CocoaPods is THE dependency manager for iOS and Mac projects. It helps software developers easily add pre-made pieces of code (called “libraries” or “dependencies”) to their iOS or Mac projects. These code libraries can help developers add extra features or functionality to their apps without having to write all of the code themselves. Think of it like adding pre-made Lego pieces to a Lego creation to make it better or more interesting.
Subdomain Hijacking
Subdomain hijacking is a type of cyber attack where an attacker takes control of a subdomain of a legitimate domain, and uses it to host malicious content or launch further attacks.
In a subdomain hijacking attack, the attacker can find forgotten settings on free hosting websites such as GitHub Pages, which are not mapped anymore. The weak validation grants attackers permission to use those subdomains.
CocoaPods Casino
Guy Nachshon, a brilliant security researcher in my team, found out the subdomain cdn2.cocoapods.org was used years ago and abandoned. However, the DNS records still pointed to the GitHub Pages hosting service, and attackers hijacked it to host a fishy casino website.
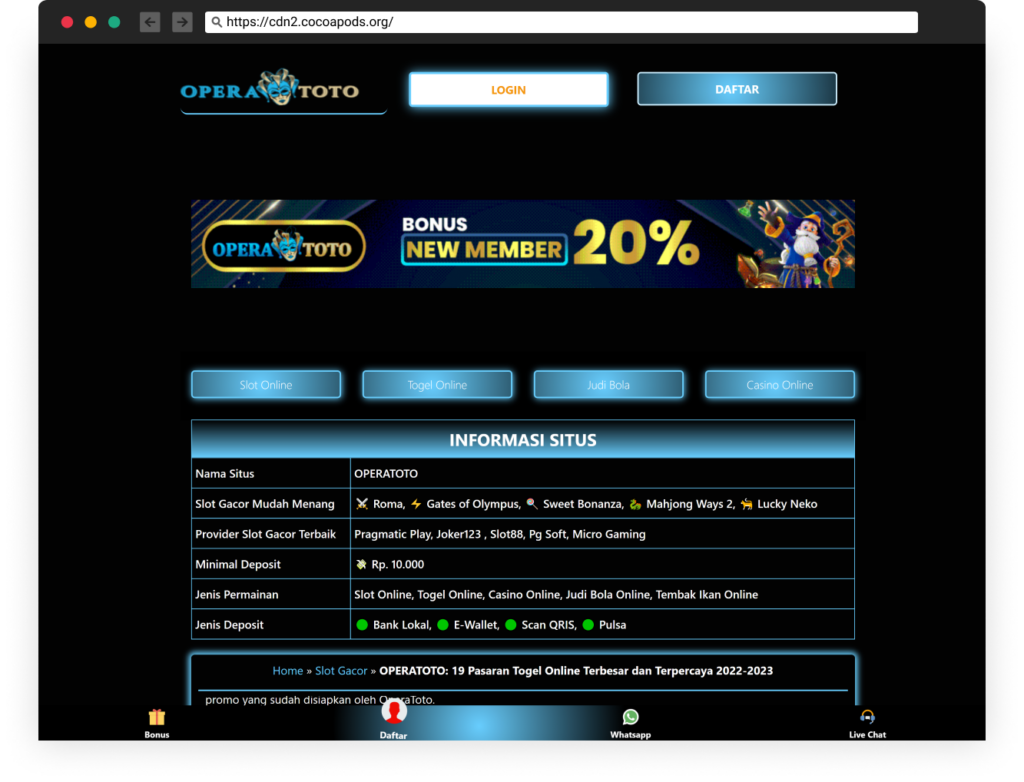
While we were investigating this, the subdomain got freed on GitHub Pages (probably due to an update/mistake of the attackers).
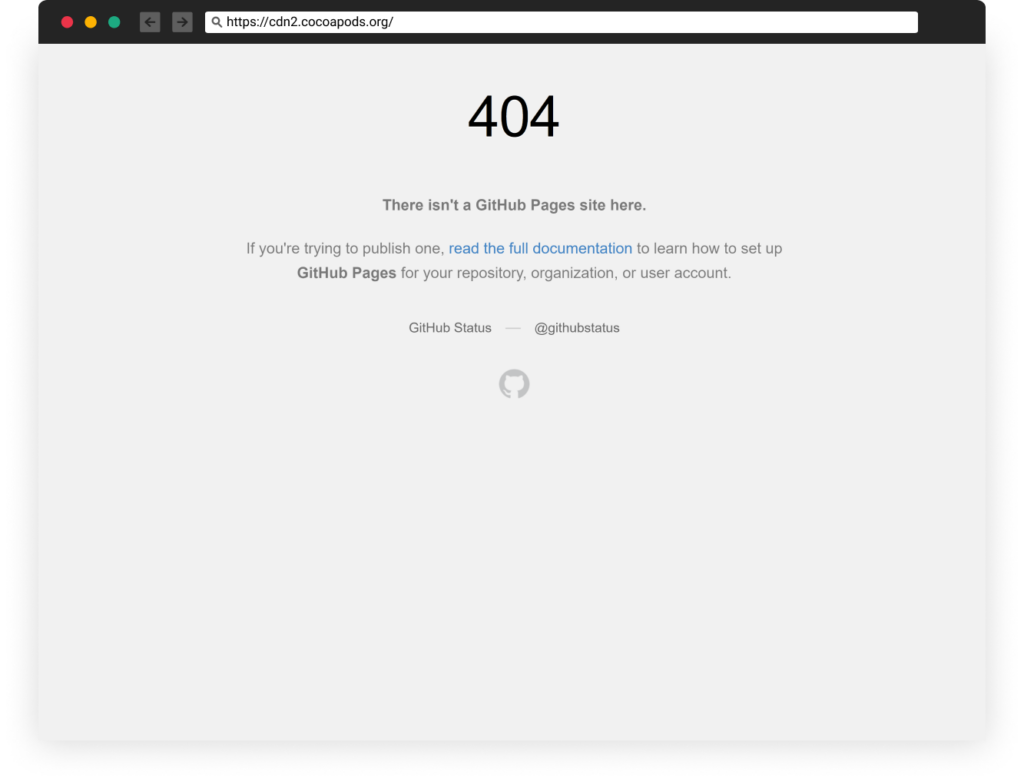
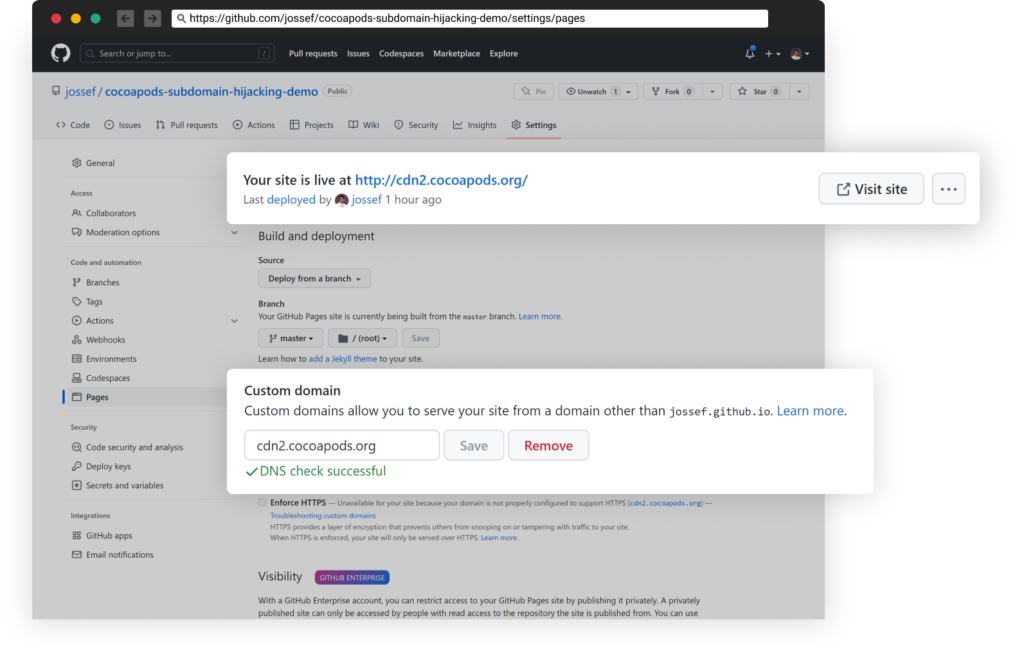
We jumped on the opportunity and created a simple repository to hold this subdomain and prevent another takeover by those casino attackers.
This works as long as the subdomain is unoccupied by another GitHub Pages project and is super simple to set up -> settings, enable GitHub Pages, type the subdomain “cdn2.cocoapods.org”:
Watch this short demo video to see it in action:
Impact
Generally speaking, the impact of hijacking a subdomain of a known website can trick users into thinking the content they are seeing is legitimate and created by the known brand.
Furthermore, organizations usually allow network traffic to such dev-related legitimate resources from sensitive networks to support the engineering process.
Last year, we saw cases in which attackers hosted malicious exe file on GitHub and another example where an image hosted on imgur.com contained malicious python code. Hence, it’s quite clear what’s the potential of hijacking a subdomain of a popular and legitimate brand.
Conclusion
I disclosed the findings to CocoaPods in this GitHub issue, and huge respect for the fast response and removing the subdomain record.
It’s ridiculous how easy it is to take over an abandoned subdomain. This made me wonder – should this be that easy? Should GitHub enforce 2-way validation when linking a domain to a GitHub Pages project? Like validating the exact repository URL? IMHO – yes.
See this case as a warning if you have created subdomain records for side-projects that over time became obsolete, like cdn2.cocoapods.org. I suggest removing them, as someone might hijack your subdomain.






