Financial Services: DevSecOps Engineering
Checkmarx One Enterprise Application Security Platform
91% of organizations knowingly released vulnerable applications. Learn why in the annual Future of AppSec Report.
Read NowCheckmarx One
The Enterprise Application
Security Platform
Secure your apps from code to cloud. Get correlated results from a unified platform and ensure the success of your enterprise AppSec program.
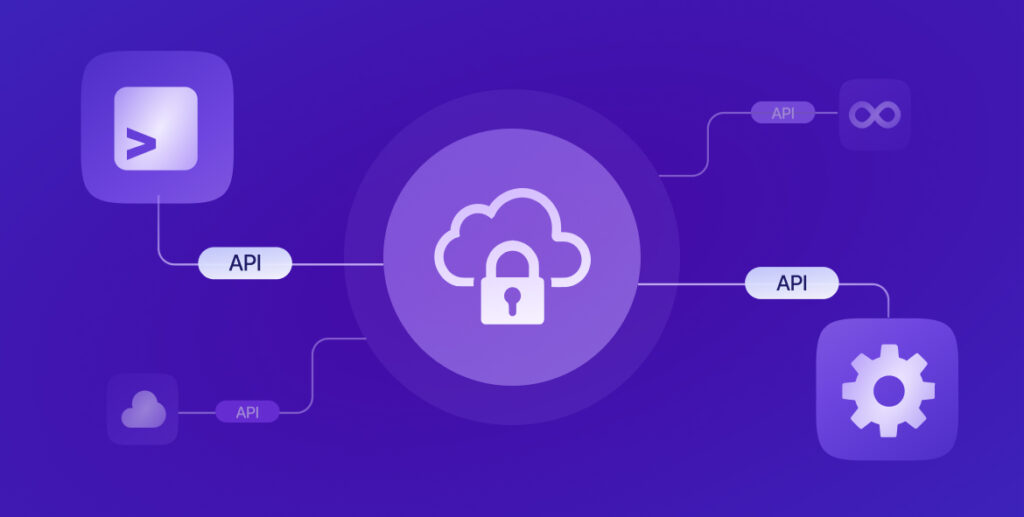
Unified Dashboard & Reporting
FUSION CORRELATION ENGINE
Static Application Security Testing (SAST)
Conduct fast, accurate scans to identify risk in your custom code.
Software Composition Analysis (SCA)
Identify security and license risks in open source software that is used in your applications.
Software Supply Chain Security (SSCS)
Proactively identify software supply chain attacks, and secure developer environments.
API Security
Eliminate shadow and zombie APIs and mitigate API-specific risks.
Dynamic Application Security Testing (DAST)
Identify vulnerabilities only seen in production and assess their behavior.
Container Security
Scan static container images, check configurations, and determine what open source packages are called and identify vulnerabilities pre-production
Infrastructure-as-Code (IaC) Security
Automatically scan your IaC files to find security vulnerabilities, compliance issues, and infrastructure misconfigurations.
Runtime Security
Correlate identified open source vulnerabilities with runtime insights to protect containers while apps are running
Powered By AI
+75 technologies and languages, +100 frameworks
SDLC integrations
Services
Create Your Ideal Enterprise
Application Security Program
Checkmarx One integrates a comprehensive suite of AppSec solutions,
including SAST, SCA, SCS, API Security, DAST, Container, and IaC Security.
This unified approach eliminates the need for multiple tools and fragmented workflows, streamlining your DevSecOps and enabling you to identify and remediate vulnerabilities faster than ever before.
Build
#DevSecTrust
Build trust between AppSec and developers to find and fix vulnerabilities and reduce risk.
Get The Most
Out of AppSec Consolidation
Simplify management, reduce TCO, and get better security outcomes from AppSec tools built to work together.
Fastest Time
To Value
Scan in minutes, adopt a proven AppSec program methodology, and customize your AppSec tools to reduce false positives up to 90%.


























The Cloud-Native Enterprise AppSec Platform
Checkmarx One has everything you need to embed AppSec in every stage of the SDLC, provide an excellent developer experience, integrate with the technologies you use, and build a successful AppSec program.
From Code To Cloud
A full suite of AppSec tools, from SAST and SCA, to runtime protections.

Cloud Native
Checkmarx One is built on the cloud, for the cloud. Get everything you need to secure new cloud native apps while maintaining protection for legacy apps.
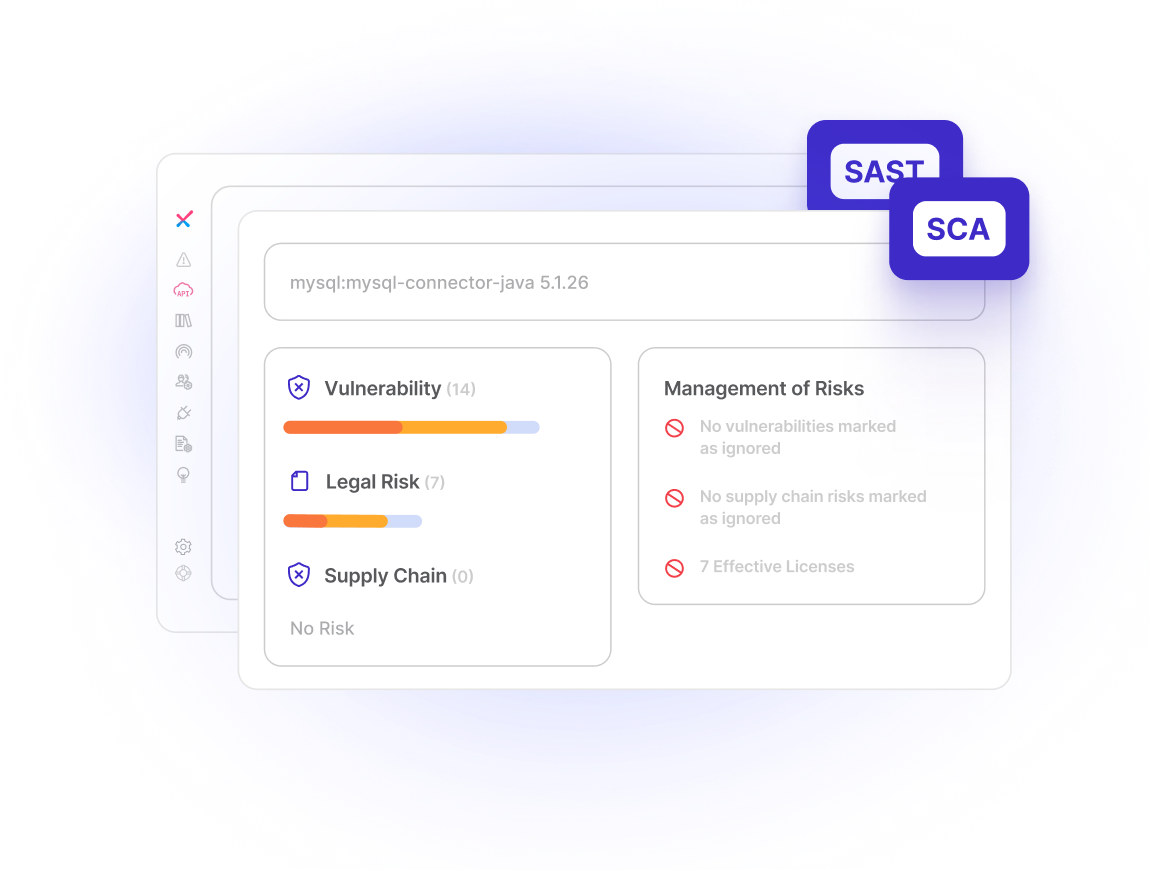
Fusion Correlation Layer
Automatically correlate results from multiple AppSec tools for higher accuracy and less noise.
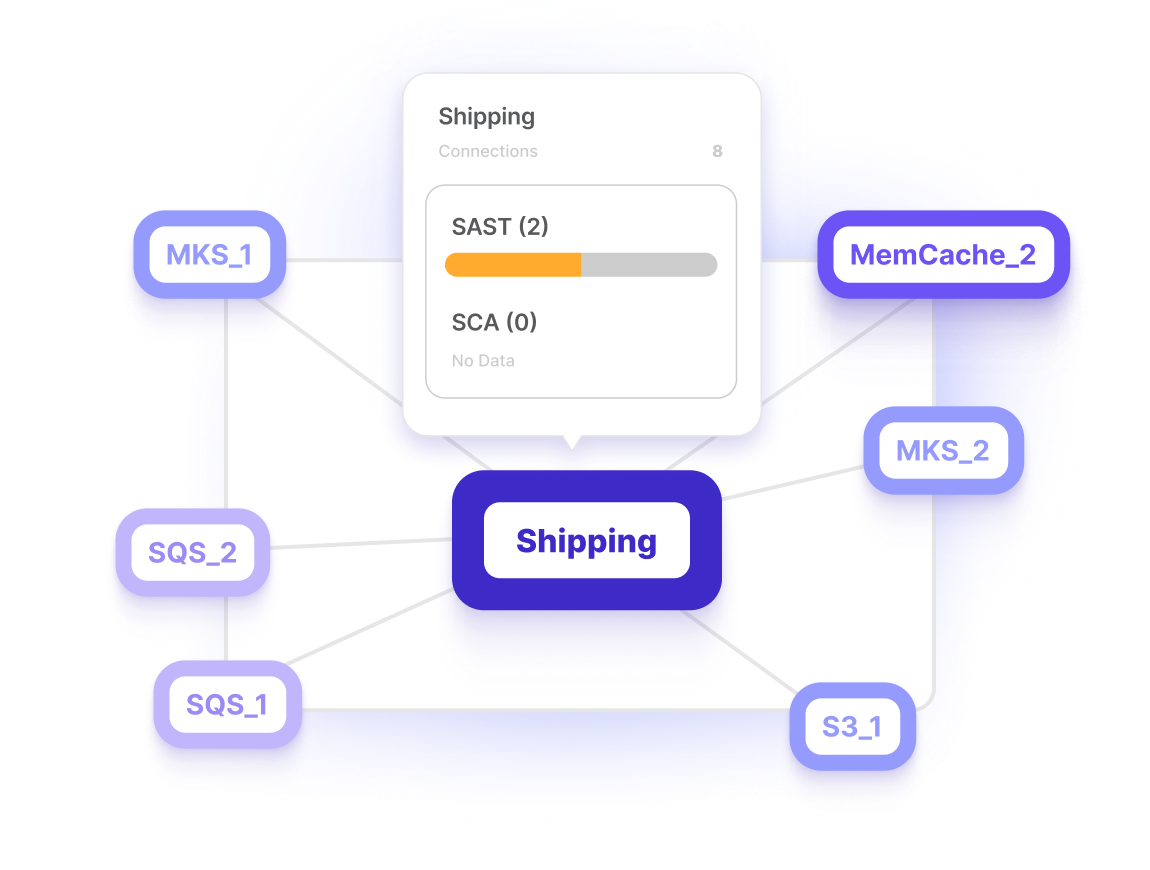
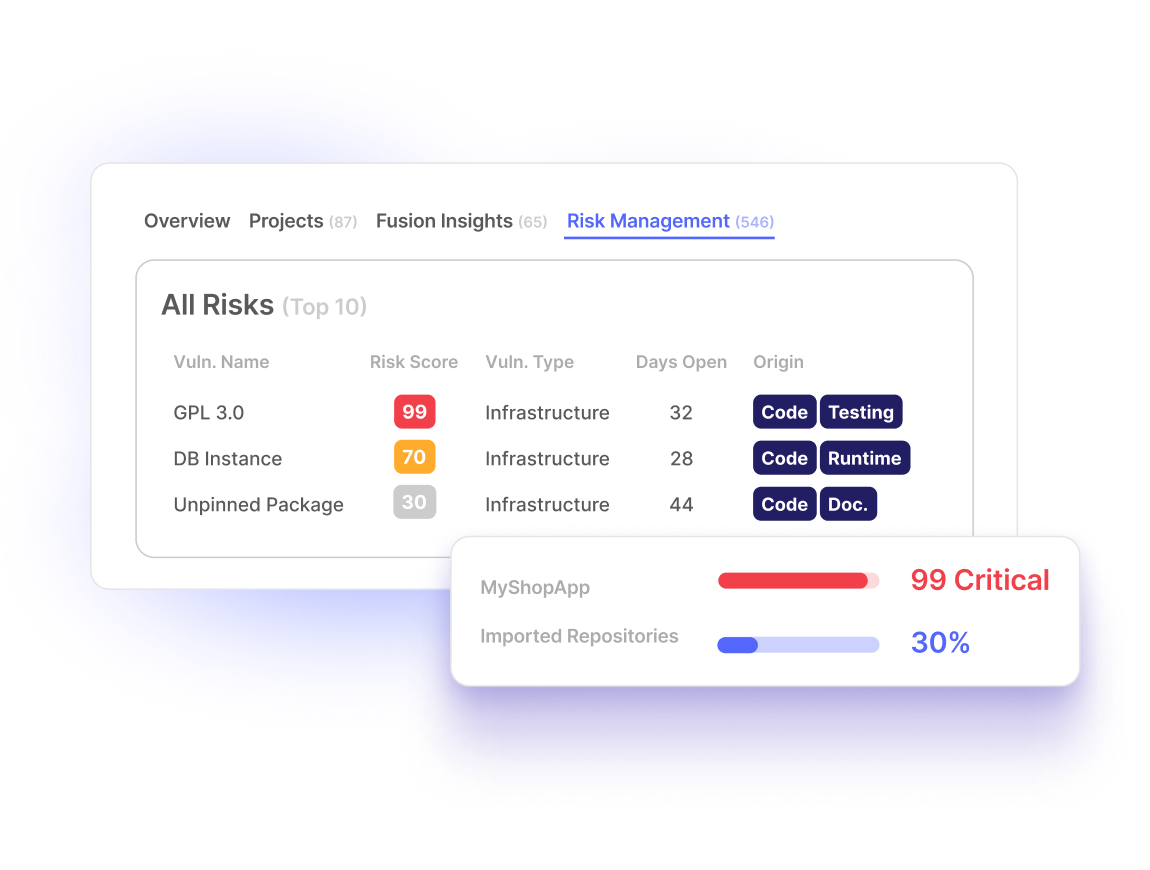
Unified Dashboard With SSO
One dashboard. One log-in. All your AppSec tools, and results, in one place.
Application Risk Management
Provides aggregated scores for each application and ranks them by risk, putting exploitability in the terms of your business.

Accelerate Time to
Value with Services
Checkmarx offers comprehensive professional services to help you build, refine, and manage your AppSec program; and, to maximize the benefits you get from the platform. No matter what stage of maturity your AppSec program is in, Checkmarx has the expertise that you need to be successful.

Learn more about Checkmarx One
Experience the cloud-native enterprise AppSec Platform.
AppSec Education Matters
Discover the power of Codebashing, where AppSec education is specifically crafted for developers. Our approach offers tailored, role-specific learning that ensuring your team is not just educated, but empowered to apply their application security knowledge.
Improve
software quality
When you give developers the knowledge and tools to write high-quality, secure code, they will be able to create innovative and secure applications.
Reduce
vulnerabilities
Train developers to recognize and mitigate security risks effectively, which reduces the chances of inadvertently introducing vulnerabilities into their code.
Faster
time-to-market
By helping your developers write secure code from the start, you’ll see accelerated software development and secure software delivery.
Mitigate API Risk Faster
Discover and assess APIs everywhere – throughout the lifecycle, in documentation, source code, and dynamic testing – to address risks efficiently.
Prioritized Remediation
Focus your AppSec teams and developers on the most critical issues, by prioritizing API vulnerabilities based on their business value and risk.
What Our Customers Say
Customers who chose Checkmarx over others
“Checkmarx One definitely checks all my boxes from a security standpoint and has a great interface that’s engaging and easy to use. Some of the solutions we considered were more complicated. With Checkmarx One, it’s easy to get right to the problem with little to no learning curve.”
Cybersecurity and Networking Manager
The Forrester WaveTM: Software Composition Analysis, Q2 2023
"After reviewing the Checkmarx platform, I’m not sure how Veracode is able to exist while being at a similar price point."

Cybersecurity and Networking Manager
“Incorporating Checkmarx's technology has revolutionized our development culture. It's more than just technology; it serves as the foundation of our security strategy, ensuring that our applications are secure by design.”

Sr. Director, Product Security Engineering

The Forrester WaveTM: Software Composition Analysis, Q2 2023
“The success of our AppSec program can be directly attributed to the tooling, processes and support provided by Checkmarx managed services. Our mission revolves around providing secure and compliant lottery and gaming applications and services to our clients around the globe, and with Checkmarx SAST, SCA and associated components enhanced by their stellar service support, we deliver on this promise with confidence and certainty.”

Head of Information Security

The Forrester WaveTM: Software Composition Analysis, Q2 2023
“After nearly nine years of using Checkmarx's SAST, CGI's journey has been one of seamless integration and consistent satisfaction. The last three years have been particularly smooth, reflecting the solution's reliability and our successful partnership.”

Lead Security Analyst

The Forrester WaveTM: Software Composition Analysis, Q2 2023
"Checkmarx’s execution is impressive; it’s brought all the products under one cloud platform"

Cybersecurity and Networking Manager
The Forrester WaveTM: Software Composition Analysis, Q2 2023
"By Far The Best AppSec Tooling Decision We Have Made!!"

Cybersecurity and Networking Manager
The Forrester WaveTM: Software Composition Analysis, Q2 2023
"We were thrilled to find Checkmarx, which helped us improve the SLA for identifying and remediating risk, reduce risk and the number of vulnerabilities, and eliminate high- and meduim-risk issues."
Tech Lead, Red Team/DevSecOps
The Forrester WaveTM: Software Composition Analysis, Q2 2023
"Checkmarx made security team and developers life easier."

IT Services
The Forrester WaveTM: Software Composition Analysis, Q2 2023
Frequently Asked Questions
Securing your enterprise’s applications effectively is complex. AppSec teams that started with just SAST tools have moved on to owning and managing multiple Application Security Testing (AST) solutions, all aimed at different areas of the software development lifecycle (SDLC). In many cases this has led to companies: needing to manage multiple vendor
contracts, AppSec teams and developers managing multiple log-ins and learning different systems, and teams needing to manually corelate disparate sets of data from entirely different sources. An AppSec platform should help make everyone’s job easier and reduce TCO through fewer tools to learn and manage, as well as through automatically correlated results.
Checkmarx One is an enterprise AppSec platform, and provides flexible, competitive pricing to meet the demands of the market. For more information, please contact our sales team.
Checkmarx One Provides a true unified AppSec experience where you can see all vulnerabilities in one place, manage with one process, and integrate seamlessly into one DevSecOps workflow. For more information on how to get more, check out our whitepaper.
With our quick start guide you can start your first scan in minutes. Our team of dedicated experts will work with you to make certain that your team has everything it needs set up properly to make your AppSec program a success.
Most likely! Checkmarx understands that while the steps in the SDLC are the same everywhere, how each company approaches it from a technology and process standpoint is different. In the end, you need an AppSec platform that works the way you do. That’s why Checkmarx focuses on integrating with all the tools, both new and legacy, that you and your developers use to do your jobs:
CI/CD – Automate scanning as part of your
CI/CD Pipeline
Development Frameworks – Support your
development teams in how they work together with support for 100+ development frameworks
Feedback Tools – Give your developers the necessary context to find and fix vulnerabilities, within their existing workflow, with our industry-leading support tools.
IDE – Enable developers to review and fix vulnerabilities in their preferred IDE.
Programming Languages – Checkmarx One
offers out-of-the-box support for 50+ languages
SCM Integrations – Automate scanning as code is checked in, enabling your team to shift
even further left
Reduce Risk From the Start
Fixing a software problem in production is 100x more costly than fixing during the design phase, and 15x more than during coding.
Get started with Checkmarx One today
Checkmarx One has everything you need to build a world class enterprise application security program
Related Resources

White paper
A Guide to Modern API Security
Understand the challenges in securing your API footprint
White paper
The Checkmarx Approach to API Security
See how a shift-left approach to API security can help you secure shadow and zombie APIs

Solution Brief
Checkmarx One: Enterprise Application Security Platform
Discover the benefits of consolidating your AppSec solutions on a single platform
White paper
Get More Out of AppSec Consolidation
Find out how to consolidate your security tools with an enterprise AppSec platform that prioritizes what matters most

Case Study
Forrester’s Total Economic Impact of Checkmarx One
Discover how Checkmarx One can positively impact your organization’s AppSec and bottom line.