Any organization with aspirations to do business with the U.S. Department of Defense will rapidly familiarize itself with the recently introduced Cybersecurity Maturity Model Certification (CMMC).
What is CMMC and how does it affect organizations?
CMMC was designed to protect DoD intellectual property and sensitive information held by an estimated 300,000 prime and sub-contractors in the Defense Industrial Base, against exposure due to cybersecurity breaches. By stipulating those third-party contractors evaluate all companies competing for DoD contracts on specific CMMC certification requirements, the DoD aims to improve the resilience and security of its software supply chain and improve its posture against cyber threats. CMMC helps apportion compliance and responsibility throughout complex ecosystems that support a variety of functions.
The CMMC framework consists of maturity process assessment and cybersecurity best practices from multiple cybersecurity standards, including DFARS and NIST SP 800-171, which many organizations will already know. Methods are measured in five levels, ranging from “Basic Cybersecurity Hygiene” (Level 1) to “Advanced/Progressive” (Level 5), while assessments of process score from “Performed” at Level 1 to “Optimized” at Level 5. The DoD expects contractors to continuously improve and reach the required standard in practices and processes to be certified compliant with a level.
Within the framework, there are 17 domains in which contractors must demonstrate that they are implementing the best practices and processes:
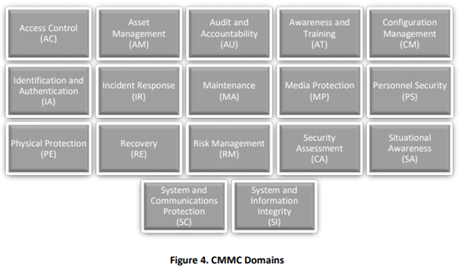
Source: CMMC version 1.02
CMMC is currently amid a lengthy implementation process, with the full roll-out planned for 2026. This imminent timeline requires organizations need to prepare now.
For most organizations in today’s software-centric environment, this will entail evaluating their application security in the context of the relevant domains in the framework – including Security Assessment, Awareness and Training, and Risk Management – and putting in place a progression plan. As specialists in helping organizations deliver secure applications at the pace modern business requires, Checkmarx is a valuable tool that helps organizations elevate their software development program to provide security confidence at the levels needed to satisfy the higher levels of CMMC.
Our security and compliance experts have five strategic and tactical suggestions to help organizations elevate their approach to secure software development, so it supports CMMC compliance:
1. CMMC compliance is a marathon, not a sprint
CMMC compliance is not achievable overnight. Organizations need to look at application security issues from a technical and management perspective and adopt a strategic approach to investing in resources to implement the necessary changes. Organizations will need to initiate the transition from DevOps to DevSecOps or continue to optimize if they’ve already embedded application security within their DevOps program.
2. Get board-level buy-in to security culture change
The implementation of this program is the DoD is signaling its desire for a culture change that makes software vendors security-first. Prospective DoD suppliers will need to embrace the opportunity to make cybersecurity a strategic, fully integrated business objective, requiring board-level champions to foster a top-down security culture. Leadership must communicate and demonstrate that software security is more than a risk and compliance issue; it is a quality issue fundamental to your authorization to operate (ATO).
3. Assess your current AppSec maturity and threat exposure using Open SAMM & OWASP Top Ten
Before you can build a program of activities to support CMMC compliance, you need to benchmark your current position. For example, NIST SP 800-171 Rev. 2 compliance is comparable to CMMC Level 3. However, earning high certification levels won’t be as simple as mapping one compliance program to CMMS.
The Open Software Assurance Maturity Model (SAMM) is an excellent place to start in terms of self-assessing your software security assurance. This model splits an AppSec program into five vertical sectors and in each detail the specific practices you need to adopt to be operating at levels 1, 2, 3, or 3+. There are helpful online assessment tools available to help you determine where you sit on the AppSec spectrum and guide how to progress. By mapping these to the relevant domains of the CMMC framework, organizations can create an AppSec-specific plan related to CMMC.
In conjunction with assessing program maturity, the OWASP Top Ten is the best place to identify application security threats. Organizations need to evaluate risks, accounting for the potential impact of a breach, in the context of their specific industry and business. This assessment informs a prioritized risk mitigation plan, remediating vulnerabilities that matter most, rather than overwhelming the AppSec and developer teams by trying to remediate it all.
4. Leverage partner power to meet CMMC requirements
Organizations should find that their service providers and strategic partners are proactive about supporting CMMC compliance, and they can leverage this as a shortcut. For example, AWS is close to earning its certification, which, in turn, provides AWS customers with those exact compliance requirements.
Adding Checkmarx to scan applications before they’re deployed and monitored in AWS cloud environments can be a shortcut, too, when it comes to achieving higher maturity levels. If organizations regularly test all code- whether custom, open source, or Infrastructure as Code (IaC)- by embedding and automating scans throughout the SDLC, they can identify and support developers in fixing vulnerabilities faster and before production. Checkmarx integrates into developers’ preferred environments, orchestrating the kick-off of scans pulling results directly into their UI.
Check out Checkmarx’s partnership and integrations with AWS >>
To reach the higher maturity levels, organizations also need to implement secure coding standards, train developers regularly, share commonly found vulnerabilities across the organization, and provide evidence that this is complete. Checkmarx enables this through the CxCodebashing Secure Coding Education (SCE) platform that delivers just-in-time, bite-sized lessons that relate directly to the issues developers face in their code.
5. Break down the security silo
When planning for CMMC compliance, it is essential to step outside of the security function and engage with developers to find out how they are using the security tools. If compliance teams make assumptions about how developers use tools and write policies accordingly, their attestations may not match reality, which will cause problems during third-party certification.
How Checkmarx supports CMMC compliance ambitions
Any organization implementing change in its AppSec approach and culture will come back to three key challenges. How to ensure new processes and tools that support the process are adopted, leverage automation to lift the burden of compliance from the developers at the coal face, and remediate the vulnerabilities identified by the new approach.
Checkmarx application security solutions are designed for easy adoption by developers as they fit seamlessly into their preferred environment and deliver value without interrupting workflow. In terms of automation, they require minimal work for the organization to integrate. Once in place, scans are fully automated at the most appropriate points of the SDLC, with results prioritized for accuracy and relevance to avoid creating alert fatigue. Checkmarx provides best-fix locations to facilitate more accessible remediation and keep the momentum flowing through the SDLC when vulnerabilities are discovered.
In combination, Checkmarx solutions support CMMC compliance activities by helping the organization move along the DevSecOps maturity scale to embed security throughout the SDLC and ensure that code is of the highest quality, appropriate to an organization aiming to win contracts with the U.S. Department of Defense.
Is your organization set up for success in winning deals with the Public Sector?
Check out these resources for how government agencies are modernizing their approaches to Application Security Testing. Browse now >>
Download our Ultimate Guide to SCA here.







