to poison the entire NPM ecosystem with over 15,000 packages. This allowed them to publish a large number of packages in a short period of time, making it difficult for the different security teams to identify and remove the packages quickly. The attackers also created many user accounts, making it difficult to trace the source of the attack. This shows the sophistication and determination of these attackers, who were willing to invest significant resources in order to carry out this campaign. Interestingly, it appears that this is the same attacker as a previous spam attack we detected last December.
The battle against threat actors poisoning our software supply chain ecosystem continues to be a challenging one, as attackers constantly adapt and surprise the industry with new and unexpected techniques.
By working together, we can stay one step ahead of attackers and keep the ecosystem safe. We believe this kind of collaboration is crucial in the fight against software supply chain attacks, and we will continue working together to help protect the open-source ecosystem.
List of Packages
The scale of this phishing campaign is significant, and you are welcome to download the full dataset hosted on GitHub Gist
https://gist.github.com/masteryoda101/a3f3500648f7e6da7bf89b3fb210e839
This will allow you to further analyze the data and gain a better understanding of the scope and nature of the attack.
If you would like access to the original metadata or samples from this phishing campaign, please feel free to send an email to supplychainsecurity@checkmarx.com. Our team will be happy to provide you with the information you need.
IOC
In total, we analyzed over 190 unique URLs (click to get the full list), which we were able to reduce to approximately 31 domains.
betapps[.]club
stumblegems[.]site
tubemate[.]vip
followersfree[.]store
apostasesportiva[.]info
sahel-digital-art[.]org
xapk[.]online
dailyspins[.]store
press-citizen-media[.]com
rebrand[.]ly
t[.]co
shahidvip[.]com
newjesuitreview[.]org
nbadeadlines[.]com
fundacionsuma[.]org
nftscollection[.]online
legalcoins[.]vip
canva-pro-free-accounts[.]
blogspot[.]com
trendcoffee[.]cc
journaldogs[.]com
free4free[.]monster
redapk[.]xyz
elavil[.]store
hiromi-haneda[.]com
claptonfc[.]info
coolhack[.]us
generators[.]searchbuzz[.]co
baby-ace[.]net
crestor[.]store
nfljerseys[.]fun