Checkmarx One
Software Composition Analysis (SCA)
Identify, prioritize, and remediate open source risk in your applications, including vulnerabilities, malicious code, and license risks.

Everything You Need to Mitigate Open Source Risk
Checkmarx provides comprehensive SCA functionality with unparalleled accuracy.
Highest Accuracy in the Industry
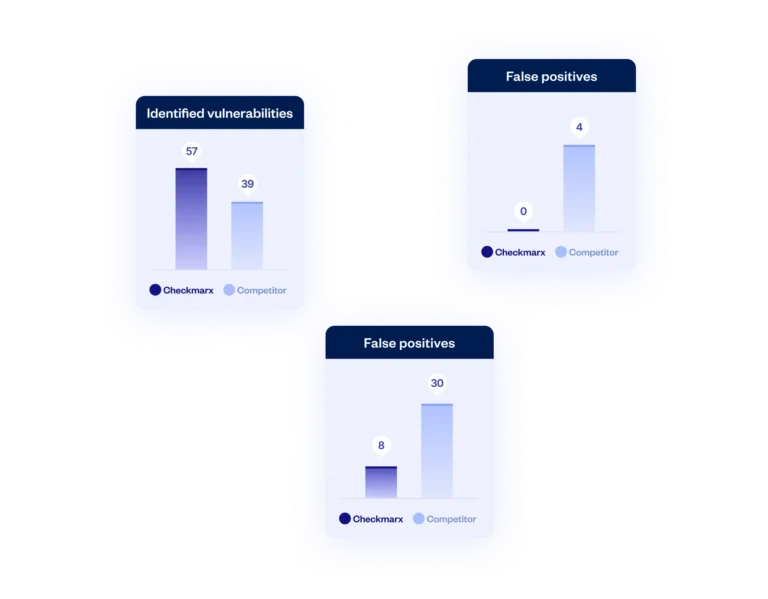
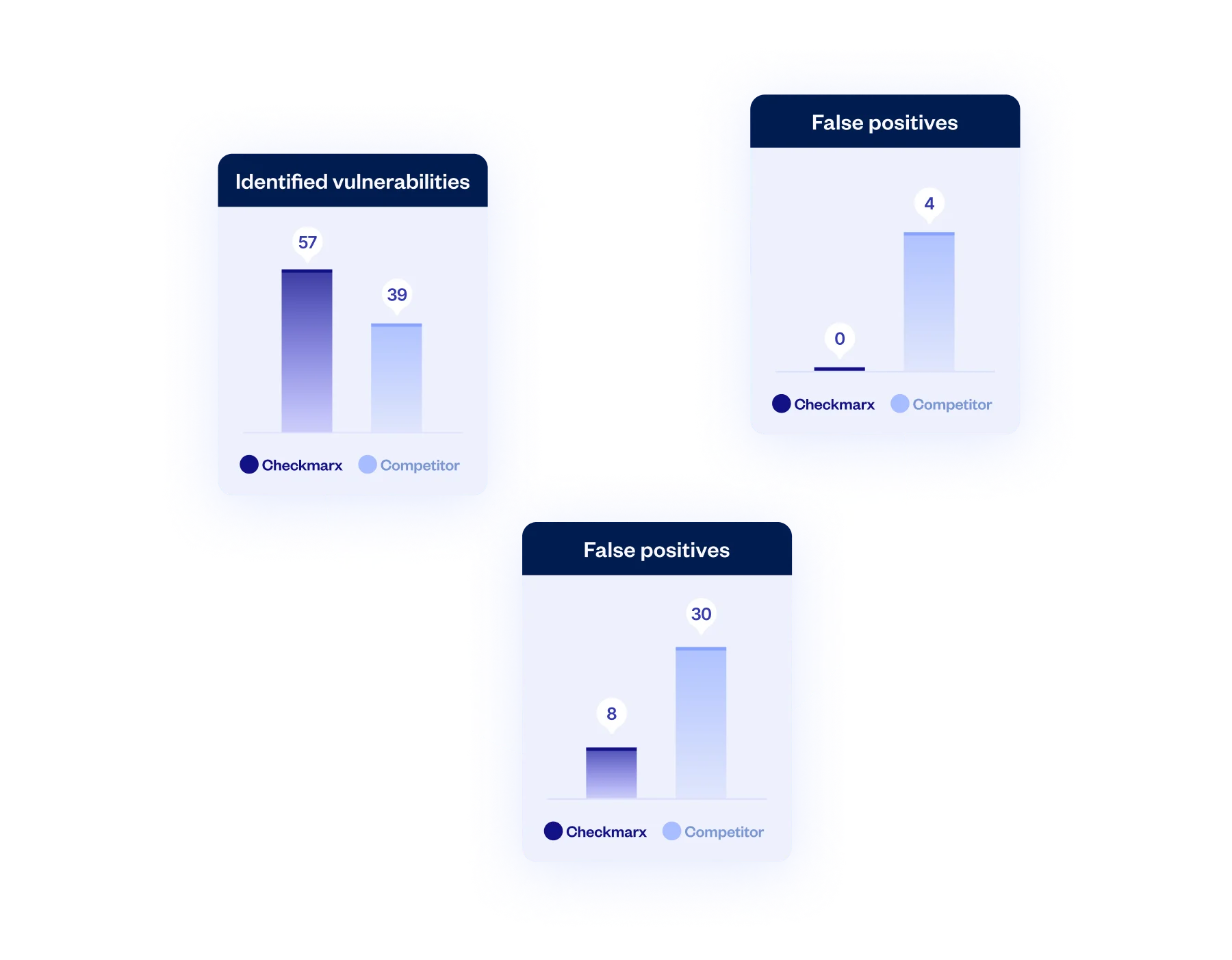
In a recent third-party competitive evaluation of OSS vulnerability detection, Checkmarx came out far ahead across all key metrics, including zero false positives (versus the competitor’s FP rate of 10%).
Read the ReportTransitive Dependency Scanning
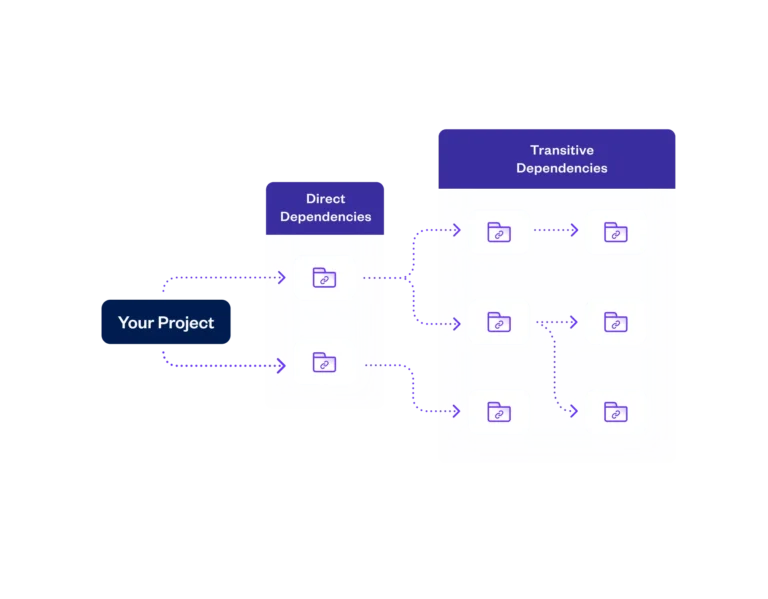
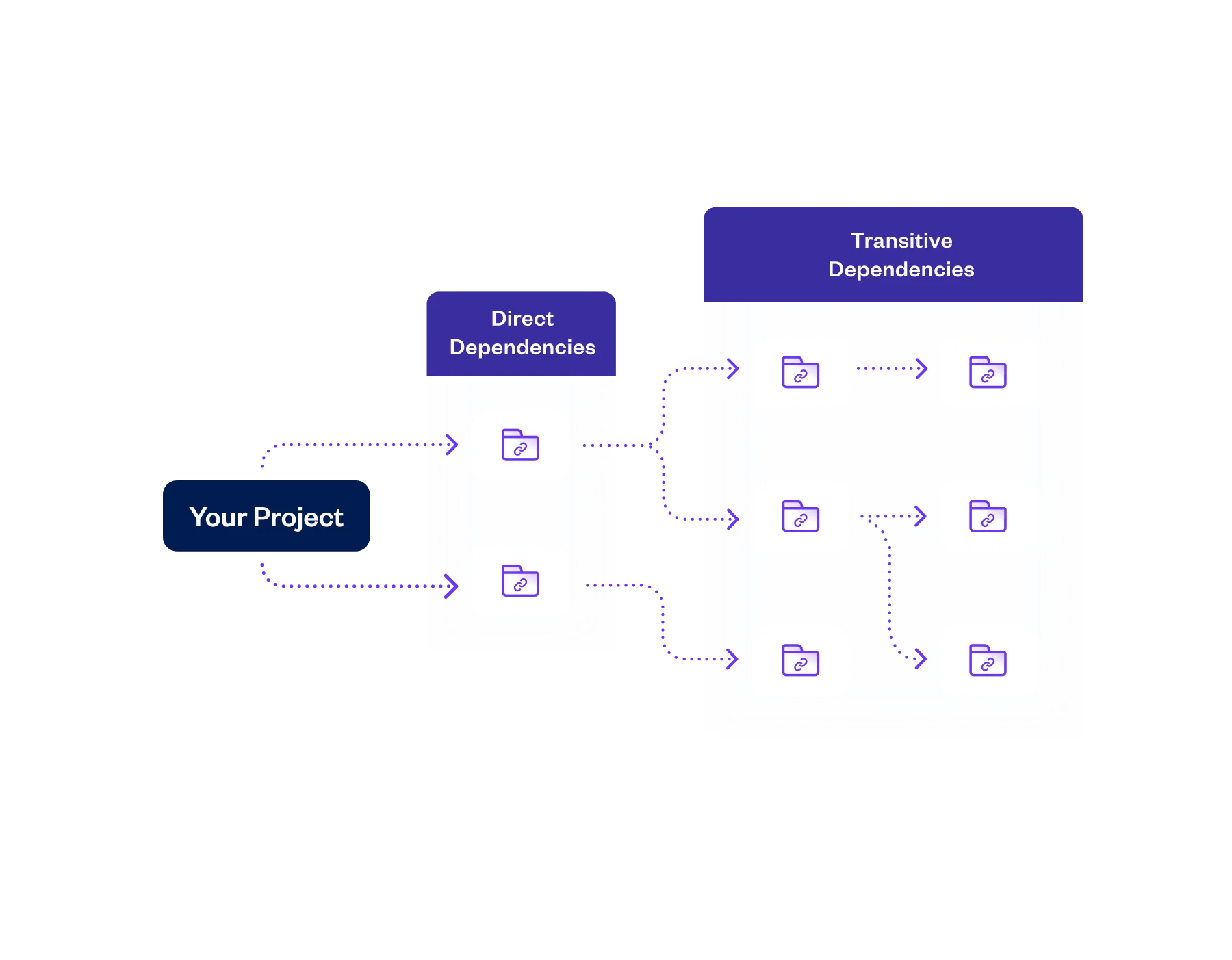
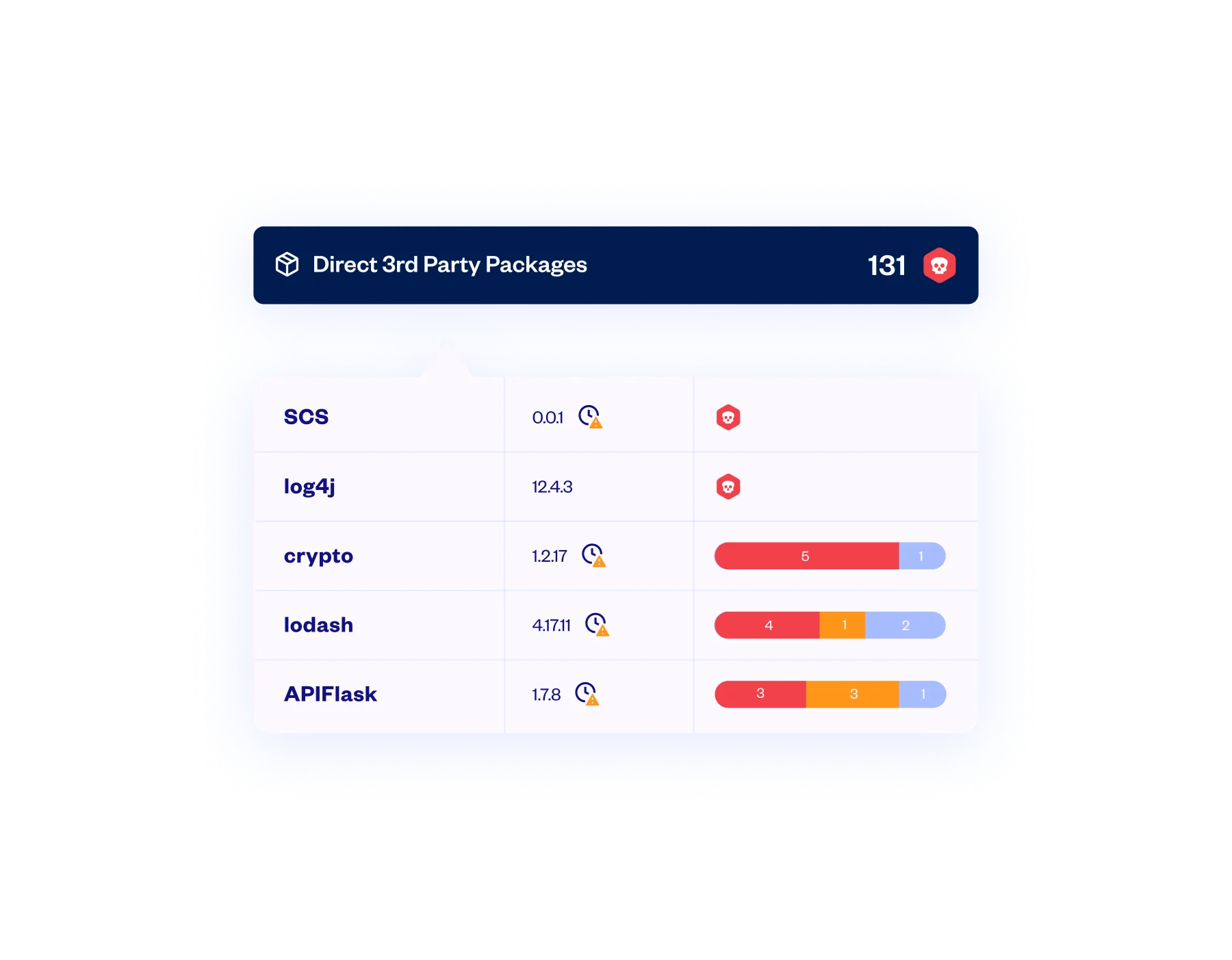
Comprehensive discovery and scanning of all directly and transitively referenced OSS and private packages – to unlimited depth – including those in on-prem and private JFrog Artifactory registries.
Malicious Package Protection

Checkmarx’ industry-leading proprietary database of more than 410,000 malicious packages enables you to identify and remediate any open source libraries in your applications known to contain malicious code.
Learn MoreEffective Reachability Analysis
Reduce noise and prioritize remediation efforts by focusing on vulnerable OSS code that may potentially execute, based on an analysis of all potential call paths to unsafe functions. Supports a variety of coding languages.
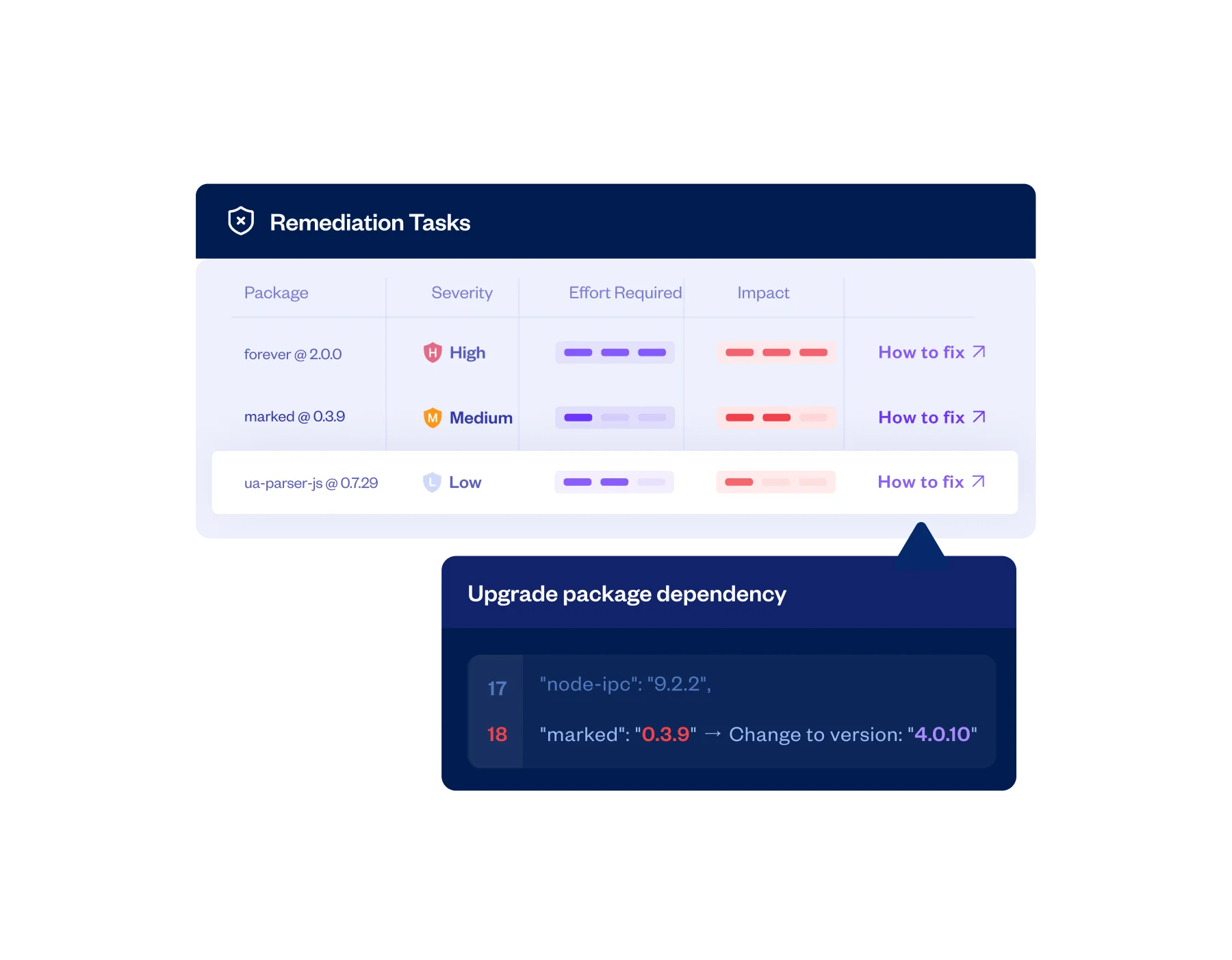
Actionable Remediation Guidance

Dramatically ease and expedite mitigation efforts with specific and actionable remediation guidance, including the expected effort and impact of each fix. Get AI recommendations for more secure alternative packages.
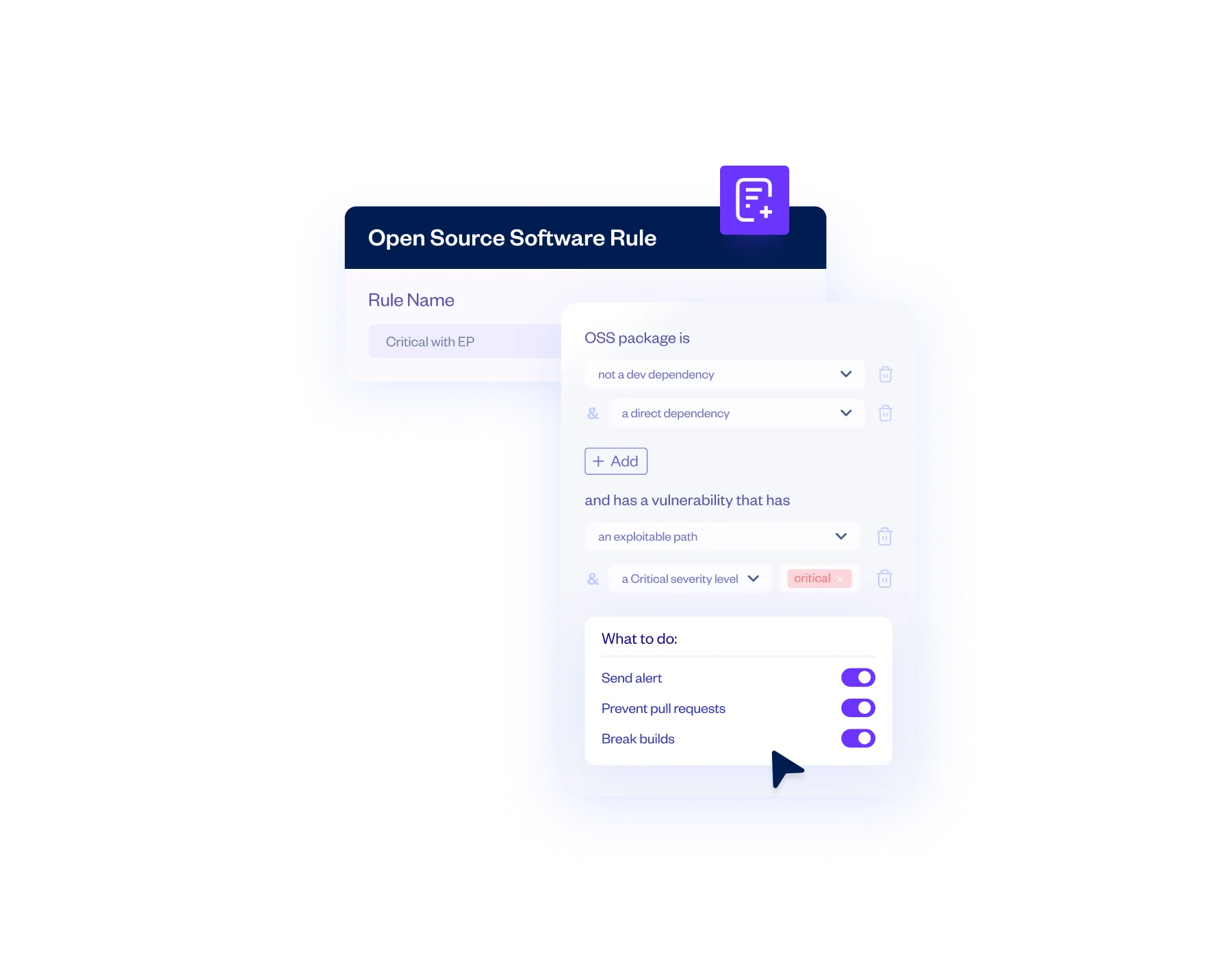
Policy Rules with Automated Actions

Policies based on package characteristics, CVSS (up to 4.0) vulnerability severity, reachability, malicious code detection, and licensing issues can be configured to send alerts, prevent pull requests, and break builds.
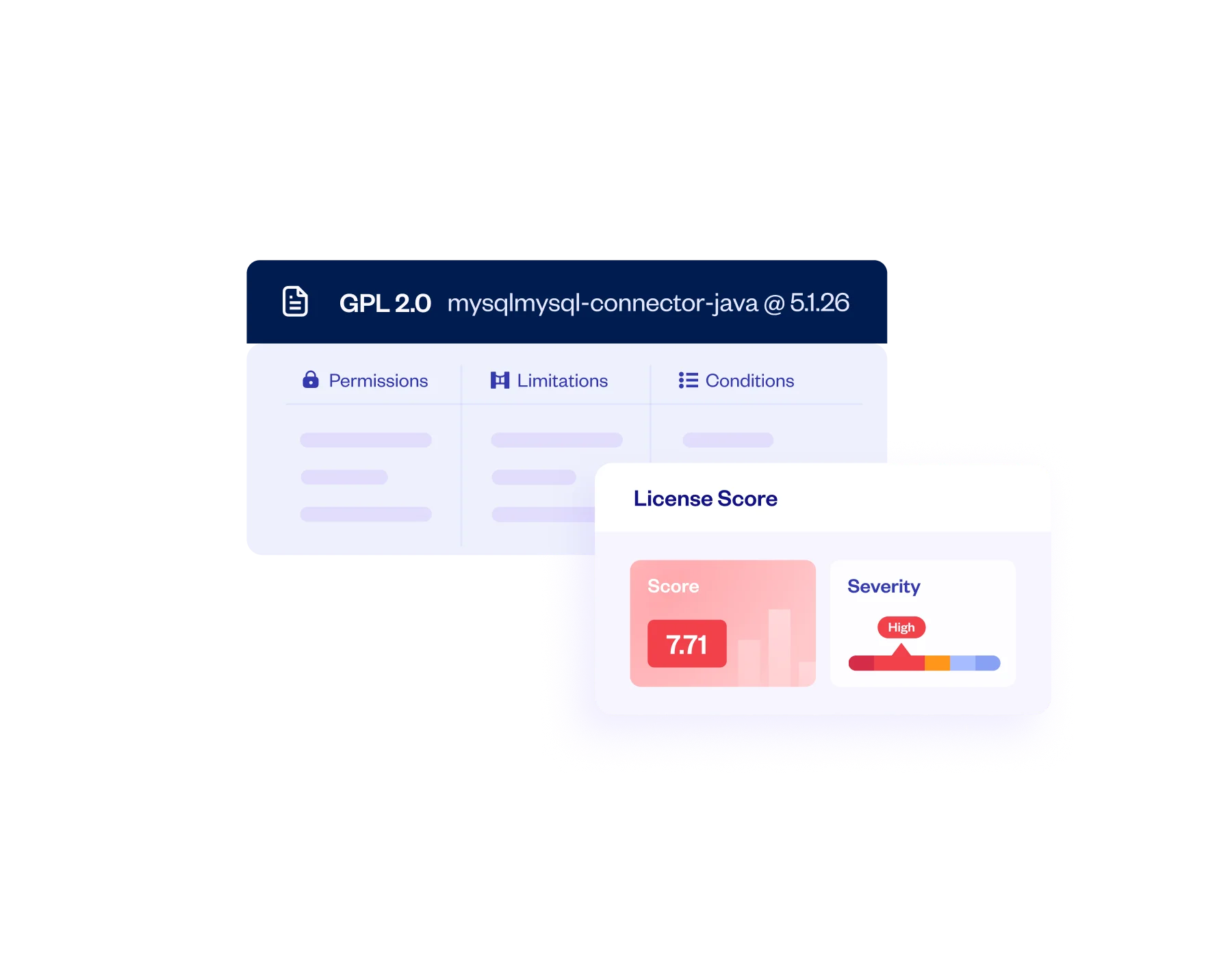
License Risk Management

Ensure awareness and tracking of all relevant third-party code license requirements and restrictions, to avoid potential compliance issues and other legal complications.
Software Bill of Materials (SBOM)

Generate, share, ingest, and manage SBOMs in industry-standard formats, to inventory the components of your applications and more easily comply with relevant regulatory, policy, and licensing requirements.
Learn More-
Highest Accuracy in the Industry
In a recent third-party competitive evaluation of OSS vulnerability detection, Checkmarx came out far ahead across all key metrics, including zero false positives (versus the competitor’s FP rate of 10%).
Read the Report -
Transitive Dependency Scanning
Comprehensive discovery and scanning of all directly and transitively referenced OSS and private packages – to unlimited depth – including those in on-prem and private JFrog Artifactory registries.
-
Malicious Package Protection
Checkmarx’ industry-leading proprietary database of more than 410,000 malicious packages enables you to identify and remediate any open source libraries in your applications known to contain malicious code.
Learn More -
Effective Reachability Analysis
Reduce noise and prioritize remediation efforts by focusing on vulnerable OSS code that may potentially execute, based on an analysis of all potential call paths to unsafe functions. Supports a variety of coding languages.
-
Actionable Remediation Guidance
Dramatically ease and expedite mitigation efforts with specific and actionable remediation guidance, including the expected effort and impact of each fix. Get AI recommendations for more secure alternative packages.
-
Policy Rules with Automated Actions
Policies based on package characteristics, CVSS (up to 4.0) vulnerability severity, reachability, malicious code detection, and licensing issues can be configured to send alerts, prevent pull requests, and break builds.
-
License Risk Management
Ensure awareness and tracking of all relevant third-party code license requirements and restrictions, to avoid potential compliance issues and other legal complications.
-
Software Bill of Materials (SBOM)
Generate, share, ingest, and manage SBOMs in industry-standard formats, to inventory the components of your applications and more easily comply with relevant regulatory, policy, and licensing requirements.
Learn More


Checkmarx: The Most Accurate and
Automated SCA
Better identify, manage, and remediate open source risk as an integrated part of your SDLC.
What’s in it for you
How Organizations Benefit From Checkmarx SCA
Checkmarx One’s SCA provides a comprehensive solution for CISOs, AppSec teams, and Developers.
FAQ
What differentiates Checkmark’s SCA tool from others?
Checkmarx SCA provides comprehensive coverage and highly accurate results, with full visibility into vulnerabilities, malicious code, and license risks in open-source libraries. Checkmarx analyzes one million packages each month; the company has identified more than 400,000 open-source libraries containing malicious code. Tight IDE, CLI tool, and CI/CD integration make it easy to integrate security workflows, including automatic SCA scan triggering, within existing development and deployment platforms.
Users are provided with prioritized remediation guidance to ensure that the most critical risks are addressed first. Also included are SBOM generation and ingestion, exploitable path analysis, transitive dependency scanning, binary dependency scanning, private package scanning, a risk management dashboard, policy rules with automated actions, and comprehensive reporting.
What is exploitable path analysis?
Checkmarx’ unique exploitable path analysis is an advanced form of reachability analysis that accurately determines which vulnerable classes or functions within third-party libraries may be called by an application at runtime. By prioritizing code that is potentially exploitable when the application is published (versus other vulnerabilities that are not currently being called by the application and are thus not readily exploitable), developers can remediate the most dangerous libraries first.
How can a Software Composition Analysis tool improve security?
Software Composition Analysis is a proactive approach to securing third-party code which is in line with modern security principles of continuous monitoring and early detection of potential threats. By preemptively addressing security risks and compliance issues, developers can focus on coding and continue to confidently leverage open source libraries and components, while ensuring applications are secure.
How does SCA differ from traditional security testing?
Software Composition Analysis (SCA) differs from traditional security testing by focusing on identifying vulnerabilities and malicious code in open-source and other third-party components within an application. Rather than testing for flaws in proprietary code, SCA examines dependencies for known security risks, licensing issues, and outdated versions, enabling faster remediation of vulnerabilities in widely used external libraries.
Why is SCA important in software development?
Open-source components are widely used in modern software development, yet they can introduce vulnerabilities or malicious code into applications. Software Composition Analysis (SCA) tools identify these risks early, enabling quick remediation and empowering developers to continue leveraging open-source components confidently. This approach supports developer productivity while ensuring the security and stability of the codebase.
What is SCA vs. SAST?
Static application security testing (SAST) scans proprietary code written by your developers, while software composition analysis (SCA) scans open source libraries and third-party components.
What is a software bill of materials (SBOM)?
An SBOM is a file that helps organizations see an application’s makeup to assess and address the security risk across all its underlying components.
Can I integrate SCA into my CI/CD pipeline?
Checkmarx SCA easily integrates into your CI/CD pipeline, works seamlessly with a wide variety of CI/CD tools, including Jenkins, Azure DevOps, GitHub Actions, and TeamCity.
How can I try Checkmarx SCA?
Checkmarx SCA is available on the Checkmarx One platform. Developers can get it free within JetBrains’ IntelliJ IDEA Ultimate and Visual Studio Code plugins.
Checkmarx One
The Cloud-Native Enterprise Application Security Platform
Checkmarx One delivers a full suite of enterprise AppSec solutions in a unified, cloud-based platform that allows enterprises to secure their applications from the first line of code to deployment in the cloud.
Get everything your enterprise needs to integrate AppSec across every stage of the SDLC and build a successful AppSec program
Application Security Posture
Management (ASPM) Consolidated, correlated, prioritized insights to help your team manage risk
Code
AI Powered-
Conduct fast and accurate scans to identify risk in your custom code.
-
Identify vulnerabilities only seen in production and assess their behavior.
-
Eliminate shadow and zombie APls and mitigate API-specific risks.
Supply Chain
AI Powered-
Easily identify, prioritize, remediate, and manage open source security and license risks.
-
Detect and remediate malicious or suspicious third-party packages that may be endangering your organization.
-
Built to accelerate AppSec teams and help developers secure applications from the first line of code.
-
Minimize risk by quickly identifying and eliminating exposed secrets.
-
Reduce security risks by health-scoring the code repositories used in your applications.
Cloud
AI Powered-
Scan container images, configurations, and identify open source packages and vulnerabilities preproduction and runtime.
-
Automatically scan your laC files for security vulnerabilities, compliance issues, and infrastructure misconfigurations.
Dev Enablement
-
Secure code training to upskill your developers and reduce risk from the first line of code.
DevSecOps
-
75+ Languages
-
100+ Frameworks
-
75+ Technologies
-
SDLC Integrations
Services
-
Maximize ROI with prioritized technical support, metrics monitoring, and operational assistance.
-
Augment your security team with Checkmarx services to ensure the success of your AppSec program.
-
Assess the current state of your AppSec program, benchmark against peers, and get actionable next steps for improvement.
Unified Dashboard, Reporting & Risk Management
Application Security Posture
Management (ASPM)
Consolidated, correlated, prioritized insights to help your team manage risk
AI Powered
Code
-
SAST
Static Application Security Testing (SAST)
Conduct fast and accurate scans to identify risk in your custom code.
-
DAST
Dynamic Application Security Testing (DAST)
Identify vulnerabilities only seen in production and assess their behavior.
-
API Security
API Security
Eliminate shadow and zombie APls and mitigate API-specific risks.
Supply Chain
-
SCA
Software Composition Analysis (SCA)
Easily identify, prioritize, remediate, and manage open source security and license risks.
-
Malicious Package Protection
Malicious Package Protection
Detect and remediate malicious or suspicious third-party packages that may be endangering your organization.
-
AI Security
AI Security
Built to accelerate AppSec teams and help developers secure applications from the first line of code.
-
Secrets Detection
Secrets Detection
Minimize risk by quickly identifying and eliminating exposed secrets.
-
Repository Health
Repository Health
Reduce security risks by health-scoring the code repositories used in your applications.
Cloud
-
Container Security
Container Security
Scan container images, configurations, and identify open source packages and vulnerabilities preproduction and runtime.
-
IaC Security
IaC Security
Automatically scan your laC files for security vulnerabilities, compliance issues, and infrastructure misconfigurations.
Get a Demo
Get Checkmarx SCA Today
Learn why enterprises across the globe rely on Checkmarx SCA to manage the risks associated with open source and other third-party dependencies.
Trusted By:


