
Infrastructure as Code (IaC) is the description of infrastructure (clusters, virtual machines, networking, storage, etc.) with a declarative model and its subsequent management using the same principles as source code. Companies that have adopted Infrastructure as Code have a unified way of working with both applications and infrastructure using the same tools (i.e., version control) and workflows.
IaC tools are now available for many different infrastructure providers ranging from traditional virtual machines to Kubernetes clusters and containerized applications.
One advantage of IaC is that all techniques that are usually aimed at source code (e.g., unit tests, linting, security scanning) can now be applied to infrastructure as well.
Static Analysis with Checkmarx KICS
Static analysis of infrastructure is a particularly important aspect of a secure workflow, as errors in infrastructure can result in unplanned downtime, to having security issues in production environments.
KICS (Keeping Infrastructure as Code Secure) is a free, open-source solution for static code analysis of IaC powered by Checkmarx.
KICS automatically parses common IaC files of any type to detect insecure configurations that could expose your applications, data, or services, which are deployed on the cloud, to attack. That means you can let anyone on your team write IaC files, and then vet the files to ensure they are secure before deployment.
Instead of setting security guidelines in your IT governance policies and hoping engineers and developers follow them when creating IaC files, you can automatically enforce IaC security with KICS.
KICS is an open-source tool that supports all mainstream IaC platforms like:
- Terraform
- CloudFormation
- Azure Resource Manager
- Google Deployment Manager
- Ansible
- Kubernetes/Helm manifests
- and more
KICS also integrates with a variety of software development tools and makes it possible to add IaC security scanning to your existing workflows without friction.
As an open-source, platform-agnostic IaC scanning tool, KICS can grow seamlessly along with your development and deployment operations.
Developers can extend KICS with new checks and policies using a simple, industry-standard query language (REGO). In addition, developers can quickly onboard new items to automated scanning workflows while also extending IaC scanning capabilities into new parts of their application stack or new types of IaC resources by taking advantage of KICS’ modular design.
KICS also enables organizations to keep up with security best practices and comply with CIS benchmarks such as “CIS Amazon Web Services Foundations Benchmark version 1.4.0, Level 1” or level 2.
For more details on KICS refer to:kics.io
Automating Static Analysis with Codefresh
KICS offers several ways to run it out of the box. You can run it from the command line, via a Docker container, or even try it from a web interface. For a production environment however, an automated workflow where a deployment pipeline is running KICS as part of the full infrastructure lifecycle is strongly recommended. A logical way to run KICS would be as part of a Continuous Integration (CI) process resulting in repeatable scans against any change in infrastructure files.
The Codefresh Software Delivery Platform includes a Continuous Integration component that can easily run KICS in an automated way using any of the supported triggers. As a very simple example, if a developer changes a Kubernetes manifest for an environment, KICS should be executed as part of the commit action to verify that the change is valid.
For Codefresh CI, a KICS pipeline step is already available in the steps marketplace. You can therefore insert KICS anywhere in a Codefresh pipeline and use it to verify any supported IaC file.
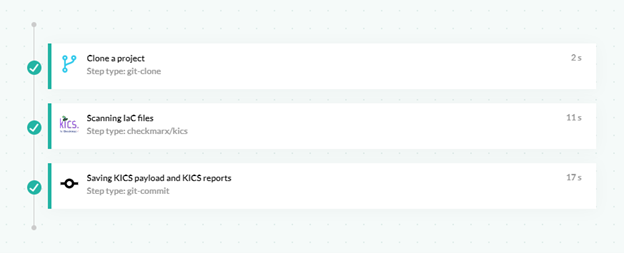
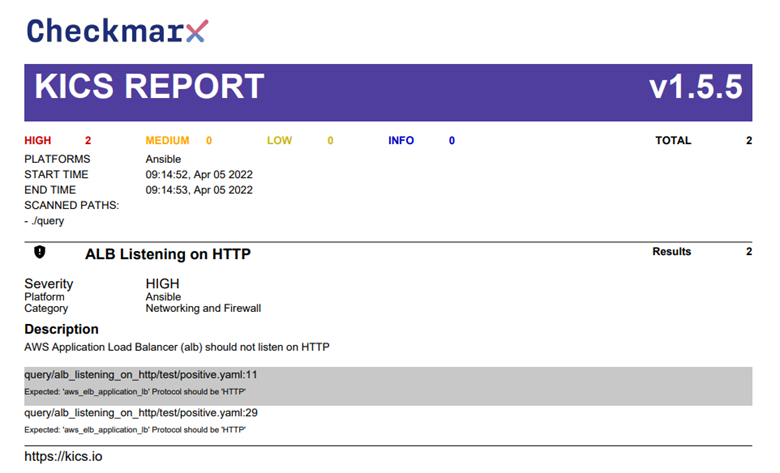
Once the security scan is complete, you can further copy/upload the report to any supported storage provider of your choice, or use an intermediate format (e.g., json) to further process the results.
You can also apply the infrastructure files themselves directly via Codefresh pipelines. Codefresh has built-in support for Kubernetes/Helm manifests and can easily use any other IaC tool such as Terraform for creating a complete pipeline that both checks and applies Infrastructure as Code files.
Running KICS using the Codefresh GitOps platform
You can use KICS from the classic Codefresh CI platform as we saw in the previous section. There is also upcoming integration for using KICS in the new Codefresh Software Delivery Platform that is specifically created for GitOps deployments and is powered by the Argo Project. Adopting GitOps is a natural extension of Infrastructure as Code and the new integration will soon appear in the Codefresh Argo Hub.
With KICS and Codefresh, developers and AppSec team can improve the security of their IaC to reduce risk and increase confidence of secure IaC. In fact, over 650K people have downloaded KICS as of date.