More and more organizations are ditching the traditional sequential processes (i.e – Waterfall) for iterative development methodologies. This commonly involves Agile and DevOps methods, which are based on continuous delivery of software based on customer feedback. But traditional AppSec solutions are not ideal for these setups due to their inherited deficiencies. This is where Static Code Analysis (SCA) enters the picture.
The modern Software Development Life Cycle (SDLC) typically involves 6 stages:
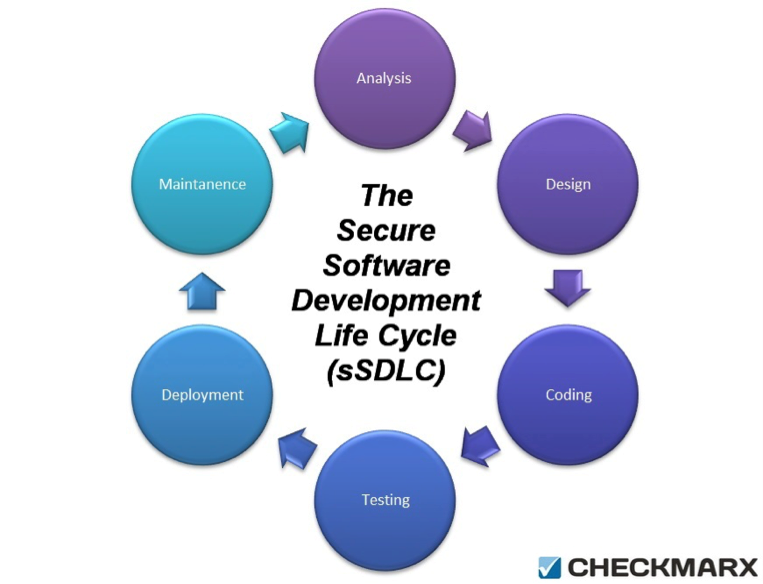

- Analysis – Establishing a high-level gameplan for the development process.
- Design – Preparing the software design as per the requirements.
- Coding – This is where the magic happensand developers write the code.
- Testing – Introduction of various QA procedures and security testing.
- Deployment – At this stage, the application is released and used by the customer.
- Maintenance – Elimination of reported bugs/vulnerabilities with patches/updates.





