In an alarming development for the cryptocurrency community, the Ledger Connect Kit, has fallen victim to a sophisticated supply chain attack, resulting in the redirection of users' crypto transactions to a wallet controlled by the attacker. The Ledger Connect Kit is a vital component in the decentralized application ecosystem owned by Ledger - a company that manages billions of dollars.
Key Findings
- NPM Account Takeover: Ledger Connect-Kit was compromised due to npmjs account takeover of a former Ledger employee.
- Affected Versions: Malicious code was injected into versions 1.1.5, 1.1.6, and 1.1.7, resulting in wallet-draining attacks.
- Impact: At this time, over $700,000 has been stolen as a result of this security breach.
- Rapid Mitigation: Ledger swiftly released version 1.1.8 to patch the vulnerability.
Attack Details
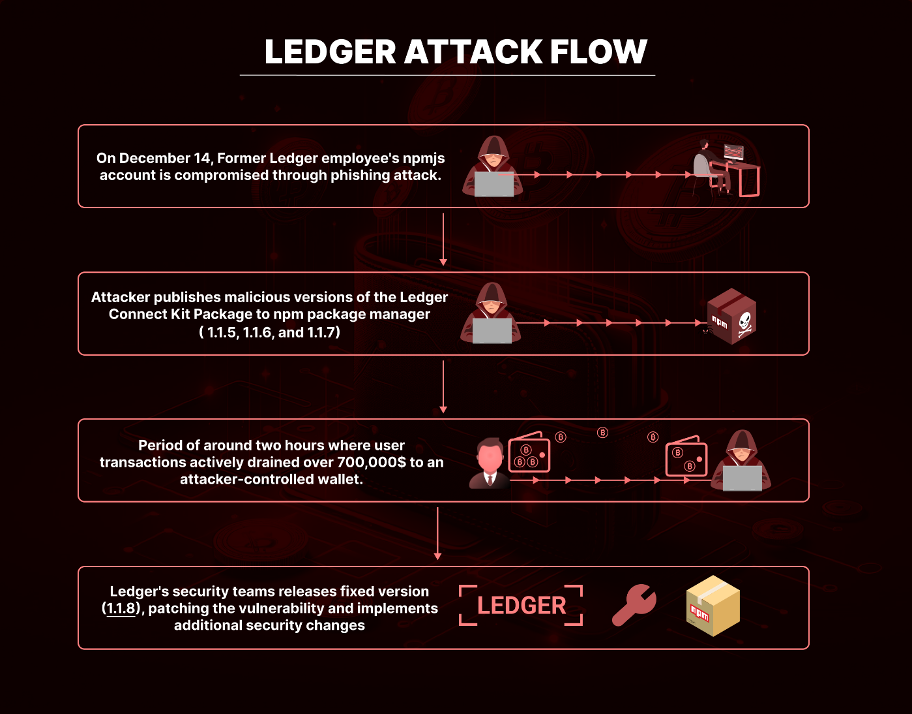
The Ledger Connect Kit, instrumental in linking users' wallets to decentralized applications (dApps), like SushiSwap and Revoke.cash, was compromised when a threat actor took over the NPM account of one of the projects maintainers. The actor then continued to publish multiple new versions of the package, injected with malicious code, that drains the wallets of users. Unsuspecting users that performed transactions unknowingly sent their crypto funds to an attacker-controlled wallet.
The breach targeted versions 1.1.5, 1.1.6, and 1.1.7 of the Ledger Connect Kit NPM Package. These versions were infected with a malicious drainer, that diverted user funds to an attacker-controlled wallet. The compromised package used a rogue WalletConnect project to reroute funds.
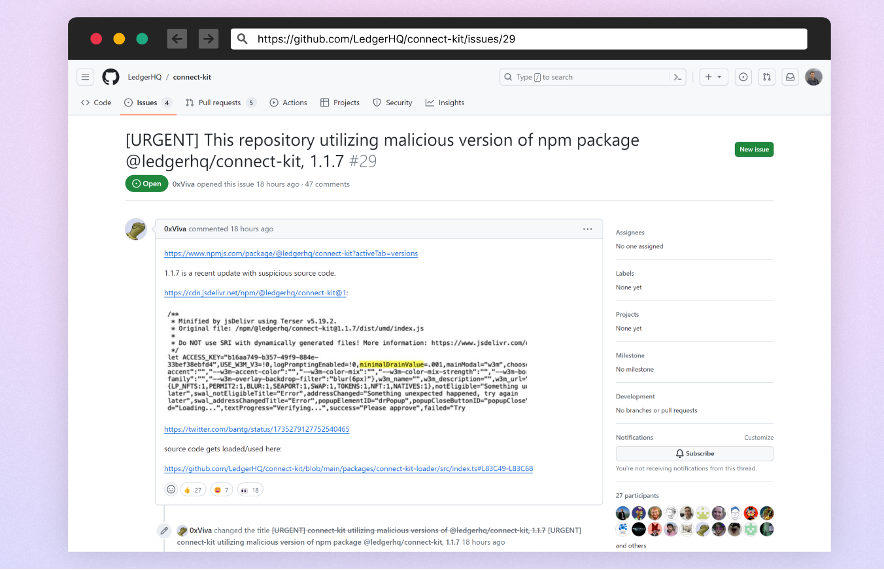
Notifying users of the attack
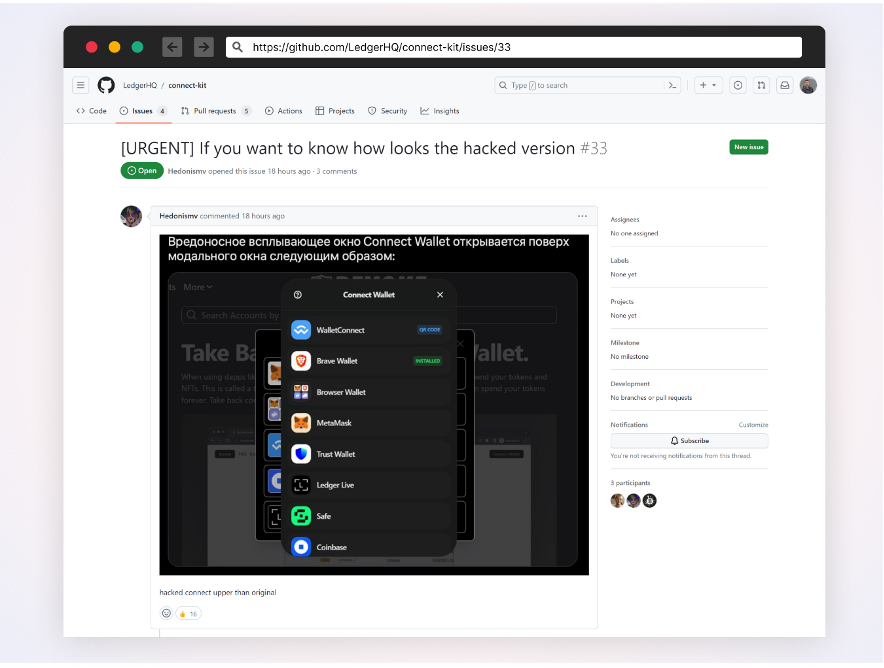
Notifying users of the attack
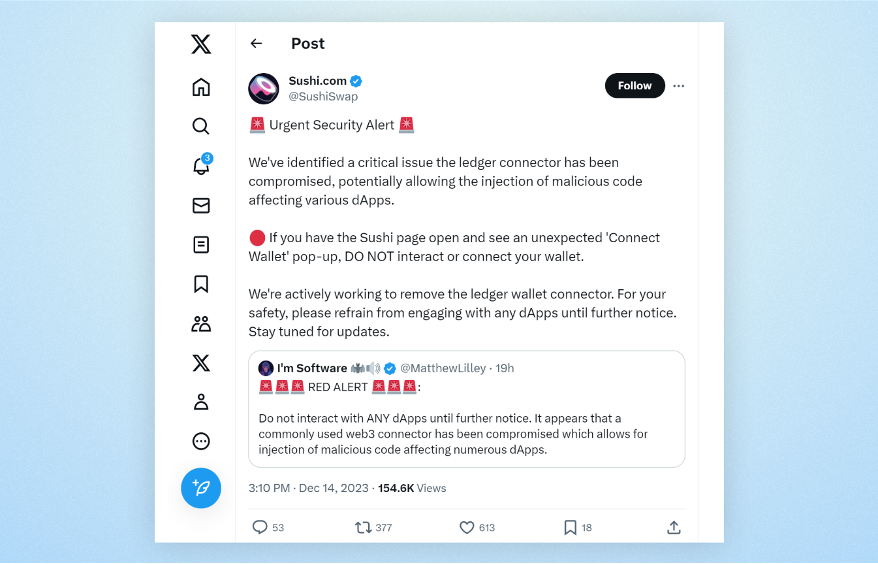
Apps affected, warning their users
Tactic Used: Account Takeover
Central to this attack was a well-crafted social engineering strategy that led to the compromise of a former Ledger employee's npmjs account credentials. This breach then led to unauthorized releases of the Ledger Connect Kit. Account takeovers are particularly dangerous since they allow attackers to bypass many traditional security checks, directly inserting malicious code into trusted software. Phishing attacks against contributors have been a rising trend for more than a year.
A critical, and often overlooked, indicator of such an attack is the discrepancy in package versions between the package manager (npm) and the version control system (Git). We can clearly see in this attack that there were no changes and no tags or releases on the Ledger git corresponding to the malicious versions on the NPM package manager.
When a project works efficiently it maintains consistency between these platforms, with each npm release corresponding to a Git tag. This is either done automatically or manually. However, in this case, the versions released on npm lacked matching tags on Git. This mismatch serves as an indicator of suspicious activity, particularly for projects known for their orderly release processes as seen in previous attack cases.
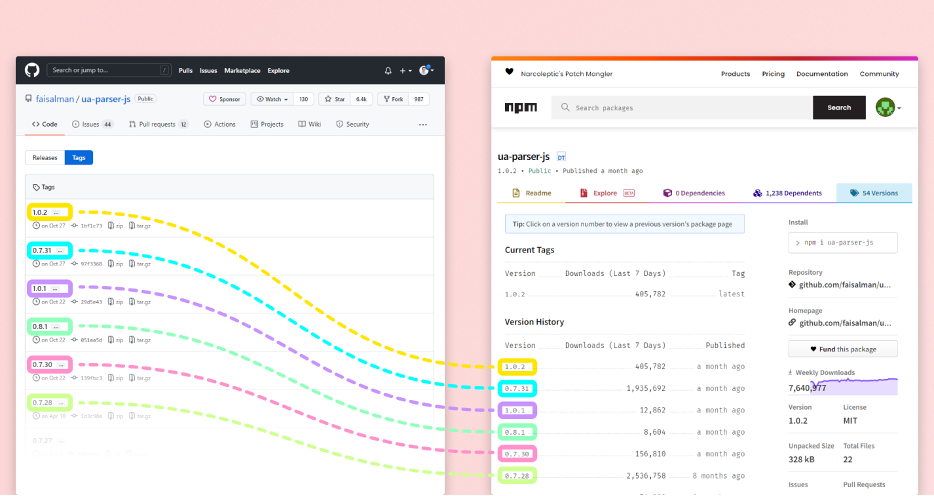
Monitoring for such inconsistencies can be a crucial part of early detection strategies for account takeovers and unauthorized package releases. Tools and practices that keep track of this alignment can quickly flag discrepancies, prompting an immediate investigation and potentially preventing widespread impact.
Rapid Response and Remediation
Upon discovering the breach, Ledger’s team acted swiftly, releasing version 1.1.8 of the Ledger Connect Kit to patch the vulnerability within 40 minutes of detection. Despite their quick response, the malicious versions were active for approximately five hours, with a critical window of less than two hours where funds were actively drained.
Impact
The financial repercussions are becoming increasingly apparent. As of the latest reports, over $700,000 has been stolen due to this security breach.
But I use SBOMs, so I'm good - right?
While a Software Bill of Materials (SBOM) is a critical tool for enhancing transparency and security in software supply chains, its effectiveness is limited in certain types of attacks. An SBOM effectively lists all components used in a software product, but it primarily addresses issues related to known vulnerabilities in these components, not necessarily the security of the distribution mechanism itself.
In the case of the Ledger Connect Kit attack, the primary issue was not with the components themselves but with the compromised distribution process due to an account takeover. The attacker published malicious versions of the package through a legitimate channel, which would not necessarily be flagged by an SBOM. Since the SBOM would list components as usual, it wouldn’t identify the malicious code introduced by the attacker in the compromised versions.
So, while SBOMs are vital for component transparency, they must be complemented with fast, proactive scanning mechanisms that can detect unauthorized changes or malicious activities in real-time, beyond just component listing.
Conclusion
This breach highlights the potential domino effect of a single compromised element in interconnected digital platforms. The reliance on third-party components, adds layers of vulnerability, making every participant in the chain a potential target and contributor to a larger-scale compromise. Therefore, it is crucial to ensure that effective security strategies are in place which involves things like rigorous vetting of third-party components, implementing robust internal security measures, and fostering a culture of cybersecurity awareness.
As part of the Checkmarx Supply Chain Security solution, our research team continuously monitors suspicious activities in the open-source software ecosystem. We track and flag “signals” that may indicate foul play and promptly alert our customers to help protect them.
Checkmarx customers are protected against this attack.






