On March 29th, 2022, two separate RCE (Remote Code Execution) vulnerabilities related to different Spring projects were published and discussed all over the internet. In addition, a third vulnerability in a Spring project was disclosed - this time a DoS (Denial of Services) vulnerability. There were also some rumors regarding an unconfirmed deserialization weakness in Spring Core, that could lead to an RCE.
Overview of Spring Vulnerabilities
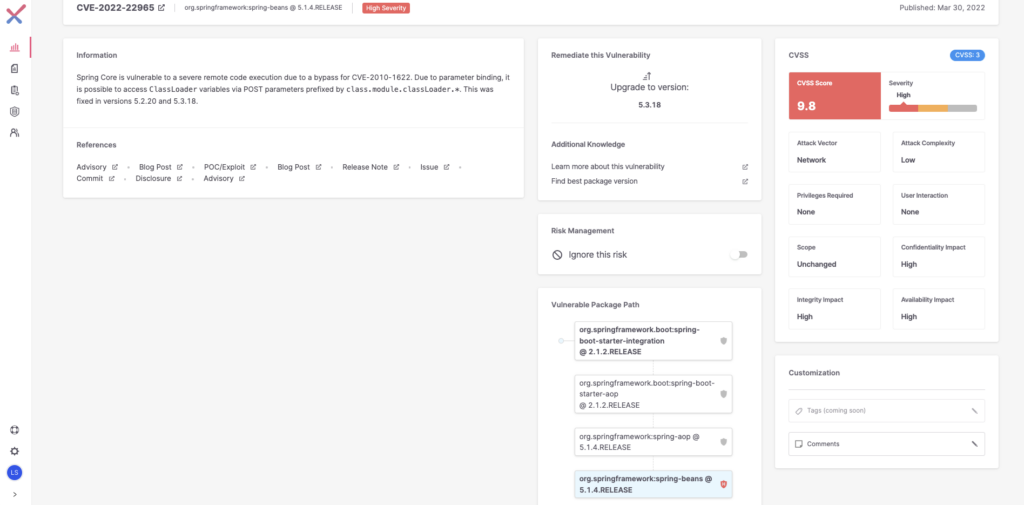
- CVE-2022-22965: “SpringShell”: RCE in org.springframework:spring-beans or org.springframework:spring prior to 5.3.18 and 5.2.20.
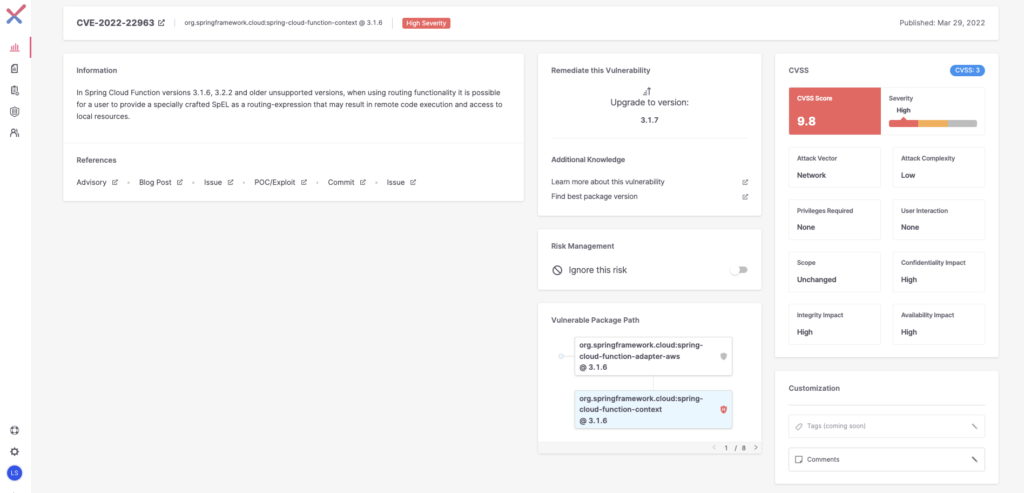
- CVE-2022-22963: RCE in org.springframework.cloud:spring-cloud-function-context prior to 3.1.7, and 3.2.3.
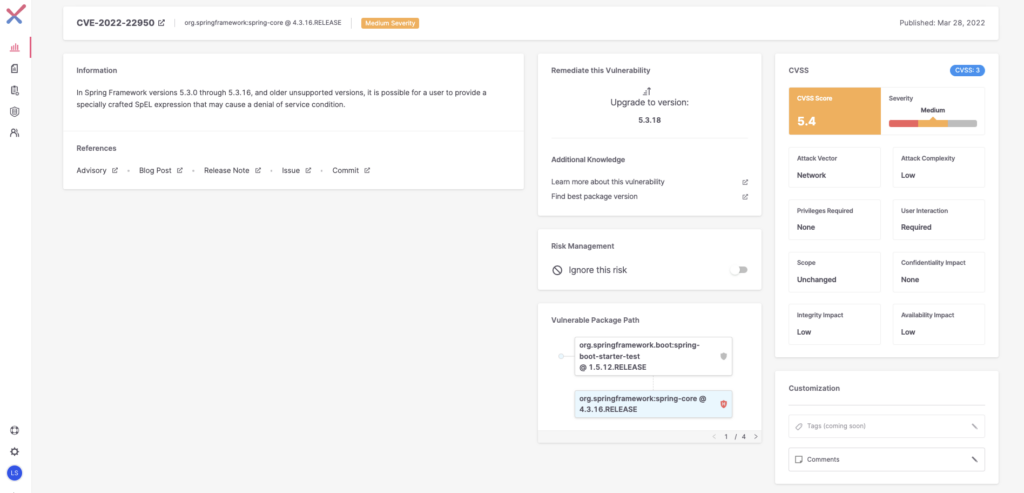
- CVE-2022-22950: DoS Vulnerability in org.springframework:spring-expression prior to 5.3.17.
Details of CVE-2022-22965 ("SpringShell")
A spring framework application running on JDK 9+ may be vulnerable to remote code execution (RCE) via data binding. The specific exploit requires the application to run on Tomcat as a WAR deployment. If the application is deployed as a Spring Boot executable jar, i.e., the default, it is not vulnerable to the exploit. However, according to Spring’s latest updates, the nature of the vulnerability is more general, and there may be other ways to exploit it. Due to parameter binding it is possible to access “ClassLoader” variables via POST parameters, through “class.module.classLoader”, thus being able to write a malicious JSP file and achieve remote code execution. More details here.
The vulnerability was fixed by restricting the property paths under “Class” and properties of types “ClassLoader” or “ProtectionDomain”.
Prerequisites: JDK 9 or higher, Apache Tomcat as the Servlet container, Packaged as WAR.
Affected Versions: org.springframework:spring and org.springframework:spring-beans prior to 5.3.18 and 5.2.20.
Vulnerable Code: The vulnerability is found in the file CachedIntrospectionResults.java, specifically in two methods: CachedIntrospectionResults and introspectInterfaces.
Please note - Some sources online describe this vulnerability as affecting Spring MVC or Spring WebFlux. However, this is true only transitively as they all use the package spring-beans which is, as detailed above, the vulnerable package itself.
Mitigations: Spring Framework versions >= 5.3.18 and >= 5.2.20
PoC (Proof of Concept):
Fix Commit: https://github.com/spring-projects/spring-framework/commit/002546b3e4b8d791ea6acccb81eb3168f51abb15
Details of CVE-2022-22963
In Spring Cloud Function versions 3.1.6, 3.2.2 and older unsupported versions, it is possible for a user to provide a specially crafted SpEL as a routing-expression that may result in access to local resources, when using routing functionality. The vulnerability was fixed by ensuring that any SpEL expression provided via Message Headers is not evaluated in the scope of StandardEvaluationContext (see commit dc5128b).
Affected Versions: org.springframework.cloud:spring-cloud-function-context in versions 3.1.6, 3.2.2 and older, unsupported versions.
Vulnerable Code: The vulnerability is found in the file RoutingFunction.java, specifically in two methods: route and functionFromExpression.
Mitigations: Users of affected versions should upgrade to 3.1.7, 3.2.3. No other steps are necessary.
PoC (Proof of Concept):
Details for CVE-2022-22950
In Spring Framework versions 5.3.0 through 5.3.16 and older, unsupported versions, it is possible for a user to provide a specially crafted SpEL expression that may cause a denial-of-service condition. This is performed by attempting to create a large array in a SpEL expression that will result in an OutOfMemoryError. The vulnerability was fixed (see commit 90cfde) By evaluating the size of the array creation and throwing a SpelEvaluationException exception whenever it is exceeding a predetermined threshold.
Affected Versions: org.springframework:spring-expression 5.3.0 through 5.3.16 and older, unsupported versions are also affected
Vulnerable Code: The vulnerability is found in the file RoutingFunction.java, specifically in the createArray method.
Mitigations: Users of affected versions should upgrade to => 5.3.17. No other steps are necessary.
The reporter of this vulnerability posted a blog post explaining all you need to know.
Detecting Spring Boot vulnerabilities and future variants with Checkmarx SCA
Checkmarx SCA™ solution enables organizations to address open-source security issues earlier in their SDLC and reduces manual processes by scanning your code and identifying the security risk it contains, so you can deliver secure and compliant software faster, and at scale.
Checkmarx SCA™ also provides SBOM (Software Bill of Materials) automation at scale, which seems like the need of the hour for anyone that uses open-source code in their organization.






