While the use of Infrastructure as Code (IaC) has gained significant popularity as organizations embrace cloud computing and DevOps practices, the speed and flexibility that IaC provides can also introduce the potential for misconfigurations and security vulnerabilities.
IaC allows organizations to define and manage their infrastructure using machine-readable configuration files, which are typically version-controlled and treated as code. IaC misconfigurations are mistakes, or oversights, in the configuration of infrastructure resources and environments that happen when using IaC tools and frameworks.
Misconfigurations in IaC can lead to security vulnerabilities, operational issues, and even potential breaches.
Common types of misconfigurations
Common misconfigurations include weak access controls, improperly exposed ports, insecure network configurations, or mismanaged encryption settings. Some of the most common types of IaC Security misconfigurations are:
- Access Controls: Misconfigurations related to access controls can result in unauthorized access to resources. This includes issues such as overly permissive access permissions, misconfigured role-based access control (RBAC), or incorrect security group rules. Attackers can exploit these misconfigurations to gain unauthorized access to sensitive data, or systems.
- Network Configuration: Misconfigurations in network settings can expose services or applications to unnecessary risks. For example, improperly configured firewall rules, open ports, or lack of network segmentation can lead to unauthorized access, network attacks, or data exfiltration.
- Encryption and Data Protection: Failure to implement proper encryption and data protection measures can result in data breaches. Misconfigurations may include not encrypting data at rest or in transit, using weak encryption algorithms or keys, or storing sensitive data in insecure locations.
- Logging and Monitoring: Misconfigurations related to logging and monitoring can hinder the ability to detect and respond to security incidents. This includes improper configuration of log collection, aggregation, and retention, or misconfigured monitoring rules, leading to missed alerts and delayed incident response.
- Secret Management: IaC misconfigurations can expose sensitive credentials or secrets, such as API keys, database passwords, or encryption keys. Storing secrets in plaintext, checking them into version control systems, or including them in IaC templates can lead to unauthorized access or misuse.
- Resource Permissions: Misconfigurations in resource permissions can result in excessive or insufficient privileges. Overly permissive permissions may allow unauthorized actions, while overly restrictive permissions can impede proper functionality or lead to operational disruptions.
- Cloud Provider-specific Misconfigurations: IaC misconfigurations can vary depending on the cloud provider being used. Each provider has its own set of services, configuration options, and security controls. Misconfigurations may involve misusing or misconfiguring specific services, not following best practices, or overlooking provider-specific security recommendations.
- Compliance and Governance: Misconfigurations can result in non-compliance with industry regulations, data protection laws, or internal governance requirements. Failure to configure resources in accordance with these guidelines can lead to legal and regulatory consequences.
IaC misconfigurations can, of course, lead to security vulnerabilities, but they can also make infrastructure management and maintenance more challenging for AppSec managers and development teams. When misconfigurations are pervasive, it becomes harder to identify and rectify them during updates, scaling, or changing infrastructure requirements. This can result in longer deployment cycles, increased risk of errors during updates, and higher operational complexity.
Beyond the challenges faced by the organization when misconfigurations are present, misconfigurations are often complicated for developers to troubleshoot. Identifying the root cause of misconfigurations can become increasingly time-consuming and complex if not addressed directly, and developers don’t always know exactly how to resolve misconfigurations, which can leave a development team frustrated and overwhelmed as they try to resolve the issue.
Introducing AI Guided Remediation for IaC / KICS
To make it easier for development teams to address the various types of IaC misconfigurations, Checkmarx is pleased to introduce AI Guided Remediation for IaC Security and KICS.
Security Platform, with KICS (Keeping Infrastructure as Code Secure) is a free, open source solution for static analysis of IaC files. KICS automatically parses common IaC files of any type to detect insecure configurations that could expose your applications, data, or services to attack.analysis of IaC files. KICS automatically parses common IaC files of any type to detect insecure configurations that could expose your applications, data, or services to attack.files. KICS automatically parses common IaC files of any type to detect insecure configurations that could expose your applications, data, or services to attack.files. KICS automatically parses common IaC files of any type to detect insecure configurations that could expose your applications, data, or services to attack.
Powered by GPT4, AI Guided Remediation provides actionable remediation steps and advice to guide teams through the process of remediating IaC misconfigurations identified by Checkmarx IaC Security and KICS. This helps organizations address issues in their IaC files and deploy their applications faster and safer.
IaC Security and AI Guided Remediation is a powerful combination that makes it faster and easier for developers to more deeply understand and quickly remediate misconfigurations.
How it works
Continuing the Checkmarx promise to make application security as easy and efficient as possible for developers and AppSec teams, the new AI Guided Remediation functionality is straightforward and easy-to-use, all within the integrated development environments (IDEs) where development teams are spending their time.
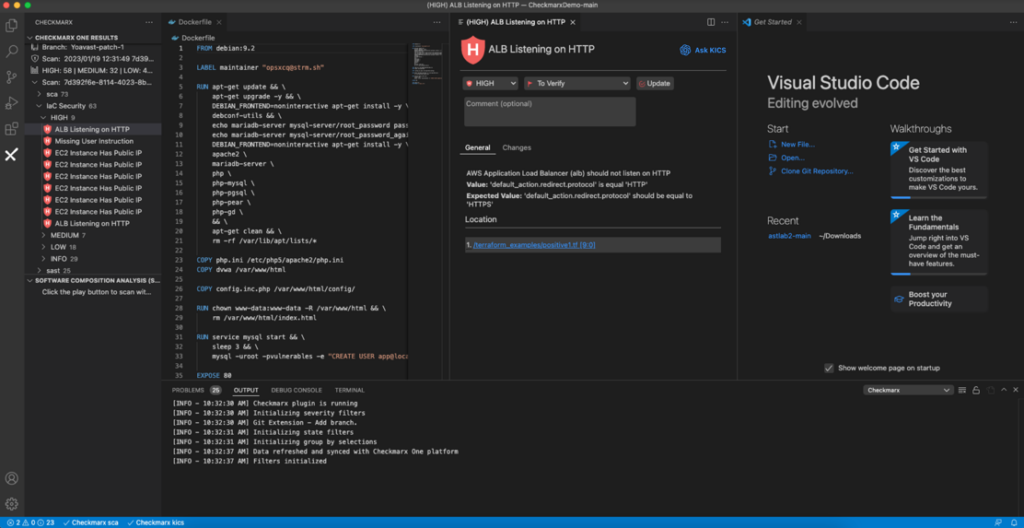
When a given vulnerability is identified by Checkmarx IaC Security / KICS, an “Ask KICS” option is displayed on screen. Developers can simply click on the button to open a panel, where they have a couple of options.
Developers can first select from common questions, with out-of-the-box prompts displayed on-screen.
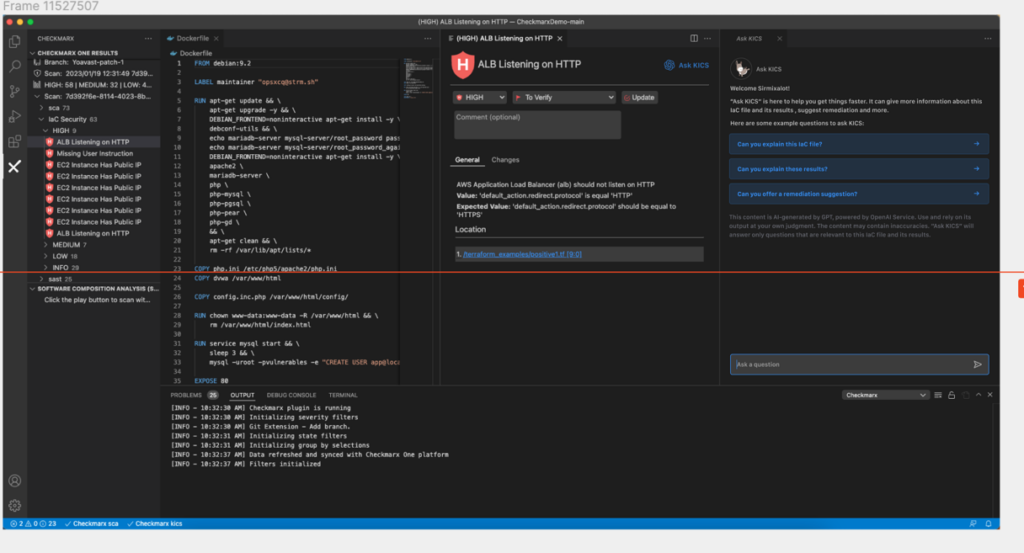
Alternatively, users can use the free-text field to ask specific questions.
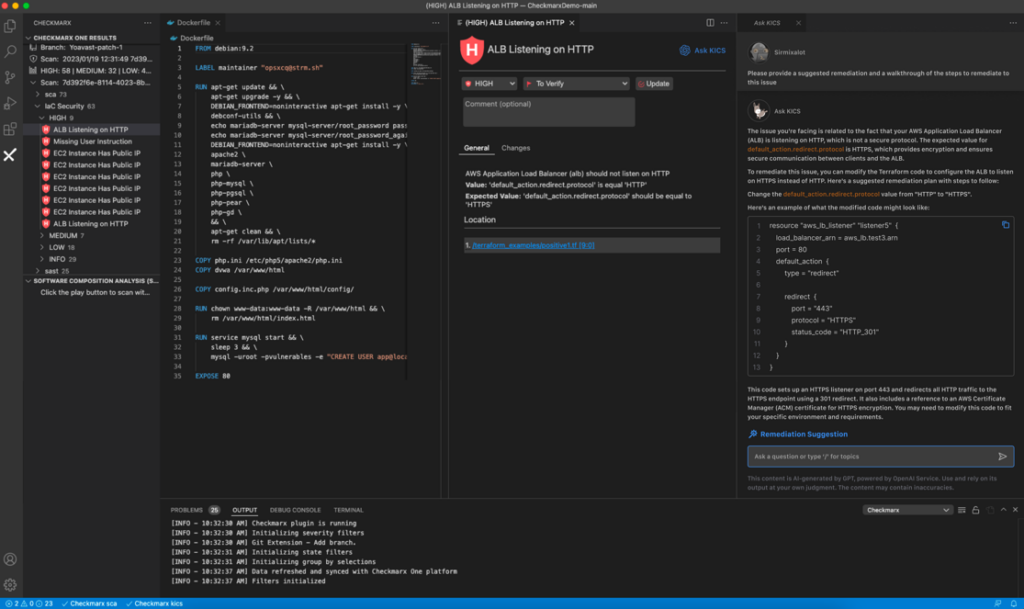
The tool will then deliver an AI-generated response, giving developers and AppSec managers actionable steps to remediate the misconfiguration.
Providing actionable steps, AI Guided Remediation helps developers better understand IaC and API misconfigurations without additional resources. Developers do not need to know the details of exactly how to remediate all of the various types of misconfigurations; instead, they can lean on the power of AI to quickly harvest the plethora of resources, documentation, and community knowledge helps development teams identify actionable steps to quickly and easily remediate misconfigurations.
With AI Guided Remediation, organizations can address issues in their IaC templates faster, reduce management overhead, boost developer adoption, and deliver more secure applications faster.
Organizations wanting to leverage this functionality can rest assured knowing that their proprietary code is secure. Importantly, the organization’s code is not shared with AI tooling.
Additionally, AI Guided Remediation detects and removes secrets before sending the code to the chat. Secrets, such as API keys, database passwords, or encryption keys, are sensitive pieces of information that should never be exposed or shared inadvertently. By integrating secret detection and removal into AI Guided Remediation, organizations can significantly enhance the security of their infrastructure as code (IaC) and protect against unauthorized access or misuse
For Checkmarx users that would like to explore Checkmarx IaC Security / KICS, the addition of AI Guided remediation provides an exciting new opportunity to easily review and action vulnerabilities identified by Checkmarx IaC Security / KICS, all within the Checkmarx One™ Application Security Platform.
It’s easy to get started
For existing Checkmarx IaC / KICS users who want to explore the power of AI Guided Remediation, especially to see how it can create a better developer experience, the Checkmarx AI early access program is now available.
Sign up now to be among the first to leverage AI Guided Remediation for IaC Security / KICS.
Checkmarx Early Access program
Not already using Checkmarx IaC or KICS? Existing Checkmarx SAST users who want to explore the power of leveraging Checkmarx IaC / KICS and the AI Guided remediation are encouraged to learn more about all of the powerfully simple AI-driven features available within the Checkmarx One™ Application Security Platform, the industry’s most comprehensive platform for reducing risk within today’s complex, cloud-native applications.
Contact your Checkmarx account manager, or contact Checkmarx today.