Malicious Package Examples
The following sections show a few examples of Supply Chain Security threats that are catalogued in our database.
NPM package “node-ipc”
The node-ipc incident occurred in March 2022. A self-corruption of its maintainer who decided to add malware on top of his package to target Russian users and wipe their PC files, to protest against the Russia-Ukraine war.
Read the full media coverage for more information
Request body:
[
{
"name": "node-ipc",
"type": "npm",
"version": "9.2.2"
}
]Response body:
[
{
"type": "npm",
"name": "node-ipc",
"version": "9.2.2",
"risks": [
{
"id": "3fd21b8ebb6337f8b405e084e5f7b8394d10c76a",
"description": "The malicious payload in this package has the ability to corrupt or destroy files on disk\n### About\n\nFile wiping or file destruction is a type of risk which usually done when attackers wish to cause harm. File destruction can be done in several ways such as:\n- Recursively overwriting all files with random / static content\n- Deleting all files\n- Encrypting all files and deleting the encryption key",
"title": "Wiper",
"score": 10
},
{
"id": "7e10f2a9a922871f8cd1098060ce92a20dc6f4b1",
"description": "This package includes functionality which aims to protest or raise an issue and might include undesired behavior.\n### About\n\nSimilar to a malicious package risk, Protestware risk may include malicious functionality [as seen in past incidents](https://checkmarx.com/blog/protestware-politics-and-open-source-software/). Protestware may contain any of the following:\n- Targeted payload\n- DOS\n- SPAM messages\n- Malicious dependencies",
"title": "Protestware",
"score": 5
}, {
"id": "dc877dee62e5a2528e12ce1fdeade0f1c11e197f",
"description": "This package was manually inspected by a security researcher and flagged as malicious\n### About\n\nClassifying malicious packages is an internal process, analysis is done at scale automatically via multiple engines. Once there's a risk suspicion, this is forwarded to a security researcher for a manual evaluation.\n\nAttackers take advantage of the excessive trust in the open-source ecosystem and launch software supply chain attacks in the form of code packages. \n\nThe risk of having a package with a malicious payload is high. It's a common behavior for most of the malicious payloads to execute itself automatically upon installing or using the package. \n\n\n\nWhile some dependency vulnerabilities have the privilege to be kept as known issue due to risk-management, same does not apply in the case of a malicious package, and it should be removed with the highest priority.",
"title": "Malicious Package",
"score": 10
},
{
"id": "a411cf63e1757a4ff8f094e296ef450094389807",
"description": "The Contributor of this package, npm user [riaevangelist](https://www.npmjs.com/~riaevangelist), previously seen corrupting one of his popular package [node-ipc](https://checkmarx.com/blog/protestware-politics-and-open-source-software/) infected with a malicious payload. [Read more](https://checkmarx.com/blog/protestware-politics-and-open-source-software/)\n### About\n\nWe recommend freezing this package's version in your manifest file or consider finding an alternative to this package.\n\nRelying on code from an unreliable contributors could damage the integrity of the code built depends on it. There is a risk this package may be corrupted as well in future versions.",
"title": "Historical Unreliable User Contribution",
"score": 4
}
]
}
]NPM package “momnet”
momnet is a malicious package. The library pretends to be the popular moment library, which is used in generating timestamps in different time-zones and formats for front-end projects. The malicious package is almost identical to the original library. The only difference is that it employs a different, crafted moment.min.js file of an unknown origin, rather than the library's own source.
Read the full media coverage for more information
Request body:
[
{
"name": "momnet",
"type": "npm",
"version": "2.29.1"
}
]Response body:
[
{
"type": "npm",
"name": "momnet",
"version": "2.29.1",
"risks": [
{
"id": "186b88f11f02aebce3dd34bd7b8bb74eedf62024",
"description": "This package name is similar to other popular package \"moment\"\n### About\n\nTyposquatting attacks relies on user type errors being inputted into installation commands or manifest files. \n\nFor example, let's take the popular npm package [moment](https://www.npmjs.com/package/moment) which has tens of millions of weekly downloads.\n\nA user would like use this package and assisting the `npm install` command like so:\n```\nnpm install moment\n``` \nHowever, sometimes users tend to do accidentally typos, so another user would write: \n```\nnpm install momnet\n```\n\nIn this case, if a package exists under the Typosquatting name, it will be fetched and used.\n\n\n\n\nAttackers find this method effective and usually tend to copy the original functionality and metadata to avoid detection. Typosquatting is one way to mislead developers to download the wrong package and usually includes with a malicious payloads.",
"title": "Typosquatting",
"score": 8
},
{
"id": "745d54931db73d31470ac8774ea45a79903dab0c",
"description": "This package was manually inspected by a security researcher and flagged as malicious\n### About\n\nClassifying malicious packages is an internal process, analysis is done at scale automatically via multiple engines. Once there's a risk suspicion, this is forwarded to a security researcher for a manual evaluation.\n\nAttackers take advantage of the excessive trust in the open-source ecosystem and launch software supply chain attacks in the form of code packages. \n\nThe risk of having a package with a malicious payload is high. It's a common behavior for most of the malicious payloads to execute itself automatically upon installing or using the package. \n\n\n\nWhile some dependency vulnerabilities have the privilege to be kept as known issue due to risk-management, same does not apply in the case of a malicious package, and it should be removed with the highest priority.",
"title": "Malicious Package",
"score": 10
},
{
"id": "8c7e99081f013f9fdc43bed8c71b287c2c8e67d6",
"description": "There is a weak link between the package's listed metadata and the referenced Git repository \"https://github.com/moment/moment\"\n### About\n\nPackage managers often display traction statistics per code package based on it's related GitHub repository. This statistics helps developers to evaluate code packages.\n\n\n\nThe statistics displayed by the package managers do not go through any validation process. It can easily be falsified to mislead developers because of how this information is acquired.\n\n\nAs part of the package metadata analysis capabilities Checkmarx has, StarJacking engine verifies the authenticity of such Git repository references and in case it's a false reference, this risk is shown",
"title": "StarJacking",
"score": 5
}
]
}
]NPM package “small-sm”
On July 26 2022, SecureList by Kaspersky identified four suspicious packages. All these packages contained highly obfuscated malicious Python and JavaScript code. The Python malware is a modified version of an open-source token logger called Volt Stealer. It is intended to steal Discord tokens from infected machines, along with the victim’s IP address, and upload them via HTTP.
Read the full media coverage for more information
Request body:
[
{
"name": "small-sm",
"type": "npm",
"version": "8.2.0"
}
]Response body:
[
{
"type": "npm",
"name": "small-sm",
"version": "8.2.0",
"risks": [
{
"id": "2be17b0c7d3f93b5388a0b149c120a3e9d1391e9",
"description": "This package exfiltrates computer and operating system information\n### About\n\nData exfiltration may be done in numerous ways such as through HTTP requests, DNS tunneling, various webhooks and more. It is common by attackers to try to exfiltrate sensitive information such as:\n- Credentials\n- Environment variables\n- SSH keys\n- Authentication tokens\n- Computer and operating system information\n- Network settings\n\n",
"title": "Data Exfiltration",
"score": 6
},
{
"id": "6f1cb117022d043a204b6fd7d03d4d740cacdc21",
"description": "This package exfiltrates sensitive data to a remote location\n### About\n\nData exfiltration may be done in numerous ways such as through HTTP requests, DNS tunneling, various webhooks and more. It is common by attackers to try to exfiltrate sensitive information such as:\n- Credentials\n- Environment variables\n- SSH keys\n- Authentication tokens\n- Computer and operating system information\n- Network settings\n\n",
"title": "Data Exfiltration",
"score": 8
},
{
"id": "cffbd25249ca13b36bbc009a4769b99eb26d3cd2",
"description": "This package was manually inspected by a security researcher and flagged as malicious\n### About\n\nClassifying malicious packages is an internal process, analysis is done at scale automatically via multiple engines. Once there's a risk suspicion, this is forwarded to a security researcher for a manual evaluation.\n\nAttackers take advantage of the excessive trust in the open-source ecosystem and launch software supply chain attacks in the form of code packages. \n\nThe risk of having a package with a malicious payload is high. It's a common behavior for most of the malicious payloads to execute itself automatically upon installing or using the package. \n\n\n\nWhile some dependency vulnerabilities have the privilege to be kept as known issue due to risk-management, same does not apply in the case of a malicious package, and it should be removed with the highest priority.",
"title": "Malicious Package",
"score": 10
}
]
}
]NPM campaign “cuteboi”
CuteBoi is a software supply chain threat actor which has published 2532 malicious packages. As Checkmarx uncovered, this attacker has demonstrated new techniques that power him with automated NPM account creation.
Read the full media coverage for more information
Request body:
[
{
"name": "zvkenxparfbmksjo",
"type": "npm",
"version": "0.0.69"
}
]Response body:
[
{
"type": "npm",
"name": "zvkenxparfbmksjo",
"version": "0.0.69",
"risks": [
{
"id": "bac4345352aea105a28a87400382a935a4cb8cb1",
"description": "This package executes a crypto mining software\n### About\n\nUsing a dynamic analysis environment (also known as a Sandbox) we can monitor filesystem activity such as newly created files within the lifecycle of the code package.\n\nOnce new files are created, our technology analyzes network and filesystem activity. In case a crypto mining behavior is detected, this risk is shown. \n\n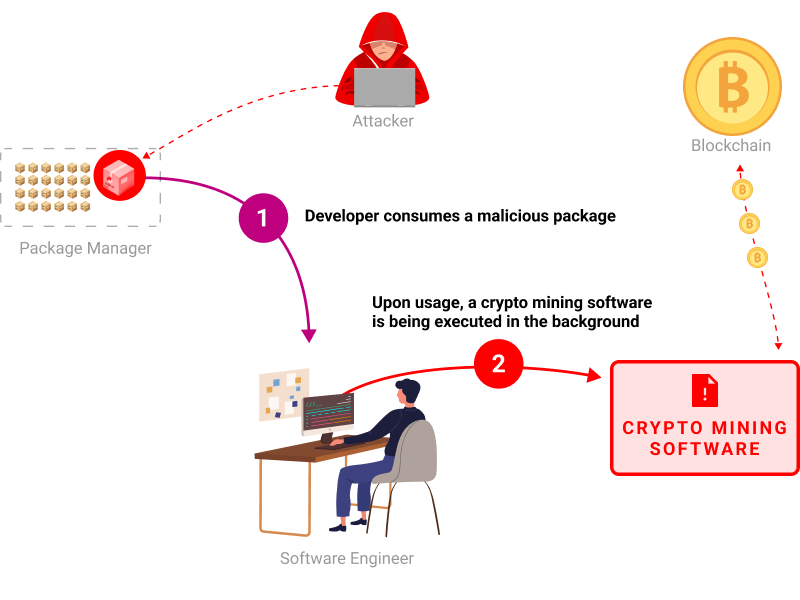",
"title": "Crypto Miner",
"score": 9
},
{
"id": "ceb79020b4d5f8cfd11bf2f8de9972d867a02127",
"description": "This package was manually inspected by a security researcher and flagged as malicious\n### About\n\nClassifying malicious packages is an internal process, analysis is done at scale automatically via multiple engines. Once there's a risk suspicion, this is forwarded to a security researcher for a manual evaluation.\n\nAttackers take advantage of the excessive trust in the open-source ecosystem and launch software supply chain attacks in the form of code packages. \n\nThe risk of having a package with a malicious payload is high. It's a common behavior for most of the malicious payloads to execute itself automatically upon installing or using the package. \n\n\n\nWhile some dependency vulnerabilities have the privilege to be kept as known issue due to risk-management, same does not apply in the case of a malicious package, and it should be removed with the highest priority.",
"title": "Malicious Package",
"score": 10
}
]
}
]