Application Security (AppSec) personnel have a tough job these days trying to secure their applications. Many organizations take a fragmented approach to AppSec and scan engines; they may use one vendor for static application security testing (SAST), another for software composition analysis (SCA), and yet another for scanning and securing their Infrastructure-as-Code (IaC) configuration files. Three different software suites to configure, three different interfaces with which to interact, and at least three different scans to analyze the results. Not to mention that the results are independent of each other with no way to integrate or correlate into one cohesive analysis.
That’s where Checkmarx Fusion comes in.
Checkmarx Fusion, an element of our Checkmarx One™ Application Security Platform, helps you see all of your scan results on one easy-to-read dashboard. Checkmarx Fusion maps the threats in a visual, intuitive graph containing all software elements, consumed cloud resources, and relationships among them. It extrapolates potential vulnerabilities within two or more scans that might otherwise escape detection. Fusion also adds context to the different scanners by combining and correlating results from static code scans and runtime scans, significantly minimizing false positives.
Let’s take a look underneath the hood at how this process works.
Fusion works with applications and currently supports Java and C# code with Terraform files and AWS, with a roadmap to support additional languages and public cloud providers. As you can see below in Figure 1, there are two applications defined in this instance of the Checkmarx One Platform, one named the “Shopping App,” and another named “Bank.”
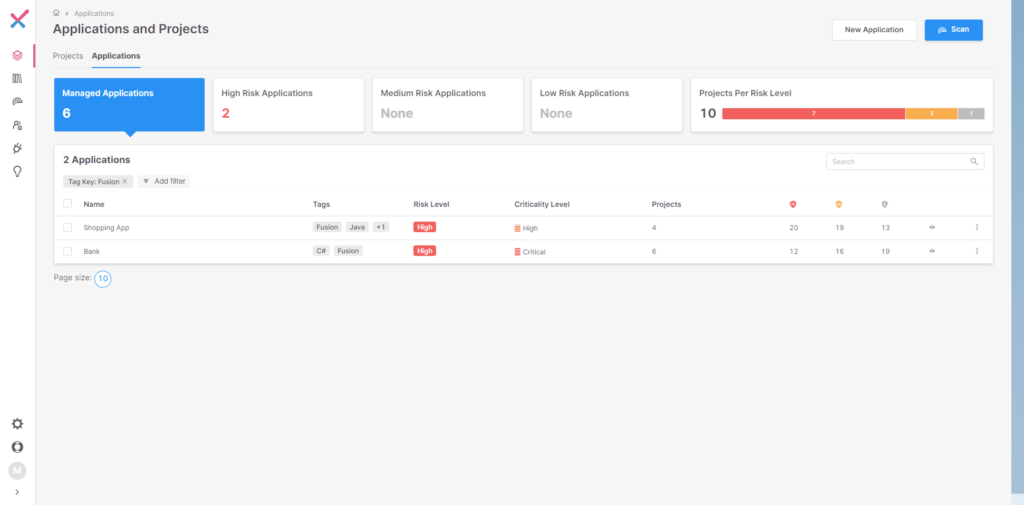
Figure 1 Checkmarx One Application and Projects
Clicking on the “Shopping App” Java-based application shows four microservices tied to this application, such as managing users and shipping.
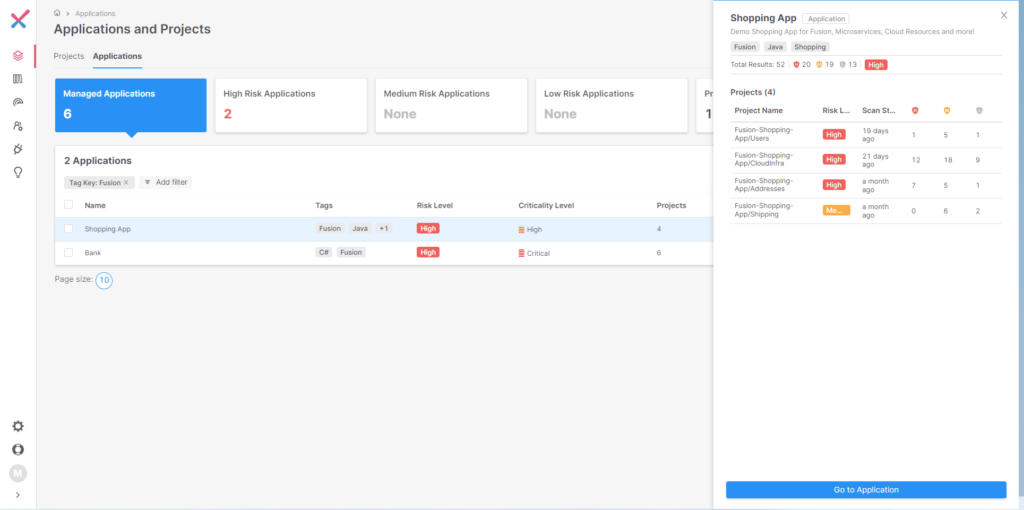
Figure 2 Microservices Tied to the Shopping App
Selecting the “Go to Application” button near the bottom of the page in Figure 2 brings us to the “Shopping App” scan overview page. This page shows information on the most recent scan of this application, such as the number of vulnerabilities found and an aging report on previous findings.
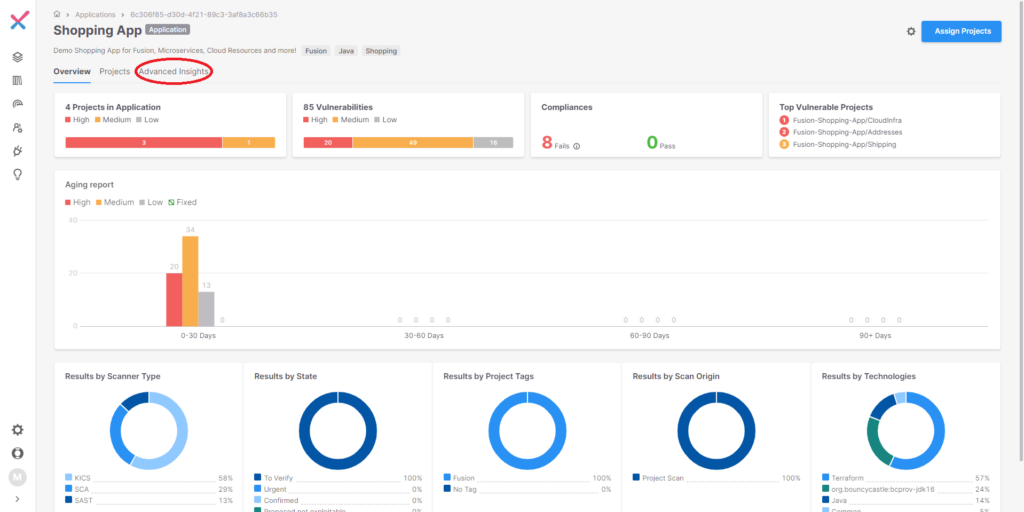
Figure 3 Shopping App Scan Overview
Clicking on the “Advance Insights” link, indicated by the red circle in Figure 3, brings us to the new Fusion correlation engine. There are two views available, the first being a topographical model as seen in Figure 4 below.
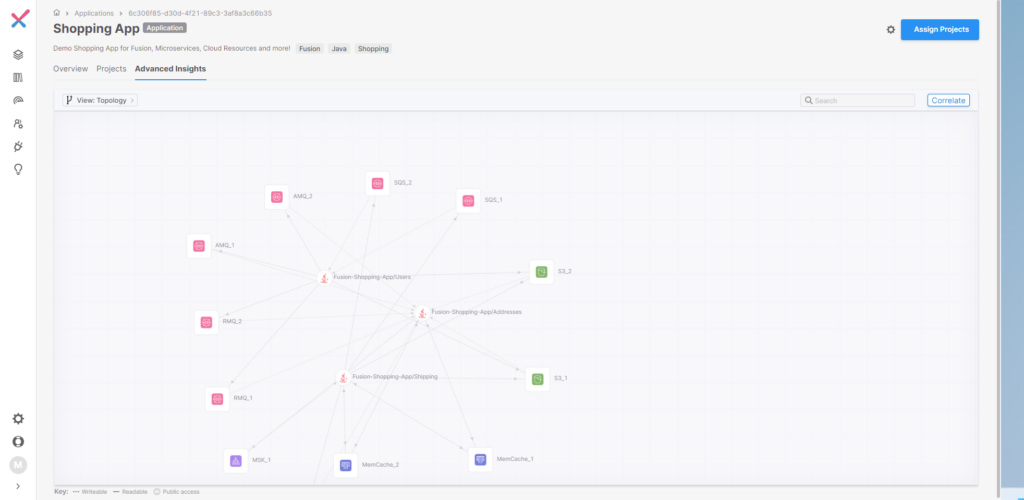
Figure 4 Fusion Topographical Map
This view shows a model indicating how services interact with each other. For instance, clicking “Shipping Microservice” shows which cloud-based infrastructure this microservice is interacting with, such as two Amazon Simple Storage Services (S3_1 and S3_2) and the vulnerabilities found, as seen by Figure 5 below.
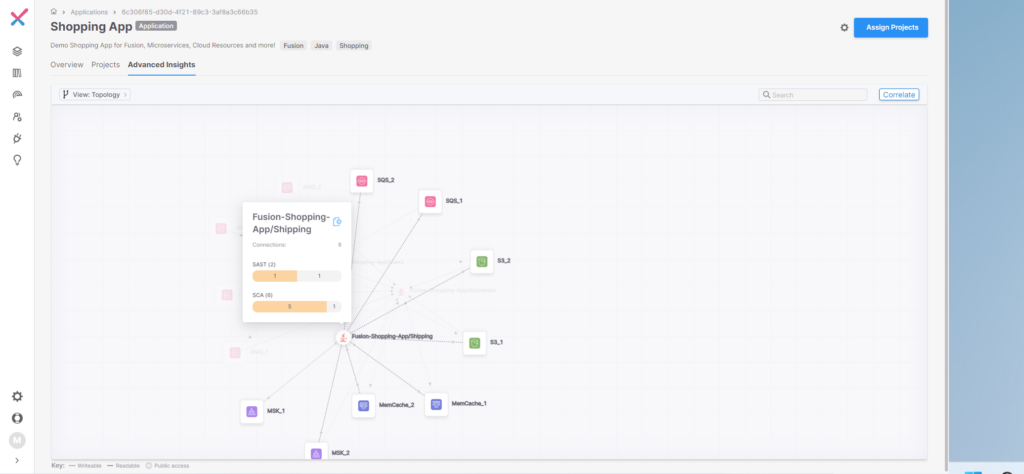
Figure 5 Shipping Microservice
In Figure 5, the blue “next page” icon shows more detail of the state of the microservice and any vulnerabilities found with S3_1 and S3_2, as shown in Figure 6.
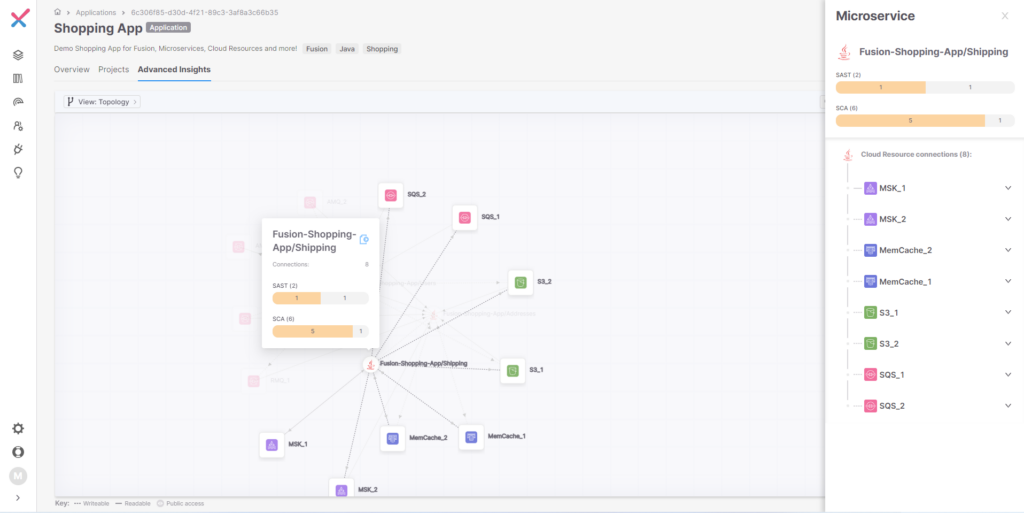
Figure 6 Shipping Microservice Vulnerabilities
The ability to show how microservices and their corresponding cloud-based infrastructure interact is critical to minimizing the vulnerabilities in your cloud-based applications. It allows AppSec users to view and correlate vulnerabilities that could have been missed from individual siloed scan results. This “next-generation” of application security testing will allow companies to have confidence that their application is secure and able to withstand the complexities of modern application development (MAD).
As attackers become more sophisticated in their approach and toolsets, so must AppSec professionals and developers.
To learn more about Checkmarx Fusion and how it works in Checkmarx One, our Checkmarx One™ Application Security Platform Demo Video. To see a live demonstration of Checkmarx Fusion, Request a Demo today!






